The Russia-linked APT29 (aka Cozy Bear) threat actor has been attributed to an ongoing cyber espionage marketing campaign focusing on international ministries and diplomatic entities located in NATO member states, the European Union, and Africa.
According to Poland’s Military services Counterintelligence Services and the CERT Polska group, the observed exercise shares tactical overlaps with a cluster tracked by Microsoft as Nobelium, which is known for its high-profile attack on SolarWinds in 2020.
Nobelium’s operations have been attributed to Russia’s International Intelligence Service (SVR), an organization which is tasked with protecting “people, culture, and the condition from international threats.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
That reported, the campaign represents an evolution of the Kremlin-backed hacking group’s tactics, indicating persistent makes an attempt at strengthening its cyber weaponry to infiltrate sufferer units for intelligence collecting.
“New instruments have been employed at the very same time and independently of each other, or changing those people whose efficiency had declined, permitting the actor to maintain a steady, higher operational tempo,” the businesses claimed.
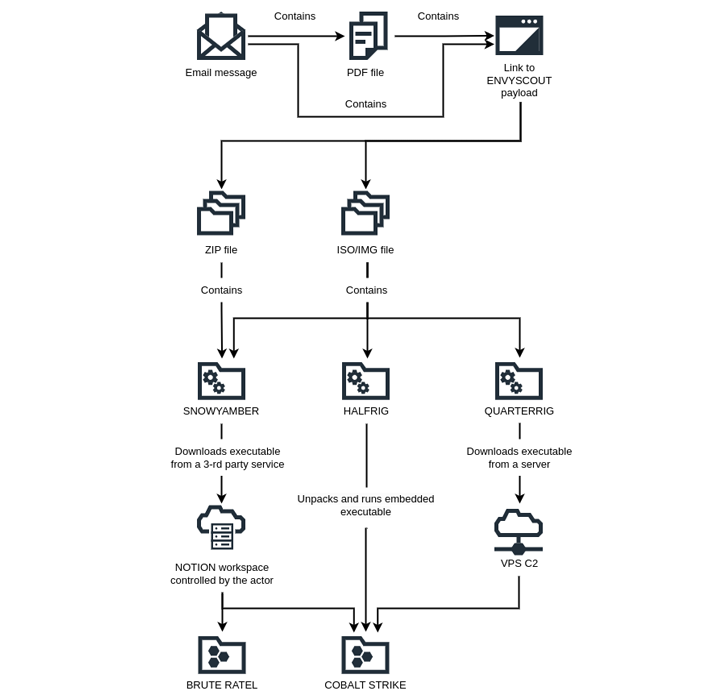
The attacks start with spear-phishing e-mail impersonating European embassies that purpose to entice specific diplomats into opening malware-laced attachments beneath the guise of an invitation or a conference.
Embedded in just the PDF attachment is a booby-trapped URL that prospects to the deployment of an HTML dropper referred to as EnvyScout (aka ROOTSAW), which is then applied as a conduit to supply three earlier unfamiliar strains SNOWYAMBER, HALFRIG, and QUARTERRIG.
Upcoming WEBINARMaster the Art of Dark Web Intelligence Accumulating
Understand the art of extracting threat intelligence from the dark web – Be part of this skilled-led webinar!
Help you save My Seat!
SNOWYAMBER, also referred to as GraphicalNeutrino by Recorded Upcoming, leverages the Idea notice-using provider for command-and-regulate (C2) and downloading more payloads this kind of as Brute Ratel.
QUARTERRIG also features as a downloader able of retrieving an executable from an actor-managed server. HALFRIG, on the other hand, acts as a loader to launch the Cobalt Strike publish-exploitation toolkit contained inside of it.
It truly is value noting that the disclosure dovetails with new findings from BlackBerry, which thorough a Nobelium campaign concentrating on European Union nations, with a particular emphasis on companies that are “aiding Ukrainian citizens fleeing the state, and furnishing assist to the government of Ukraine.”
Observed this post interesting? Stick to us on Twitter and LinkedIn to read through extra unique information we article.
Some pieces of this short article are sourced from:
thehackernews.com


 UK Education Sector Suffered Most from Ransomware in 2022
UK Education Sector Suffered Most from Ransomware in 2022