The threat actor at the rear of a distant entry trojan called RomCom RAT has been observed focusing on Ukrainian armed service establishments as part of a new spear-phishing campaign that commenced on Oct 21, 2022.
The growth marks a change in the attacker’s modus operandi, which has been formerly attributed to spoofing genuine applications like Innovative IP Scanner and pdfFiller to drop backdoors on compromised devices.
“The original ‘Advanced IP Scanner’ campaign occurred on July 23, 2022,” the BlackBerry exploration and intelligence staff stated. “When the sufferer installs a Trojanized bundle, it drops RomCom RAT to the system.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Though previous iterations of the campaign concerned the use of trojanized Innovative IP Scanner, the unidentified adversarial collective has given that switched to pdfFiller as of Oct 20, indicating an lively endeavor on aspect of the adversary to refine techniques and thwart detection.
These lookalike sites host a rogue installer package that success in the deployment of the RomCom RAT, which is able of harvesting facts and capturing screenshots, all of which is exported to a remote server.
The adversary’s most recent exercise directed towards the Ukrainian armed forces is a departure in that it employs a phishing email with an embedded website link as an initial an infection vector, foremost to a fake internet site dropping the next stage downloader.

This downloader, signed using a legitimate electronic certificate from “Blythe Consulting sp. z o.o.” for an further layer of evasion, is then applied to extract and run the RomCom RAT malware. BlackBerry explained the very same signer is utilised by the legitimate edition of pdfFiller.
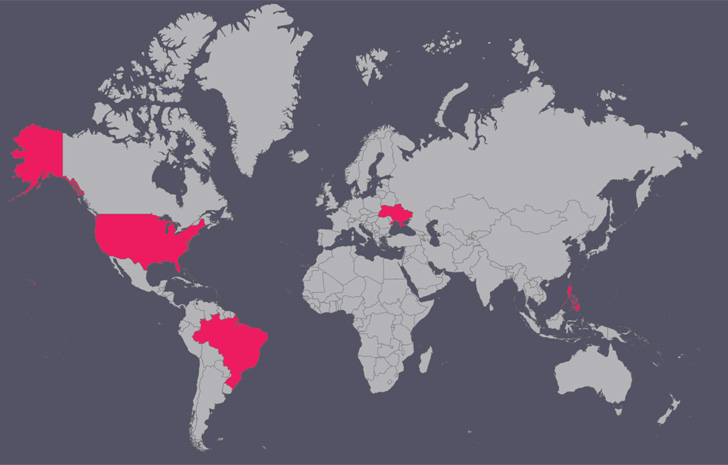
Other than the Ukrainian military services, other targets of the marketing campaign include IT businesses, food items brokers, and food stuff manufacturing entities in the U.S., Brazil, and the Philippines.
“This marketing campaign is a superior illustration of the blurred line concerning cybercrime-motivated danger actors and focused attack risk actors,” Dmitry Bestuzhev, danger researcher at BlackBerry, instructed The Hacker News.
“In the earlier, each groups acted independently, relying on various tooling. Today, qualified attack risk actors depend extra on common tooling, making attribution more challenging.”
Uncovered this article intriguing? Observe THN on Facebook, Twitter and LinkedIn to browse extra unique articles we article.
Some elements of this posting are sourced from:
thehackernews.com


 See Tickets admits it took nine months to remove malicious code from site
See Tickets admits it took nine months to remove malicious code from site