Vulnerability evaluation benefits in Orange Cyberdefenses’ Security Navigator exhibit that some vulnerabilities to start with discovered in 1999 are continue to identified in networks today. This is concerning.
Age of VOC results
Our Vulnerability Scans are performed on a recurring foundation, which offers us the chance to look at the difference concerning when a scan was carried out on an Asset, and when a presented getting on that Asset was noted. We can get in touch with that the getting ‘Age’. If the results first claimed are not addressed, they will occur in much more scans around time with rising Age, and so we can keep track of how the Age of documented conclusions improvements around time.
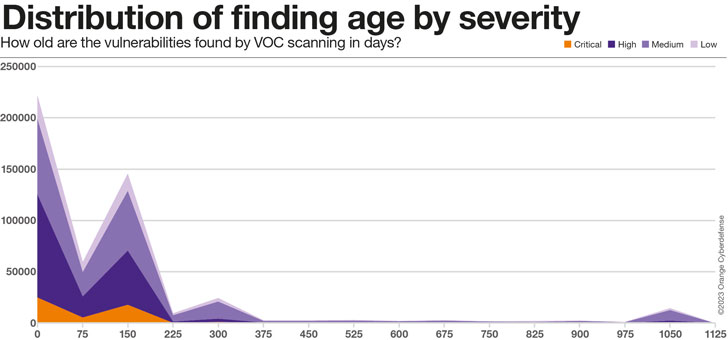
As the chart under obviously illustrates, the vast majority of real conclusions in our dataset, across all Severity levels, are in between 75 and 225 times outdated. There is a second ‘peak’ at all-around 300 days, which we suspect has a lot more to do with the age of the details in the dataset and can thus be dismissed. Eventually, there is a fascinating ‘bump’ at around 1,000 days, which we consider signifies the ‘long tail’ of results in the dataset that will basically by no means be addressed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
75% of the results in the 1000-times ‘bump’ are Medium Severity, but 16% are categorised as Large or Critical Severity.
The Common Age of results in our dataset is impacted as a lot by alterations in our Shopper and Property set as any exterior factor, as can be witnessed in the superior diploma of variation. Yet, there is a crystal clear increase in the Typical Age of results of 241% from 63 to 215 times around the 24 months given that we’ve been onboarding clientele on to this platform.
Roughly grouping confirmed conclusions from our Vulnerability Scan details by ‘Age Group’ reveals the following:
- Only 20% of all conclusions are addressed in beneath 30 days
- 80% all results acquire 30 days or extra to patch
- 57% of all conclusions just take 90 days or more to patch.
- 215 times Ordinary
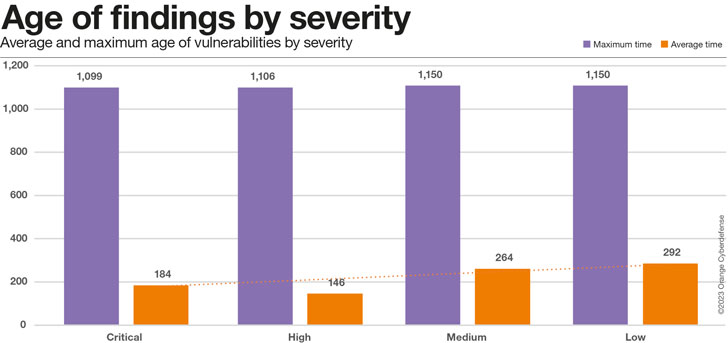
Common/max age of conclusions by severity
The chart below suggests that even Critical Vulnerabilities are having all-around 6 months on normal to take care of, but that is encouragingly at the very least 36% speedier than the time for lower-severity issues.
Taking a nearer glimpse at the readings of regular vs. optimum time for various scores of criticality we close up with the chart underneath.
Whilst our summary of critical issues getting resolved more rapidly stands for the average mitigation time, the greatest time is regularly high irrespective of criticality.
We will have to watch this metric extra as the dataset grows in the long run.
Field Comparison
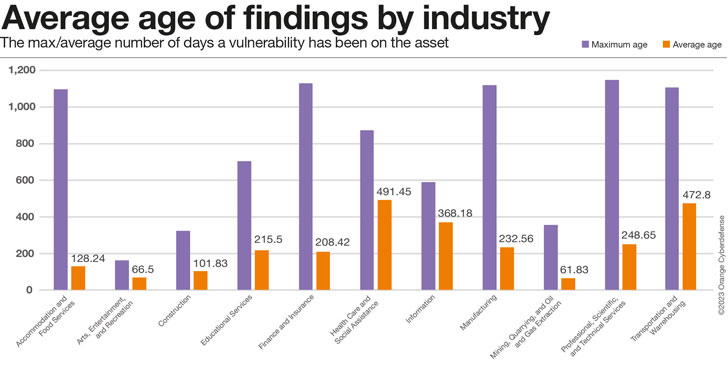
The optimum age of results in the check out down below serves as a great deal as an indicator of how prolonged clients from that Industry have been existing in our dataset as anything else, though the typical age is a much better proxy for how nicely shoppers are performing at addressing the issues we report. Industries with higher maximums and lower averages would therefore be executing the best, higher highest and higher average… the ‘worst.’ Industries with very minimal greatest ages have in all probability not been in the dataset for quite extensive and should really, for that reason, potentially not be integrated in comparisons on this metric.
Nevertheless these Industries are in contrast, the obtaining Age is a relating to metric.
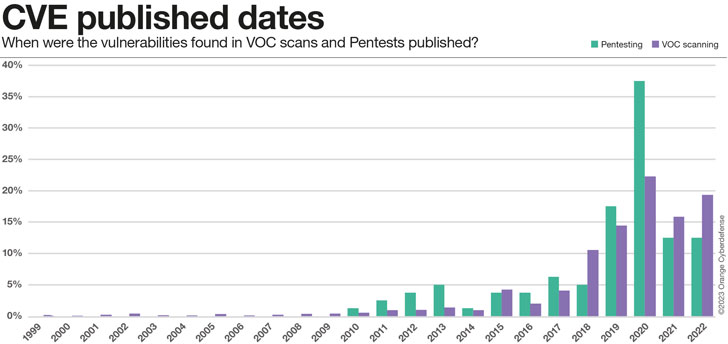
How outdated are those people vulnerabilities definitely?
So considerably we have only seemed at the relative time, from when we initial found a vulnerability in an asset up right up until now (if however existing). On the other hand, that does not give us any facts on how previous all those vulnerabilities really are. Getting a closer seem at the observed CVEs we can assess their publishing dates. The effects are fairly baffling, but seem to be to in good shape the image that emerges: for a single purpose or a different, some vulnerabilities are just not mounted, ever. They come to be portion of the security credit card debt that corporations accumulate.
- .5% of CVEs claimed are 20 yrs old or more
- 13% of CVEs reviews are 10 decades aged or much more
- 47% of CVEs are 5 several years previous or a lot more
Conclusion
Much more than 22 vulnerabilities with assigned CVEs are printed every working day. With an ordinary CVSS score earlier mentioned 7 (Higher Severity), each individual of these disclosed vulnerabilities is a significant datapoint that affects our risk equations and our real publicity to threats.
Vulnerability Scanning and Penetration Testing are mechanisms we use to make perception of the vulnerabilities that may well effects our security posture, fully grasp their probable effect, prioritize and choose ideal motion. These two assessment workout routines are distinct in technique, but use related language and serve a similar goal.
This 12 months we are which include an assessment of datasets from equally companies in the Navigator. This is the to start with time we are trying this, and our data is nevertheless far from best.
What we can evidently see is the we’re struggling to control the vulnerabilities we know about. On average, it is taking our clients 215 days to patch a vulnerability we report to them. This is a very little decreased for Critical Vulnerabilities – it appears these are patched 36% quicker than ‘Low’ severity issues. But the picture is still grim: 80% of all Results choose 30 days or a lot more to patch, 57% get 90 times or a lot more.
Our pentesting groups are still exploring vulnerabilities that were being 1st identified in 2010, and our scanning teams experience issues that day back to 1999! Without a doubt 47% of CVEs are 5 yrs outdated or a lot more. 13% are as outdated as 10 several years or much more. This is a about result.
This is just an excerpt of the analysis. Much more information, like the criticality of vulnerabilities and the adjustments in Pentesting and VOC scanning benefits about time (as nicely as a ton of other appealing exploration subjects), can be found in the Security Navigator. It really is totally free of cost, so have a look. It is really really worth it!
Take note: This insightful piece has been expertly crafted and generously shared by Charl van der Walt, Head of Security Research at Orange Cyberdefense.
Identified this article attention-grabbing? Follow us on Twitter and LinkedIn to go through extra exclusive information we article.
Some pieces of this article are sourced from:
thehackernews.com


 Up to 350,000 open source projects vulnerable to 15-year-old Python bug
Up to 350,000 open source projects vulnerable to 15-year-old Python bug