Cybersecurity scientists have lose gentle on a new dropper-as-a-provider (DaaS) for Android called SecuriDropper that bypasses new security limitations imposed by Google and provides the malware.
Dropper malware on Android is made to function as a conduit to install a payload on a compromised system, generating it a lucrative company design for threat actors, who can advertise the capabilities to other legal groups.
What’s more, undertaking so also enables adversaries to independent the growth and execution of an attack from the installation of the malware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Droppers and the actors behind them are in a regular point out of evolution as they attempt to outwit evolving security actions,” Dutch cybersecurity business ThreatFabric claimed in a report shared with The Hacker Information.

1 this sort of security measure released by Google with Android 13 is what is actually termed the Limited Options, which stops sideloaded purposes from getting Accessibility and Notification Listener permissions, which are often abused by banking trojans.
SecuriDropper aims to get all around this guardrail without the need of finding detected, with the dropper generally disguised as a seemingly harmless app. Some of the samples observed in the wild are as follows –
- com.appd.instll.load (Google)
- com.appd.instll.load (Google Chrome)
“What can make SecuriDropper stand out is the complex implementation of its installation procedure,” ThreatFabric discussed.
“In contrast to its predecessors, this spouse and children works by using a diverse Android API to set up the new payload, mimicking the method utilized by marketplaces to put in new apps.”
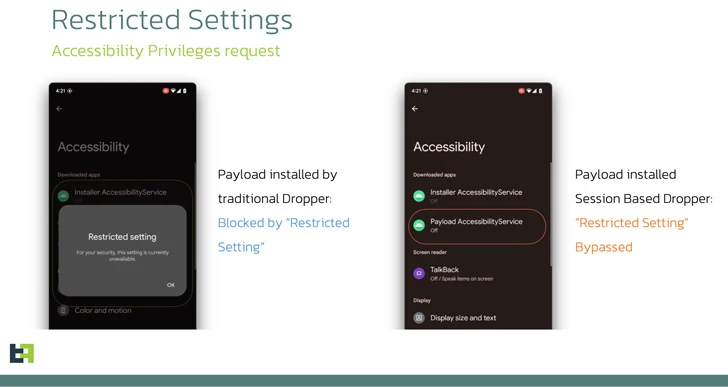
Particularly, this involves requesting for permissions to read through and publish details to external storage (Read through_External_STORAGE and Generate_Exterior_STORAGE) as very well as set up and delete offers (Request_Put in_Offers and DELETE_Offers).
In the second phase, the installation of the malicious payload is facilitated by urging the victims to click on a “Reinstall” button on the application to solve a purported installation error.

ThreatFabric explained it has observed Android banking trojans these types of as SpyNote and ERMAC dispersed through SecuriDropper on misleading sites and 3rd-party platforms like Discord.
A further dropper support that has also been noticed featuring a very similar Limited Options bypass is Zombinder, an APK binding instrument that was suspected to be shut down before this calendar year. It really is now not apparent if there is any relationship among the two instruments.
“As Android continues to increase the bar with each individual iteration, cybercriminals, also, adapt and innovate,” the firm reported. “Dropper-as-a-Company (DaaS) platforms have emerged as powerful tools, allowing for destructive actors to infiltrate products to distribute adware and banking trojans.”
Identified this post fascinating? Follow us on Twitter and LinkedIn to read through extra exclusive written content we article.
Some sections of this posting are sourced from:
thehackernews.com


 Iranian Hackers Launches Destructive Cyberattacks on Israeli Tech and Education Sectors
Iranian Hackers Launches Destructive Cyberattacks on Israeli Tech and Education Sectors