The data wiping malware called AcidPour may perhaps have been deployed in attacks concentrating on four telecom suppliers in Ukraine, new conclusions from SentinelOne display.
The cybersecurity agency also confirmed connections among the malware and AcidRain, tying it to danger exercise clusters involved with Russian navy intelligence.
“AcidPour’s expanded capabilities would empower it to greater disable embedded devices which includes networking, IoT, significant storage (RAIDs), and maybe ICS units working Linux x86 distributions,” security researchers Juan Andres Guerrero-Saade and Tom Hegel mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
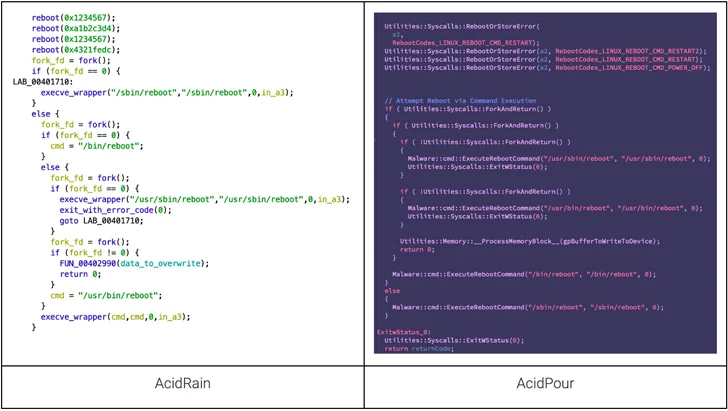
AcidPour is a variant of AcidRain, a wiper that was made use of to render Viasat KA-SAT modems operable at the onset of the Russo-Ukrainian war in early 2022 and cripple Ukraine’s military services communications.

It also builds on the latter’s attributes, although targeting Linux methods operating on x86 architecture. AcidRain, on the other hand, is compiled for MIPS architecture.
Where by AcidRain was extra generic, AcidPour incorporates logic to focus on embedded products, Storage Region Networks (SANs), Network Hooked up Storage (NAS) appliances, and dedicated RAID arrays.
That explained, both equally the strains overlap when it arrives to the use of the reboot calls and the technique used for recursive listing wiping. Also equivalent is the IOCTLs-primarily based system-wiping mechanism that also shares commonalities with yet another malware connected to Sandworm identified as VPNFilter.
“One of the most interesting elements of AcidPour is its coding style, reminiscent of the pragmatic CaddyWiper broadly utilized towards Ukrainian targets along with noteworthy malware like Industroyer 2,” the researchers explained.
The C-centered malware will come with a self-delete functionality that overwrites alone on disk at the commencing of its execution, when also employing an alternate wiping approach relying on the device form.
AcidPour has been attributed to a hacking crew tracked as UAC-0165, which is linked with Sandworm and has a track document of hanging Ukrainian critical infrastructure.
The Laptop Crisis Response Staff of Ukraine (CERT-UA), in October 2023, implicated the adversary to attacks targeting at least 11 telecommunication provider companies in the state between May perhaps and September of previous yr.

“[AcidPour] could have been used in 2023,” Hegel advised The Hacker News. “It can be most likely the actor has manufactured use of AcidRain/AcidPour linked tooling continuously throughout the war. A hole in this viewpoint speaks to the level of perception the general public frequently has to cyber intrusions – usually fairly constrained and incomplete.”
The ties to Sandworm are additional bolstered by the point that a menace actor regarded as Solntsepyok (aka Solntsepek or SolntsepekZ) claimed to have infiltrated four diverse telecommunication operators in Ukraine and disrupted their services on March 13, 2024, 3 days prior to the discovery of AcidPour.
Solntsepyok, in accordance to the Condition Unique Communications Provider of Ukraine (SSSCIP), is a Russian innovative persistent risk (APT) with probably ties to the Key Directorate of the Typical Staff of the Armed Forces of the Russian Federation (GRU), which also operates Sandworm.
It can be well worth pointing out that Solntsepyok has also been accused of hacking into Kyivstar’s programs as early as May well 2023. The breach came to gentle in late December.
When it really is currently not crystal clear if AcidPour was applied in the most recent established of attacks, the discovery implies that risk actors are constantly refining their techniques to stage destructive assaults and inflict major operational impression.
“This development reveals not only a refinement in the technological abilities of these threat actors but also their calculated approach to choose targets that increase comply with-on results, disrupting critical infrastructure and communications,” the scientists claimed.
Found this write-up attention-grabbing? Abide by us on Twitter and LinkedIn to browse far more special material we article.
Some elements of this write-up are sourced from:
thehackernews.com


 Russia Hackers Using TinyTurla-NG to Breach European NGO’s Systems
Russia Hackers Using TinyTurla-NG to Breach European NGO’s Systems