Menace actors have observed an exploit in a Google Docs comment attribute that utilizes Google’s personal automatic email notification operate to send destructive hyperlinks.
Email security experts Avanan explained it experienced notified Google of the flaw on 3 January just after noticing a spike in usage about December 2021.
The attack consists of hackers using their possess Google accounts to generate a Google Doc, to which they merely invite a target using the comments part with the ‘@’ perform. This routinely sends a notification email to the supposed target’s inbox, informing them that a different consumer has commented on a document and pointed out them. The email is from Google, and so it is tough to tell irrespective of whether the message is malicious.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
However, the remark on the email can be loaded with a destructive backlink for phishing sites or malware, and there seems to be no filtering mechanisms in position, in accordance to Avanan. What is actually extra, the hackers email deal with is not proven in the notification the receiver will only see a identify, producing it quite straightforward to impersonate a victim’s colleagues or friends.
The exploit is quite simple to execute and has been obtainable considering the fact that the Autumn of 2020. Google has attempted to mitigate the problem but are yet to entirely near it off, partly due to the point it needs its personal email company to get the job done.
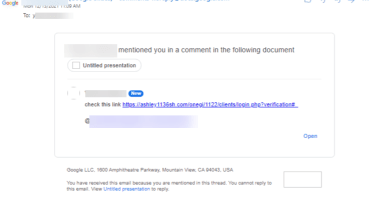
Attackers also usually are not essential to share the doc with their targets, as simply just messaging them is plenty of to induce the email alert. Avanan implies that the very same methods function on Google Slides and other collaboration resources in the Google’s Workspace suite.
Outlook consumers surface to be the favoured targets, according to Avanan, but it is thought the exploit has made use of around 100 Google accounts and has by now attacked 500 inboxes across 30 different organisations.
To safeguard on your own, and your organisation, Avanan suggests steering clear of clicking on inbound links in e-mail, deploying stricter file-sharing rules throughout Google Workspace, and using an Internet security services from a trustworthy vendor, specifically one that capabilities phishing URL protection.
Some areas of this short article are sourced from:
www.itpro.co.uk


 Thousands of Schools Impacted After IT Provider Hit by Ransomware
Thousands of Schools Impacted After IT Provider Hit by Ransomware