Cybersecurity scientists have detailed the techniques of a “increasing” cybercriminal gang called “Study The Handbook” (RTM) Locker that features as a personal ransomware-as-a-assistance (RaaS) supplier and carries out opportunistic attacks to deliver illicit gain.
“The ‘Read The Manual’ Locker gang employs affiliates to ransom victims, all of whom are pressured to abide by the gang’s demanding procedures,” cybersecurity organization Trellix said in a report shared with The Hacker News.
“The business enterprise-like established up of the group, the place affiliates are required to stay energetic or notify the gang of their go away, reveals the organizational maturity of the group, as has also been observed in other groups, these as Conti.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
RTM, 1st documented by ESET in February 2017, begun off in 2015 as a banking malware concentrating on companies in Russia by using travel-by downloads, spam, and phishing emails. Attack chains mounted by the group have considering the fact that evolved to deploy a ransomware payload on compromised hosts.
In March 2021, the Russian-talking team was attributed to an extortion and blackmail campaign that deployed a trifecta of threats, like a financial trojan, reputable distant access tools, and a ransomware pressure called Quoter.
Trellix informed The Hacker News that there is no relationship concerning Quoter and the RTM Locker ransomware executable utilised in the latest attacks.
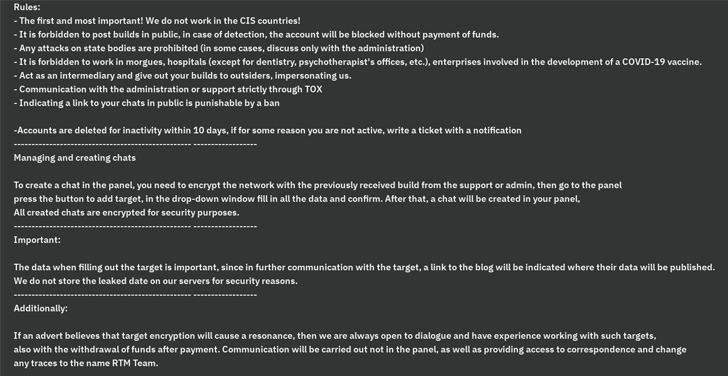
A important trait of the danger actor is its capacity to operate less than the shadows by intentionally avoiding significant-profile targets that could attract consideration to its functions. To that close, CIS nations, as effectively as morgues, hospitals, COVID-19 vaccine-related corporations, critical infrastructure, regulation enforcement, and other popular corporations are off-limitations for the group.
“The RTM gang’s purpose is to entice as small notice as feasible, which is wherever the regulations support them to avoid hitting significant-value targets,” security researcher Max Kersten reported. “Their management of affiliates to attain that purpose calls for some level of sophistication, nevertheless it really is not a high amount for each se.”
Impending WEBINARMaster the Art of Dark Web Intelligence Gathering
Find out the art of extracting menace intelligence from the dark web – Be a part of this qualified-led webinar!
Conserve My Seat!
RTM Locker malware builds are bound by demanding mandates that forbid affiliates from leaking the samples, or else risk struggling with a ban. Amongst the other guidelines laid out is a clause that locks out affiliate marketers need to they remain inactive for 10 times sans a notification upfront.
“The exertion the gang set into staying away from drawing attention was the most unusual,” Kersten explained. “The affiliates need to have to be lively as well, building it more durable for scientists to infiltrate the gang. All in all, the gang’s specific endeavours in this region are bigger than ordinarily observed as opposed to other ransomware groups.”
It is suspected that the locker is executed on networks that are by now under the adversary’s command, indicating that the techniques could have been compromised by other means, these types of as phishing attacks, malspam, or the exploitation of internet-uncovered susceptible servers.
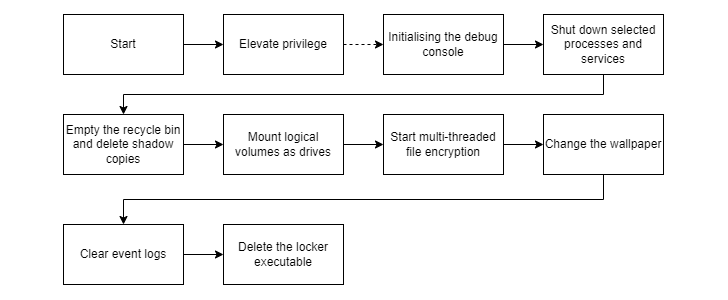
The danger actor, like other RaaS teams, employs extortion techniques to compel victims into shelling out up. The payload, for its section, is capable of elevating privileges, terminating antivirus and backup expert services, and deleting shadow copies right before commencing its encryption method.
It is also developed to empty the Recycle Bin to prevent recovery, modify the wallpaper, wipe celebration logs, and execute a shell command that self-deletes the locker as a past phase.
The results propose that cybercrime groups will continue on to “undertake new techniques and strategies to stay clear of the headlines and aid them fly beneath the radar of researchers and legislation enforcement alike,” Kersten famous.
Observed this article appealing? Stick to us on Twitter and LinkedIn to study much more distinctive content material we post.
Some pieces of this article are sourced from:
thehackernews.com

 Over 20,000 Iowa Medicaid Members Affected By Data Breach
Over 20,000 Iowa Medicaid Members Affected By Data Breach