This previous January, a SaaS Security Posture Management (SSPM) company named Wing Security (Wing) built waves with the start of its totally free SaaS-Shadow IT discovery answer. Cloud-dependent firms were being invited to gain perception into their employees’ SaaS use by way of a wholly no cost, self-service products that operates on a “freemium” design. If a consumer is impressed with the solution and desires to achieve much more insights or take remediation action, they can acquire the enterprise solution.
“In today’s financial reality, security budgets have not essentially been cut down, but potential buyers are far extra very careful in their buying decisions and rightfully so. We believe that that you cannot protected what you do not know, so being aware of need to be a simple commodity. Once you recognize the magnitude of your SaaS attack layer, you can make an educated conclusion as to how you are going to solve it. Discovery is the purely natural and essential initial step and it should really be accessible to any one.” stated Galit Lubetzky Sharon, Wing’s Co-Founder and CTO
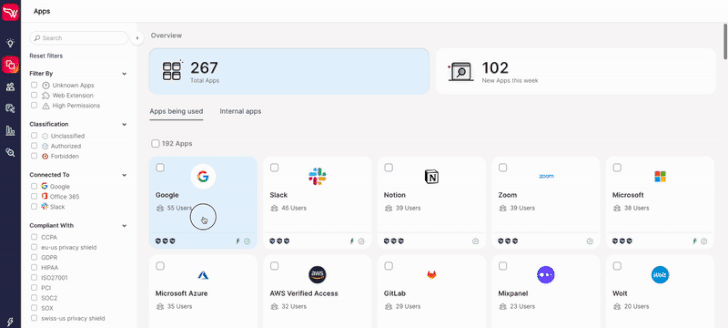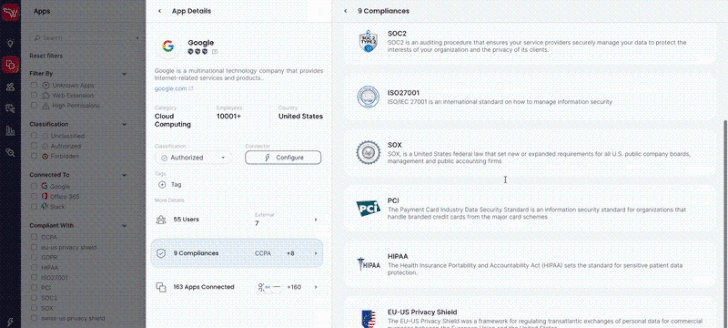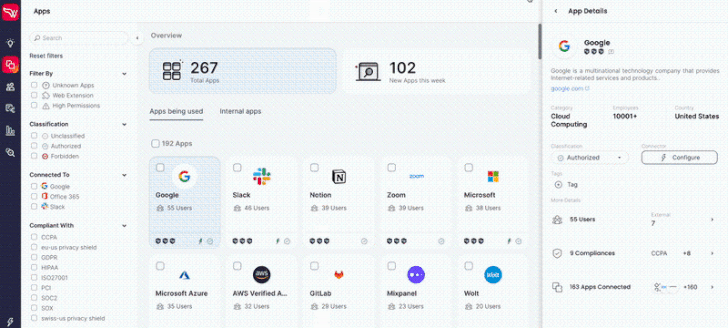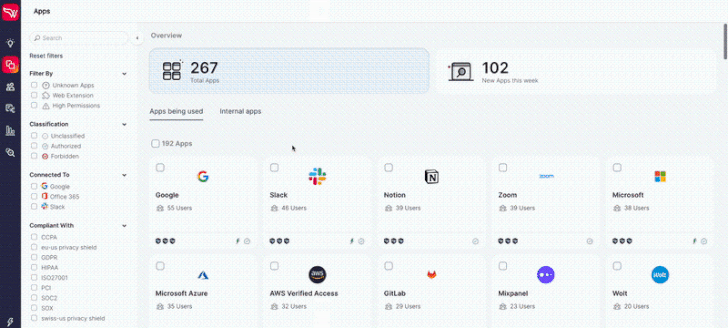
The organization reported that in just the initially couple of months of launching, in excess of 200 companies enrolled in their self-services no cost discovery instrument, including to the firm’s present customer base. They a short while ago launched a quick report on the findings from hundreds of organizations that unveiled SaaS use, and the figures are unsettling.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Tangible Dangers of Increasing SaaS Use
In 71.4% of corporations, staff use an typical of 2.4 SaaS purposes that have been breached in the earlier a few months. On average, 58% of SaaS apps are employed by only a person employee. A quarter of organizations’ SaaS people are external. These numbers, together with other attention-grabbing facts, are identified in the company’s report, together with explanations as to why they believe that this is the case and the pitfalls that need to be taken into thing to consider.
SaaS utilization is often decentralized and tricky to govern, and its rewards can also pose security threats when ungoverned. Whilst IAM/IM techniques help businesses regain control about a part of their employees’ SaaS utilization, this command is minimal to the sanctioned SaaS apps that IT/Security knows about. The challenge is that SaaS applications are frequently onboarded by employees with no involving IT or security teams. In other terms, this is SaaS Shadow IT. This is particularly accurate for numerous SaaS applications that don’t demand a credit rating card or supply a cost-free version.
The typical situation is that of an staff, typically distant, searching for a fast resolution to a enterprise problem. The option is often an application that the personnel found on-line, granted permissions to (these can be browse and create permissions, or even execute), and then entirely forgot about. This can direct to many security dangers.
SaaS similar pitfalls can be categorized into a few diverse varieties:
Applications related
Illustrations incorporate dangerous purposes with a very low security rating, indicating a larger probability that these purposes are vulnerable. And programs that have just lately been compromised but have permissions into the organization’s information, instantly compromising that info. In its absolutely free solution, Wing attaches a security score to every single application discovered and alerts consumers to the dangerous purposes in their SaaS stack.
Other illustrations of the pitfalls that SaaS purposes inherently provide incorporate 3rd party SaaS apps, all those that “piggyback” off the recognized and authorized SaaS. Or apps that were granted high permissions that are almost never provided: According to Wing, 73.3% of all permissions that ended up provided to purposes by the end users had been not in use in over 30 times. This begs the query, why leave open doorways into your organization’s details when you’re not even utilizing the software that is asking for them?
People Similar
A person cannot ignore the human factor. Afterall, SaaS is frequently onboarded directly by the worker utilizing it. They are the types granting permissions, not always knowledgeable of the that means powering these permissions. Listed here much too Wing’s absolutely free option gives some aid: For the initially 100 applications located, Wing provides a checklist of the customers who use them. For total facts as to who the users are, exterior customers and consumer inconsistent habits across purposes, Wing presents its organization edition.
Info Relevant
The hazards related with facts security are broad and have a entire classification of merchandise that offer with them, this sort of as DLPs and DSPMs. Nonetheless, when it comes to the SaaS programs that workforce use, information relevant issues can span from sensitive information getting shared on apps that are not meant for file sharing, tricks shared on general public channels (Slack is a popular illustration) and even the substantial amount of money of documents that staff members share externally and then forget about about, leaving that external link broad open. Preserving a clean up SaaS-natural environment consists not only of sustaining the applications and buyers, but also running the details that resides in and amongst these purposes.
In conclusion, SaaS-Shadow IT discovery has come to be a critical space of issue for IT and security groups, as the usage of SaaS applications carries on to develop speedily. Though SaaS apps provide quite a few rewards to organizations, they also pose significant security risks when ungoverned. These challenges consist of the use of breached applications, granting extreme permissions, person inconsistencies, and details security issues.
It is crucial for companies to have visibility into their employees’ SaaS utilization to make knowledgeable selections and consider remedial actions to mitigate these challenges. In 2023, the expectation is that essential SaaS-Shadow IT discovery must no more time appear at a charge, as it should really be a elementary commodity for companies aiming to secure their SaaS environment.
Observed this report interesting? Follow us on Twitter and LinkedIn to examine additional special information we publish.
Some elements of this post are sourced from:
thehackernews.com


 New FiXS ATM Malware Targeting Mexican Banks
New FiXS ATM Malware Targeting Mexican Banks