Danger actors involved with the Roaming Mantis attack marketing campaign have been noticed offering an up-to-date variant of their patent mobile malware recognised as Wroba to infiltrate Wi-Fi routers and undertake Domain Title Process (DNS) hijacking.
Kaspersky, which carried out an examination of the destructive artifact, mentioned the feature is intended to goal unique Wi-Fi routers situated in South Korea.
Roaming Mantis, also recognized as Shaoye, is a long-jogging financially motivated operation that targets Android smartphone consumers with malware able of stealing financial institution account qualifications as effectively as harvesting other kinds of delicate data.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Despite the fact that mostly concentrating on the Asian location given that 2018, the hacking crew was detected expanding its sufferer range to incorporate France and Germany for the initially time in early 2022 by camouflaging the malware as the Google Chrome web browser software.
The attacks leverage smishing messages as the first intrusion vector of decision to produce a booby-trapped URL that either delivers a destructive APK or redirects the sufferer to phishing webpages centered on the functioning procedure put in in the mobile products.
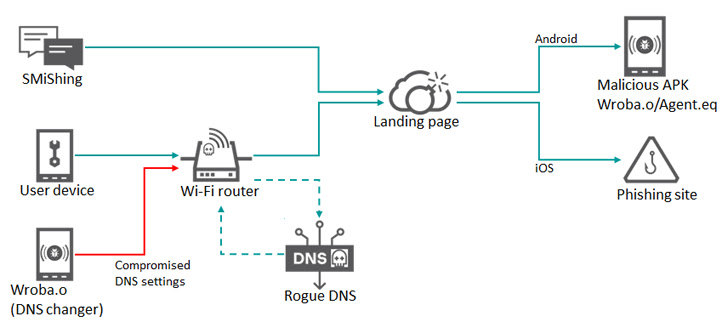
Alternatively, some compromises have also leveraged Wi-Fi routers as a means to just take unsuspecting people to a faux landing web page by making use of a procedure identified as DNS hijacking, in which DNS queries are manipulated in order to redirect targets to bogus web sites.
Regardless of the method applied, the intrusions pave the way for the deployment of a malware dubbed Wroba (aka MoqHao and XLoader) that is capable of carrying out a slew of nefarious things to do.
The most current update to Wroba, for each the Russian cybersecurity enterprise, includes a DNS changer functionality that is engineered to detect particular routers centered on their design quantities and poison their DNS options.
“The new DNS changer operation can control all product communications employing the compromised Wi-Fi router, these types of as redirecting to malicious hosts and disabling updates of security solutions,” Kaspersky researcher Suguru Ishimaru said.
The underlying concept is to bring about units connected to the breached Wi-Fi router to be redirected to web internet pages controlled by the threat actor for even more exploitation. Offered that some of these internet pages provide the Wroba malware, the attack chain correctly creates a steady stream of “bots” that can be weaponized to crack into nutritious Wi-Fi routers.
It really is noteworthy that the DNS changer application is solely applied in South Korea. On the other hand, the Wroba malware in alone has been noticed focusing on victims in Austria, France, Germany, India, Japan, Malaysia, Taiwan, Turkey, and the U.S. by way of smishing.
“Customers with infected Android products that link to free of charge or public Wi-Fi networks may well unfold the malware to other products on the network if the Wi-Fi network they are connected to is vulnerable,” the researcher mentioned.
Identified this short article fascinating? Abide by us on Twitter and LinkedIn to study far more exceptional content material we post.
Some parts of this article are sourced from:
thehackernews.com


 WhatsApp Hit with €5.5m fine for GDPR Violations
WhatsApp Hit with €5.5m fine for GDPR Violations