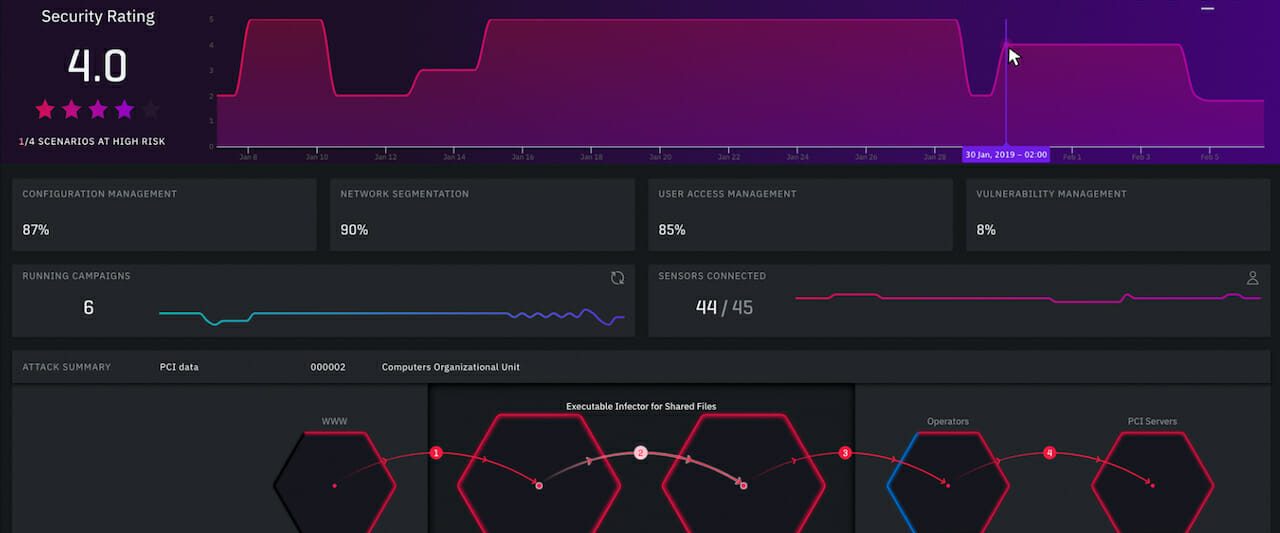
SC Labs usually takes a glance at 7 primary breach and attack products and solutions that produce comprehensive metrics on a company’s security general performance. (Resource: XM Cyber)
Manual security tests just cannot maintain tempo with the threat landscape. Penetration tests will take time and it is costly and labor-intensive. It’s also thoroughly dependent on the abilities of the penetration tester. Even with these inefficiencies, security execs will need to exam security posture and validate controls. Businesses have no way of realizing the efficacy of controls configurations or the general performance of current security investments devoid of knowledge from regular assessments. Furthermore, most compliance criteria now mandate regular security screening as portion of their frameworks.
Breach and assault simulation (BAS) technologies are the resolution to the high-priced venture of guide tests. These resources answer the very same thoughts as guide tests, apart from they do so more inexpensively, regularly and quickly. Security tools are irrelevant if they are misconfigured or underused and the breach and attack simulation (BAS) systems we assessed this month have great prospective for profound return on expense many thanks to the validation presented by way of security controls tests and security instrument screening.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In addition to remaining exceptionally efficient, BAS equipment are incredibly uncomplicated to deploy and manage. They have simple setup and centralized administration to improve the simplicity for security groups and directors alike. Just about every products will come with many out-of-the-box assessments and stories, driving the consumer-friendliness and intuitive implementation. All of the templates are customizable to make certain the overall flexibility important to meet the requires of any business.
A security resource that acts as a hacker continuously attacking a network and its infrastructure might seem dangerous. These equipment are risk-free and provide valuable insight into vulnerabilities and assault vectors without having compromising manufacturing environments. These solutions take security assessments a step further more to give remediation strategies, prioritizations and guidelines to guide analysts with danger reaction. The broad use instances and probable attain from these alternatives helps make picking to implement them a no-brainer. They capitalize on existing security investments and assure that an organization’s digital estate and human assets are secure.
Group Opener
This month we revisited the however rising house of BAS technologies. These goods have gone through a good deal of maturity and advancement in excess of the past year and are continuing the development in the direction of mainstreaming and reworking the security space. Security testing stays crucial for preserving a powerful security posture and fantastic security hygiene. Misconfigured controls and underused tools are commonplace throughout industries and security tests offers a way to mitigate these vulnerabilities.
The pricey and time-consuming mother nature of the previous go-to security testing methodologies have and go on to get outperformed by the chopping-edge technology breach and assault simulation instruments give, rendering manual controls screening and penetration tests a lot more out of date than ever. Reoccurring assessments and validation are not feasible with guide testing, notoriously pricey and time-consuming. The threat landscape we deal with today needs security screening which is ongoing and repetitive. This need coupled with the obsolescence of manual penetration screening paves the way for breach and assault simulators.
BAS technology takes advantage of automation to push ongoing security management testing, exposing and identifying vulnerabilities and misconfigurations. Analysts could use this data to get more out of their present security tools and validate environments are correctly configured. You might believe of these solutions as a personalized trainer for your security ecosystem as they fortify what’s by now there and discover weaknesses, offering tips on how to bolster people vulnerabilities and mitigate threats. We proceed to see these solutions progressively employ purple workforce capabilities with extensive remediation advice to streamline the detection and response method.
In addition to the breach and attack simulation use scenarios that focus on controls tests and item tests, these goods also examination the human component in businesses. Staff members screening is a essential part of security. An corporation could have an airtight natural environment with all the leading-of-the-line equipment money can purchase. None of that indicates anything at all if the human component opens the group to attack and exploitation. These products and solutions produce the perception important for security teams to be certain absolutely everyone on the workforce abides by the protocols in put.
The BAS applications we assessed this month continue on to solidify their put within just the cybersecurity realm and competently shore up human and technological vulnerabilities when giving a considerable return on expenditure of all security implementations. Security gurus now think about these products and solutions a staple for any security toolset and will continue on to change the landscape and the way security groups work.
August Testimonials:
AttackIQ System v2.1
Cymulate Breach and Assault Simulation System 3.30.16
The Picus Security Validation System 3113
SafeBreach Platform
Sophos Phish Risk
Spirent Communications CyberFlood Facts Breach Assessment v2.02
XM Cyber 1.35

 Feds arrest teen Twitter hack chief, accomplices
Feds arrest teen Twitter hack chief, accomplices