The North Korean superior persistent risk (APT) actor dubbed ScarCruft is making use of weaponized Microsoft Compiled HTML Support (CHM) files to download additional malware.
According to many experiences from AhnLab Security Unexpected emergency reaction Heart (ASEC), SEKOIA.IO, and Zscaler, the progress is illustrative of the group’s ongoing efforts to refine and retool its methods to sidestep detection.
“The team is consistently evolving its resources, tactics, and treatments even though experimenting with new file formats and techniques to bypass security sellers,” Zscaler researchers Sudeep Singh and Naveen Selvan stated in a new evaluation printed Tuesday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
ScarCruft, also tracked less than the names APT37, Reaper, RedEyes, and Ricochet Chollima, has exhibited an amplified operational tempo considering that the begin of the yr, concentrating on numerous South Korean entities for espionage needs. It is identified to be lively due to the fact at least 2012.
Past thirty day period, ASEC disclosed a campaign that utilized HWP data files that get gain of a security flaw in the Hangul term processing software to deploy a backdoor referred to as M2RAT.
But new conclusions reveal the risk actor is also making use of other file formats such as CHM, HTA, LNK, XLL, and macro-based mostly Microsoft Workplace paperwork in its spear-phishing attacks towards South Korean targets.
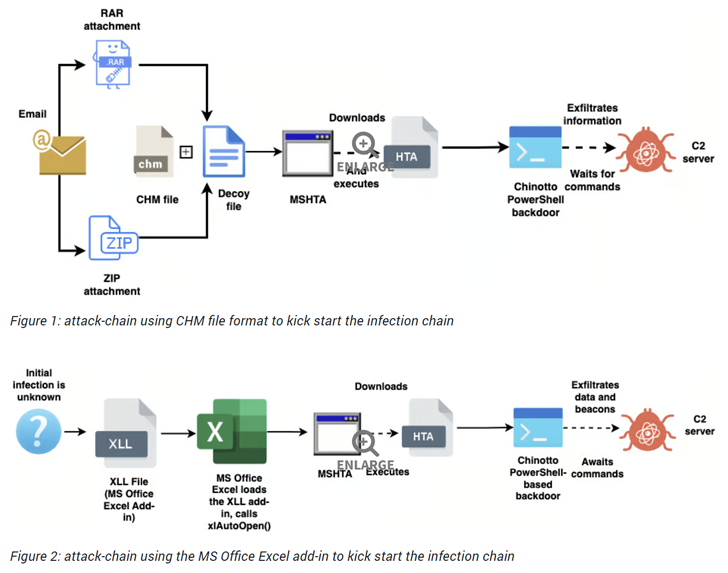
These infection chains generally serve to show a decoy file and deploy an up to date variation of a PowerShell-primarily based implant known as Chinotto, which is able of executing commands despatched by a server and exfiltrating sensitive info.
Some of the new abilities of Chinotto involve capturing screenshots just about every 5 seconds and logging keystrokes. The captured information is saved in a ZIP archive and sent to a distant server.
WEBINARDiscover the Hidden Risks of Third-Party SaaS Apps
Are you mindful of the hazards related with 3rd-party application access to your firm’s SaaS applications? Be a part of our webinar to understand about the varieties of permissions becoming granted and how to limit risk.
RESERVE YOUR SEAT
The insights about ScarCruft’s many attack vectors arrive from a GitHub repository maintained by the adversarial collective to host malicious payloads considering that Oct 2020.
“The danger actor was ready to preserve a GitHub repository, usually staging destructive payloads for additional than two many years devoid of staying detected or taken down,” Zscaler researchers stated.
Outside the house of malware distribution, ScarCruft has also been noticed serving credential phishing webpages focusing on a number of email and cloud companies these types of as Naver, iCloud, Kakao, Mail.ru, and 163.com.
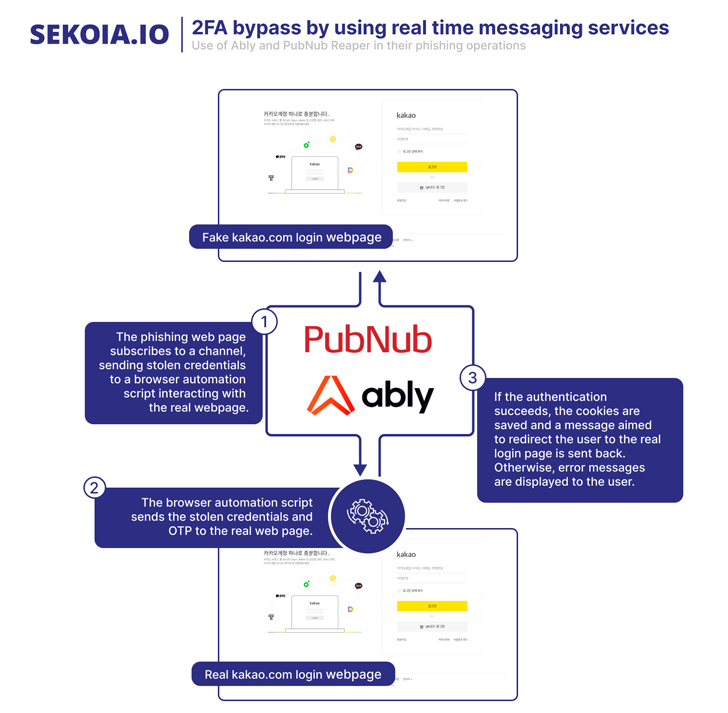
It really is having said that not apparent how these internet pages are accessed by the victims, boosting the possibility that they may well have been embedded inside iframes on sites controlled by the attacker or sent as HTML attachments via email.
Also uncovered by SEKOIA.IO is a piece of malware named AblyGo, a backdoor written in Go that makes use of the Ably serious-time messaging framework to obtain instructions.
The use of CHM information to smuggle malware appears to be catching on with other North Korea-affiliated teams as perfectly, with ASEC uncovering a phishing campaign orchestrated by Kimsuky to distribute a backdoor accountable for harvesting clipboard details and recording keystrokes.
Located this short article intriguing? Abide by us on Twitter and LinkedIn to go through far more special written content we put up.
Some sections of this short article are sourced from:
thehackernews.com

 Surge in compromised credentials highlights rampant cyber hygiene failings
Surge in compromised credentials highlights rampant cyber hygiene failings