Samsung has announced a new attribute named Concept Guard that arrives with safeguards to shield buyers from malware and adware through what is referred to as zero-click attacks.
The South Korean chaebol said the alternative “preemptively” secures users’ equipment by “limiting publicity to invisible threats disguised as impression attachments.”
The security function, obtainable on Samsung Messages and Google Messages, is at this time restricted to the Samsung Galaxy S23 series, with plans to grow it to other Galaxy smartphones and tablets later this calendar year that are working on Just one UI 5.1 or greater.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Zero-click attacks are very-focused and innovative attacks that exploit previously not known flaws (i.e., zero-days) in computer software to result in execution of destructive code without necessitating any consumer interaction.
Unlike classic strategies of remotely exploiting a product whereby danger actors count on phishing strategies to trick a person into clicking on a destructive connection or opening an rogue file, such attacks circumvent the require for social engineering solely and deliver an adversary with an entry issue.
A the vast majority of the zero-click on exploits are engineered to acquire gain of vulnerabilities in applications these types of as messaging, SMS, or email apps that obtain and system untrusted information.
As a consequence, if there exists a security vulnerability in the manner an app interprets the incoming information, a danger actor could weaponize this shortcoming to craft a malicious image that, when sent to a target’s product, automatically executes the code embedded in it.
The lack of conversation concerned in zero-click attacks means there are much less traces of any nefarious activity, creating them hugely-prized tools to deliver spy ware able of checking people and harvesting a prosperity of sensitive data.
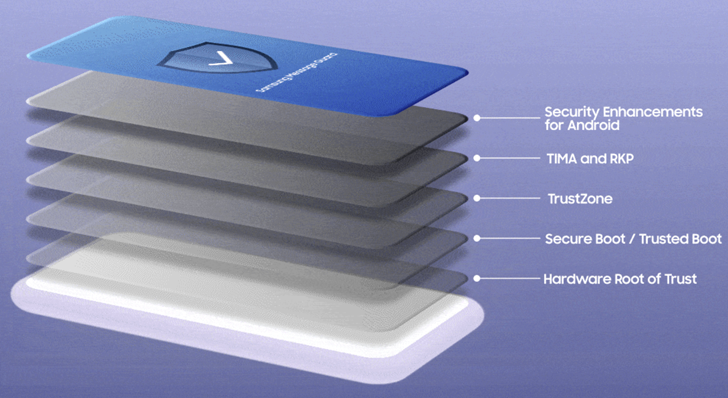
Samsung’s Concept Guard functions against a range of image formats, which include PNG, JPG/JPEG, GIF, ICO, WEBP, BMP, and WBMP, and essentially acts as a sandbox which is created to quarantine photos acquired via the application from the relaxation of the working procedure.
“Information Guard checks the file little bit by bit and processes it in a managed ecosystem to make sure it cannot infect the relaxation of your machine,” the company claimed.
The function is also analogous to a characteristic in Apple’s iMessage known as BlastDoor that the tech huge incorporated in iOS 14 as a indicates to counter zero-simply click attacks by means of its messaging app.
Apple, final year, also released an “extraordinary, optional safety” setting dubbed Lockdown Manner that hardens iPhones and iPads from “very exceptional and highly sophisticated cyber attacks.”
Observed this post interesting? Comply with us on Twitter and LinkedIn to read through much more unique articles we put up.
Some pieces of this article are sourced from:
thehackernews.com


 Fortinet Issues Patches for 40 Flaws Affecting FortiWeb, FortiOS, FortiOS, and FortiProxy
Fortinet Issues Patches for 40 Flaws Affecting FortiWeb, FortiOS, FortiOS, and FortiProxy