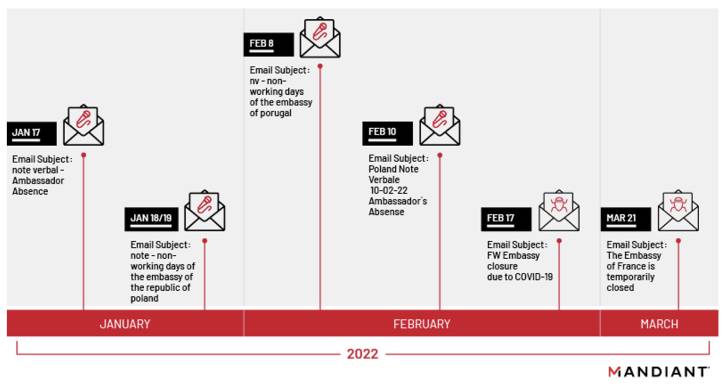
A Russian state-sponsored menace actor has been observed focusing on diplomatic and authorities entities as portion of a sequence of phishing campaigns commencing on January 17, 2022.
Risk intelligence and incident reaction business Mandiant attributed the attacks to a hacking team tracked as APT29 (aka Cozy Bear), with some established of the functions involved with the crew assigned the moniker Nobelium (aka UNC2452/2652).
“This most recent wave of spear phishing showcases APT29’s enduring interests in getting diplomatic and overseas policy info from governments close to the world,” the Mandiant reported in a report printed past 7 days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The preliminary obtain is explained to have been aided by way of spear-phishing e-mail masquerading as administrative notices, working with legitimate but compromised email addresses from other diplomatic entities.
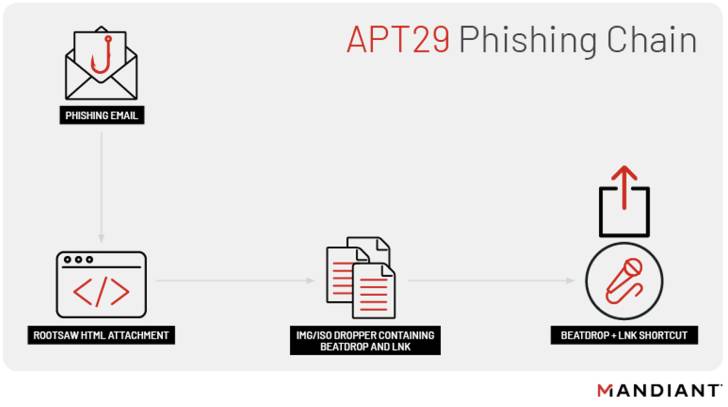
These email messages consist of an HTML dropper attachment called ROOTSAW (aka EnvyScout) that, when opened, triggers an an infection sequence that delivers and executes a downloader dubbed BEATDROP on a concentrate on process.
Prepared in C, BEATDROP is intended to retrieve upcoming-stage malware from a remote command-and-command (C2) server. It achieves this by abusing Atlassian’s Trello assistance to retail store sufferer details and fetch AES-encrypted shellcode payloads to be executed.
Also utilized by APT29 is a instrument named BOOMMIC (aka VaporRage) to build a foothold within just the ecosystem, adopted by escalating their privileges inside the compromised network for lateral motion and substantial reconnaissance of hosts.
What’s more, a subsequent operational shift observed in February 2022 noticed the risk actor pivoting absent from BEATDROP in favor of a C++-centered loader referred to as BEACON, probably reflecting the group’s skill to periodically change their TTPs to continue to be under the radar.
BEACON, programmed in C or C++, is portion of the Cobalt Strike framework that facilitates arbitrary command execution, file transfer, and other backdoor capabilities these as capturing screenshots and keylogging.
The development follows the cybersecurity company’s selection to merge the uncategorized cluster UNC2452 into APT29, while noting the very refined group’s propensity for evolving and refining its complex tradecraft to obfuscate activity and restrict its electronic footprint to stay away from detection.

Nobelium, notably, breached many enterprises by indicates of a supply chain attack in which the adversary accessed and tampered with SolarWinds resource code, and used the vendor’s reputable application updates to distribute the malware to consumer systems.
“The consistent and continual improvement in TTPs speaks to its disciplined nature and commitment to stealthy functions and persistence,” Mandiant reported, characterizing APT29 as an “evolving, disciplined, and really expert menace actor that operates with a heightened degree of operational security (OPSEC) for the functions of intelligence selection.”
The conclusions also coincide with a specific report from Microsoft, which observed Nobelium making an attempt to breach IT firms serving authorities shoppers in NATO member states, utilizing the entry to siphon details from Western international policy companies.
Located this report fascinating? Adhere to THN on Facebook, Twitter and LinkedIn to read more unique content we put up.
Some pieces of this report are sourced from:
thehackernews.com


 Google Releases First Developer Preview of Privacy Sandbox on Android 13
Google Releases First Developer Preview of Privacy Sandbox on Android 13