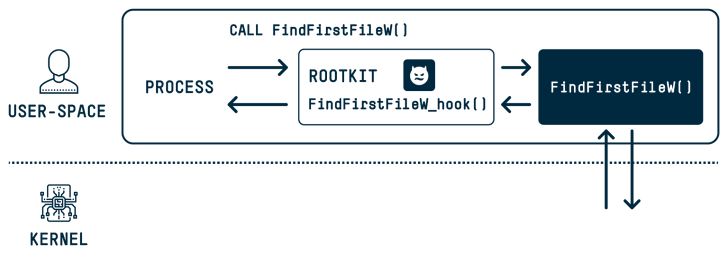
New investigate has discovered that the DOS-to-NT route conversion approach could be exploited by threat actors to attain rootkit-like capabilities to conceal and impersonate files, directories, and processes.
“When a person executes a functionality that has a route argument in Windows, the DOS path at which the file or folder exists is transformed to an NT route,” SafeBreach security researcher Or Yair explained in an assessment, which was presented at the Black Hat Asia conference past 7 days.
“All through this conversion process, a acknowledged issue exists in which the functionality gets rid of trailing dots from any path aspect and any trailing areas from the very last path aspect. This action is done by most person-room APIs in Windows.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
These so-identified as MagicDot paths make it possible for for rootkit-like performance which is obtainable to any unprivileged consumer, who could then weaponize them to carry out a sequence of destructive steps with no owning admin permissions and remain undetected.

They involve the skill to “conceal information and procedures, conceal files in archives, have an effect on prefetch file investigation, make Undertaking Supervisor and Method Explorer consumers feel a malware file was a confirmed executable published by Microsoft, disable Course of action Explorer with a denial of service (DoS) vulnerability, and a lot more.”
The underlying issue inside the DOS-to-NT route conversion procedure has also led to the discovery of four security shortcomings, three of which have given that been resolved by Microsoft –
- An elevation of privilege (EoP) deletion vulnerability that could be employed to delete files with no the needed privileges (to be preset in a long run launch)
- An elevation of privilege (EoP) compose vulnerability that could be employed to produce into information without the necessary privileges by tampering with the restoration approach of a previous version from a quantity shadow duplicate (CVE-2023-32054, CVSS score: 7.3), and
- A distant code execution (RCE) vulnerability that could be applied to make a specially crafted archive, which can lead to code execution when extracting the documents on any spot of the attacker’s selection (CVE-2023-36396, CVSS score: 7.8)
- A denial-of-assistance (DoS) vulnerability impacting the Approach Explorer when launching a system with an executable whose title is 255 figures extensive and is without a file extension (CVE-2023-42757)
“This exploration is the to start with of its form to explore how known issues that show up to be harmless can be exploited to produce vulnerabilities and, ultimately, pose a significant security risk,” Yair explained.
“We believe that the implications are applicable not only to Microsoft Windows, which is the world’s most extensively utilised desktop OS, but also to all software suppliers, most of whom also allow for regarded issues to persist from edition to edition of their software package.”
Observed this posting intriguing? Stick to us on Twitter and LinkedIn to study much more exclusive written content we write-up.
Some sections of this post are sourced from:
thehackernews.com

 Microsoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage
Microsoft Warns: North Korean Hackers Turn to AI-Fueled Cyber Espionage