A phishing-as-a-services (PhaaS) system regarded as Robin Banking companies has relocated its attack infrastructure to DDoS-Guard, a Russian provider of bulletproof hosting products and services.
The change will come soon after “Cloudflare disassociated Robin Banks phishing infrastructure from its companies, triggering a multi-day disruption to operations,” in accordance to a report from cybersecurity company IronNet.
Robin Banking institutions was initially documented in July 2022 when the platform’s qualities to offer all set-designed phishing kits to felony actors were exposed, creating it feasible to steal the money information and facts of clients of well-known banks and other on the internet companies.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It was also located to prompt people to enter Google and Microsoft qualifications on rogue landing webpages, suggesting an attempt on element of the malware authors to monetize initial access to corporate networks for publish-exploitation routines these kinds of as espionage and ransomware.
In the latest months, Cloudflare’s decision to blocklist its infrastructure in the wake of public disclosure has prompted the Robin Financial institutions actor to move its frontend and backend to DDoS-Guard, which has in the previous hosted the alt-tech social network Parler and the infamous Kiwi Farms.
“This hosting company is also notorious in not complying with takedown requests, hence generating it a lot more pleasing in the eyes of risk actors,” the scientists famous.
Main between the new updates launched is a cookie-stealing functionality, in what is viewed as an try to provide a broader clientele this sort of as sophisticated persistent danger (APT) groups that are wanting to compromise distinct organization environments. It is really available for $1,500 for each thirty day period.
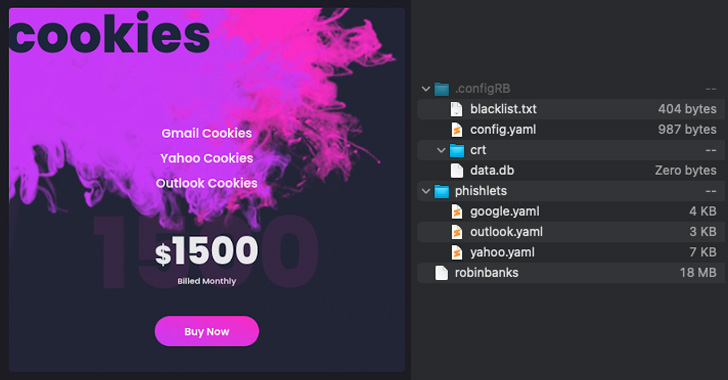
This is accomplished by reusing code from evilginx2, an open source adversary-in-the-middle (AiTM) attack framework used to steal qualifications and session cookies from Google, Yahoo, and Microsoft Outlook even on accounts that have multi-factor authentication (MFA) enabled.
Robin Banking institutions is also stated to have integrated a new security evaluate that involves its clients to change on two-factor authentication (2FA) to look at the stolen facts by way of the services, or, alternatively, receive the data by means of a Telegram bot.
Yet another notable function is its use of Adspect, an advertisement fraud detection company, to redirect targets of phishing strategies to rogue internet websites, when main scanners and undesired visitors to benign internet websites to slip less than the radar.

The results are just the newest in a sequence of new PhaaS products and services that have emerged in the risk landscape, such as Frappo, EvilProxy, and Caffeine, making cybercrime additional available to beginner and seasoned bad actors alike.
What is far more, the advancements also illustrate the expanding will need for risk actors to depend on diverse procedures this kind of as AiTM and prompt bombing (aka MFA exhaustion) – as not long ago noticed in the case of Uber – to circumvent security actions and obtain first obtain.
“The infrastructure of the Robin Banking companies phishing kit relies seriously on open-supply code and off-the-shelf tooling, serving as a primary illustration of the decreasing barrier-to-entry to not only conducting phishing attacks, but also to creating a PhaaS system for others to use,” the researchers said.
Observed this article fascinating? Adhere to THN on Fb, Twitter and LinkedIn to read through additional exceptional content material we put up.
Some sections of this post are sourced from:
thehackernews.com

 Researchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer
Researchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer