A new qualified phishing marketing campaign has zoomed in on a two-factor authentication option referred to as Kavach that’s utilised by Indian federal government officers.
Cybersecurity firm Securonix dubbed the activity STEPPY#KAVACH, attributing it to a menace actor recognised as SideCopy primarily based on tactical overlaps with prior attacks.
“.LNK files are made use of to initiate code execution which ultimately downloads and runs a destructive C# payload, which capabilities as a remote obtain trojan (RAT),” Securonix scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov explained in a new report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
SideCopy, a hacking crew thought to be of Pakistani origin and active considering that at least 2019, is stated to share ties with a different actor known as Clear Tribe (aka APT36 or Mythic Leopard).

It’s also regarded to impersonate attack chains leveraged by SideWinder, a prolific nation-condition team that disproportionately singles out Pakistan-based mostly navy entities, to deploy its have toolset.
That explained, this is not the to start with time Kavach has emerged as a goal for the actor. In July 2021, Cisco Talos specific an espionage procedure that was carried out to steal credentials from Indian govt workforce.
Kavach-themed decoy apps have considering the fact that been co-opted by Clear Tribe in its attacks concentrating on India considering that the get started of the year.
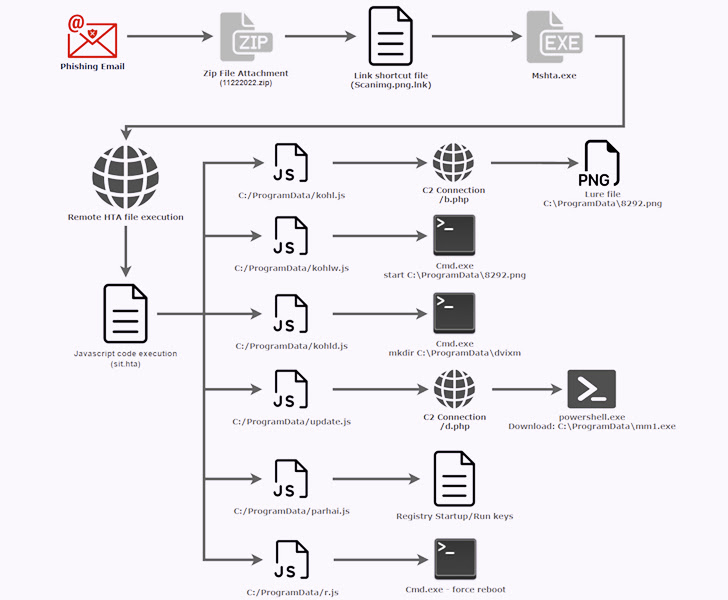
The most up-to-date attack sequence noticed by Securonix in excess of the previous few of weeks entails utilizing phishing email messages to entice opportunity victims into opening a shortcut file (.LNK) to execute a remote .HTA payload employing the mshta.exe Windows utility.
The HTML application, the enterprise said, “was discovered currently being hosted on a probable compromised web-site, nested inside an obscure ‘gallery’ listing built to retail outlet some of the site’s images.”
The compromised web page in problem is incometaxdelhi[.]org, the official web page for India’s Income Tax office pertaining to the Delhi location. The destructive file is no lengthier obtainable on the portal.
In the upcoming stage, working the .HTA file sales opportunities to the execution of obfuscated JavaScript code which is developed to show a decoy image file that functions an announcement from the Indian Ministry of Defence a yr ago in December 2021.
The JavaScript code further more downloads an executable from a distant server, establishes persistence by means of Windows Registry modifications, and reboots the machine to instantly launch the binary put up startup.
The binary file, for its component, capabilities as a backdoor that permits the risk actor to execute commands sent from an attacker-controlled area, fetch and run more payloads, take screenshots, and exfiltrate data files.
The exfiltration part also includes an alternative to specially research for a databases file (“kavach.db”) designed by the Kavach application on the system to retail outlet the credentials.
It really is worth noting that the aforementioned infection chain was disclosed by the MalwareHunterTeam in a sequence of tweets on December 8, 2022, describing the remote obtain trojan as MargulasRAT.
“Based on correlated information from the binary samples acquired of the RAT utilized by the menace actors, this campaign has been heading on in opposition to Indian targets undetected for the past year,” the scientists explained.
Uncovered this write-up exciting? Follow us on Twitter and LinkedIn to read through a lot more exceptional written content we write-up.
Some parts of this posting are sourced from:
thehackernews.com

 Accelerate Your Incident Response
Accelerate Your Incident Response