Ukraine has appear less than a refreshing onslaught of ransomware attacks that mirror past intrusions attributed to the Russia-centered Sandworm country-condition team.
Slovak cybersecurity business ESET, which dubbed the new ransomware strain RansomBoggs, stated the attacks versus various Ukrainian entities ended up very first detected on November 21, 2022.
“Although the malware published in .NET is new, its deployment is comparable to former attacks attributed to Sandworm,” the corporation mentioned in a sequence of tweets Friday.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The growth arrives as the Sandworm actor, tracked by Microsoft as Iridium, was implicated for a established of attacks aimed at transportation and logistics sectors in Ukraine and Poland with one more ransomware pressure identified as Prestige in Oct 2022.
The RansomBoggs activity is said to make use of a PowerShell script to distribute the ransomware, with the latter “pretty much identical” to the one particular employed in the Industroyer2 malware attacks that arrived to light in April.
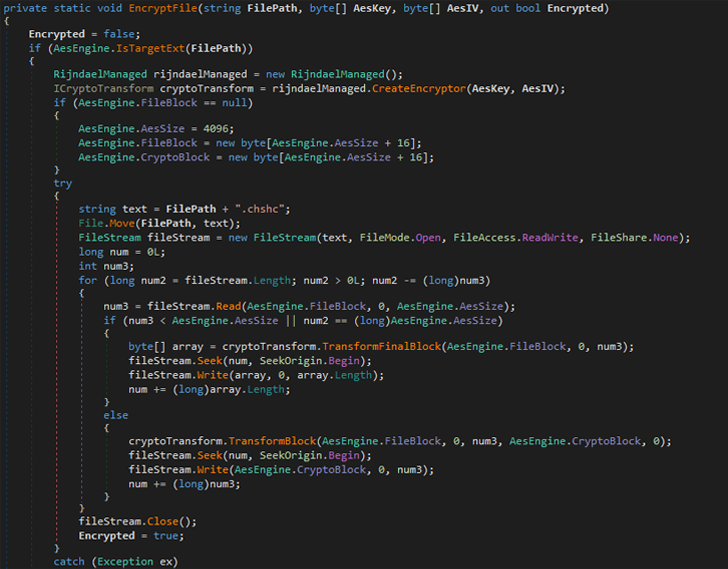
In accordance to the Laptop or computer Unexpected emergency Reaction Workforce of Ukraine (CERT-UA), the PowerShell script, named POWERGAP, was leveraged to deploy a data wiper malware identified as CaddyWiper making use of a loader dubbed ArguePatch (aka AprilAxe).
ESET’s evaluation of the new ransomware demonstrates that it generates a randomly created vital and encrypts data files working with AES-256 in CBC mode and appends the “.chsch” file extension.
Sandworm, an elite adversarial hacking team in Russia’s GRU navy intelligence agency, has a notorious observe record of hanging critical infrastructure over the many years.
The menace actor has been joined to the NotPetya cyberattacks towards hospitals and healthcare facilities in 2017 and the damaging assaults from the Ukrainian electrical electric power grid in 2015 and 2016.
Discovered this post exciting? Adhere to THN on Fb, Twitter and LinkedIn to study much more exclusive articles we article.
Some pieces of this report are sourced from:
thehackernews.com

 ConnectWise Fixes XSS Vulnerability that Could Lead to Remote Code Execution
ConnectWise Fixes XSS Vulnerability that Could Lead to Remote Code Execution