When SaaS purposes started out expanding in attractiveness, it was unclear who was liable for securing the data. Today, most security and IT teams understand the shared obligation model, in which the SaaS seller is responsible for securing the software, when the corporation is liable for securing their data.
What is much murkier, on the other hand, is the place the data duty lies on the organization’s side. For significant organizations, this is a specifically hard problem. They keep terabytes of customer info, worker information, money data, strategic facts, and other sensitive data information on the internet.
SaaS knowledge breaches and SaaS ransomware attacks can lead to the decline or general public exposure of that knowledge. Based on the industry, some firms could face stiff regulatory penalties for details breaches on best of the detrimental PR and loss of faith these breaches bring with them.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Finding the proper security product is the to start with action right before deploying any style of SSPM or other SaaS security resolution.
Learn how Adaptive Shield’s SSPM option can support protected your SaaS stack.
Getting to Know the Players
There are various distinctive teams of players involved in the SaaS security ecosystem.
SaaS Application Proprietors – When organization models subscribe to SaaS software package, somebody from in the company unit is typically dependable for setting up and onboarding the software. Whilst they may possibly have some enable from IT, the application is their obligation.
They opt for options and configurations that align with their business demands, incorporate end users, and get to perform. SaaS Application Entrepreneurs figure out the want for knowledge security, but it isn’t really their obligation or something they know really a great deal about. Some mistakenly believe that info security is only the accountability of the SaaS vendor.
Central IT – In most massive businesses, Central IT is dependable for matters like infrastructure, components, and passwords. They deal with IDP and servers, as nicely as oversee help desk routines. SaaS programs usually do not fall under their immediate area.
Central IT is a lot more common with security needs than the ordinary staff, but it isn’t their most important issue. Nonetheless, it is critical to retain in brain that they are not security industry experts.
Security Groups – The security team is the natural match for utilizing security controls and oversight. They are tasked with producing and utilizing a cybersecurity policy that applies throughout the corporation.
On the other hand, they have quite a few issues inhibiting their skill to secure programs. For starters, they are normally unaware of SaaS apps that are becoming employed by the company. Even for programs that they are knowledgeable of, they lack access to the configuration panels inside of the SaaS stack, and aren’t constantly mindful of the special security factors connected with each and every software. Those people are controlled and managed by the SaaS Application Homeowners and Central IT.
GRC Groups – Compliance and governance teams are tasked with making sure that all IT satisfies particular security standards. Though they do not perform a distinct part in securing corporate property, they do have oversight and need to determine whether the firm is living up to its compliance obligations.
SaaS Vendor – When the SaaS vendor is absolved from any duty to protected the data, they are the staff that built the security apparatus for the SaaS software, and have a deep understanding of their application and its security abilities.
Defining Roles and Duties
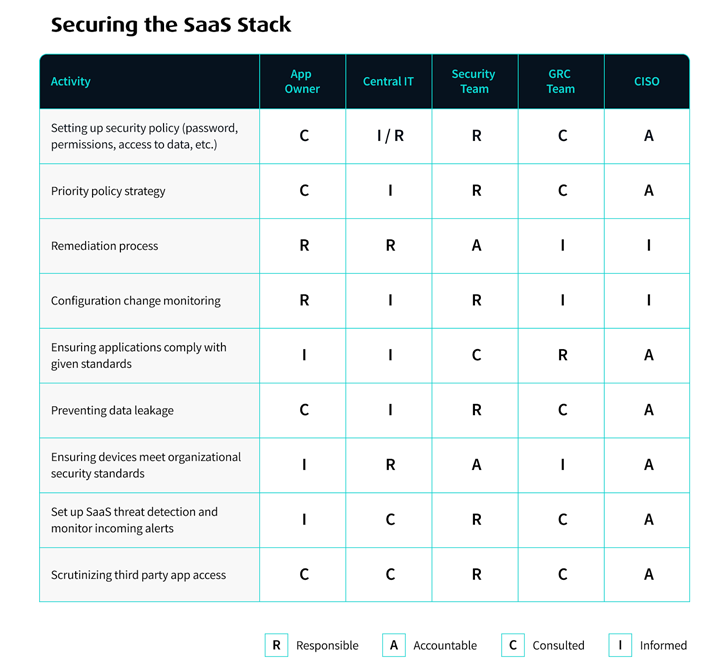
Securing the whole SaaS stack calls for near collaboration between the security specialists and those people running and functioning their personal SaaS purposes. We created this RACI chart to share our perspective on the departments that are responsible, accountable, consulted, and educated for the diverse tasks associated in securing SaaS data.
Bear in thoughts, this table is not 1 measurement fits all, but a framework centered on the way we see several companies managing their SaaS security roles. It ought to be tailored to the demands of your group.
Study extra about SaaS consumer roles and tasks. Timetable a demo nowadays.
Building the Appropriate Infrastructure
Developing the RACI matrix is significant, but with no the appropriate instruments in place, applying security obligations turns into a in close proximity to-unachievable endeavor.
Companies need a SaaS Security platform that facilitates crystal clear interaction amongst the security team and application proprietors. This interaction should really include things like alerts when misconfigurations arise that weaken the person app’s security posture and when threats are detected by its IAM governance tools.
Interaction must be channel agnostic, so people can receive messages and alerts about email, Slack, Splunk, or the messaging platform of preference. All security-similar notifications should also consist of remediation actions, providing application entrepreneurs and central IT with a clear understanding of the ways expected to mitigate the risk.
In the system, each and every owner should really have visibility and obtain to the application or apps under their manage. They should really be capable to see the status of their security options, their security score, their users, third-party SaaS applications that are connected to their app, and the products being utilized to access their SaaS app.
App owners and central IT ought to also have the capabilities to dismiss a security alert owing, either simply because it doesn’t utilize or because of to company demands, and check with with the security group on risk.
Securing SaaS Data Takes a Cross-Workforce Exertion
It really is quick for SaaS application security to be overlooked. It sits outside the watch of the security staff and is managed by proficient professionals whose obligations never include things like security.
On the other hand, the details contained within just the SaaS purposes are normally the lifeblood of an organization, and failure to secure the data can have disastrous outcomes.
Thoroughly safeguarding the data from publicity calls for a cross-team work and dedication from all get-togethers involved, as very well as a innovative SSPM system designed for SaaS in the authentic globe.
Discover how an SSPM can assistance protected your info. E-book a demo.
Observed this post appealing? Stick to us on Twitter and LinkedIn to study much more unique information we write-up.
Some components of this post are sourced from:
thehackernews.com

 OpenSSH Releases Patch for New Pre-Auth Double Free Vulnerability
OpenSSH Releases Patch for New Pre-Auth Double Free Vulnerability