An unknown threat actor has been connected to an actively in-growth malware toolkit called the “Eternity Project” that allows experienced and amateur cybercriminals buy stealers, clippers, worms, miners, ransomware, and a dispersed denial-of-services (DDoS) bot.
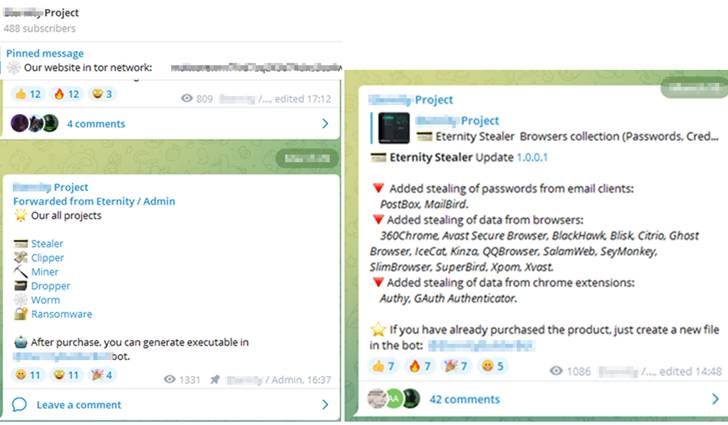
What will make this malware-as-a-services (MaaS) stand out is that other than using a Telegram channel to communicate updates about the hottest attributes, it also employs a Telegram Bot that permits the purchasers to create the binary.
“The [threat actors] provide an option in the Telegram channel to customize the binary characteristics, which provides an productive way to construct binaries without having any dependencies,” scientists from Cyble mentioned in a report posted final week.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
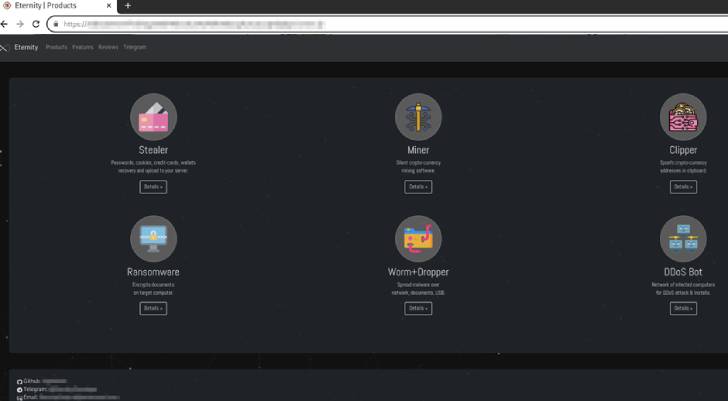
Every of the modules can be leased individually and delivers compensated access to a broad wide range of functions –
- Eternity Stealer ($260 for an annual subscription) – Siphon passwords, cookies, credit history cards, browser cryptocurrency extensions, crypto wallets, VPN consumers, and email applications from a victim’s device and sends them to the Telegram Bot
- Eternity Miner ($90 as an yearly membership) – Abuse the computing resources of a compromised equipment to mine cryptocurrency
- Eternity Clipper ($110) – A crypto-clipping plan that steals cryptocurrency during a transaction by substituting the first wallet address saved in the clipboard with the attacker’s wallet address.
- Eternity Ransomware ($490) – A 130kb ransomware executable to encrypt all of the users’ files until finally a ransom is paid out
- Eternity Worm ($390) – A malware that propagates via USB Drives, nearby network shares, community data files as very well as via spam messages broadcasted on Discord and Telegram.
- Eternity DDoS Bot (N/A) – The attribute is explained to be currently under development.
Cyble pointed out there are indications that the malware authors may perhaps be repurposing existing code relevant to DynamicStealer, which is obtainable on GitHub, and buying and selling it below a new moniker for revenue.
It truly is truly worth noting that Jester Stealer, one more malware that came to light-weight in February 2022 and has since been place to use in phishing attacks from Ukraine, also makes use of the same GitHub repository for downloading TOR proxies, indicating feasible back links among the two risk actors.

The cybersecurity organization also mentioned it “has noticed a important boost in cybercrime as a result of Telegram channels and cybercrime discussion boards where by [threat actors] provide their solutions without any regulation.”
Just last 7 days, BlackBerry exposed the interior workings of a distant obtain trojan named DCRat (aka DarkCrystal RAT) that is readily available for sale at low-priced selling prices on Russian hacking community forums and makes use of a Telegram channel for sharing details about computer software and plugin updates.
Identified this post fascinating? Follow THN on Fb, Twitter and LinkedIn to examine much more special material we put up.
Some parts of this posting are sourced from:
thehackernews.com


 IT admin deletes company’s databases and is jailed for seven years
IT admin deletes company’s databases and is jailed for seven years