A security vulnerability has been disclosed in the preferred WordPress plugin Crucial Addons for Elementor that could be most likely exploited to accomplish elevated privileges on influenced internet sites.
The issue, tracked as CVE-2023-32243, has been dealt with by the plugin maintainers in model 5.7.2 that was delivered on May possibly 11, 2023. Critical Addons for Elementor has above a single million active installations.
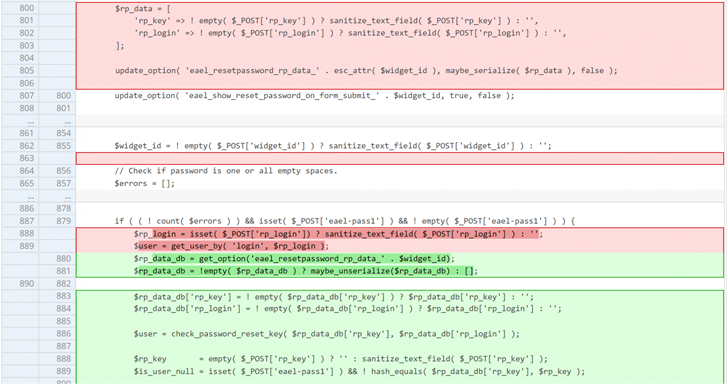
“This plugin suffers from an unauthenticated privilege escalation vulnerability and makes it possible for any unauthenticated consumer to escalate their privilege to that of any user on the WordPress internet site,” Patchstack researcher Rafie Muhammad stated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Prosperous exploitation of the flaw could allow a danger actor to reset the password of any arbitrary person as long as the destructive party is knowledgeable of their username. The shortcoming is believed to have existed considering the fact that edition 5.4..
This can have major ramifications as the flaw could be weaponized to reset the password involved with an administrator account and seize total management of the internet site.
“This vulnerability happens mainly because this password reset function does not validate a password reset essential and alternatively right adjustments the password of the provided consumer,” Muhammad pointed out.

The disclosure will come far more than a 12 months soon after Patchstack uncovered another extreme flaw in the identical plugin that could have been abused to execute arbitrary code on compromised web sites.
The results also comply with the discovery of a new wave of attacks concentrating on WordPress web sites because late March 2023 that aims to inject the infamous SocGholish (aka FakeUpdates) malware.
SocGholish is a persistent JavaScript malware framework that capabilities as an preliminary accessibility supplier to facilitate the shipping of further malware to infected hosts. The malware has been dispersed by using generate-by downloads masquerading as a web browser update.
The latest campaign detected by Sucuri has been observed to leverage compression techniques working with a software program library referred to as zlib to conceal the malware, reduce its footprint, and steer clear of detection.
“Lousy actors are frequently evolving their tactics, strategies, and techniques to evade detection and prolong the lifetime of their malware strategies,” Sucuri researcher Denis Sinegubko stated.
“SocGholish malware is a prime instance of this, as attackers have altered their tactic in the earlier to inject destructive scripts into compromised WordPress websites.”
Approaching WEBINARLearn to Halt Ransomware with Genuine-Time Protection
Be part of our webinar and master how to prevent ransomware attacks in their tracks with true-time MFA and services account defense.
Preserve My Seat!
It really is not just SocGholish. Malwarebytes, in a specialized report this 7 days, comprehensive a malvertising marketing campaign that serves website visitors to adult web-sites with popunder advertisements that simulate a phony Windows update to drop the “in2al5d p3in4er” (aka Invalid Printer) loader.
“The scheme is really nicely created as it depends on the web browser to show a whole screen animation that really substantially resembles what you’d assume from Microsoft,” Jérôme Segura, director of risk intelligence at Malwarebytes, stated.
The loader, which was documented by Morphisec very last month, is created to test the system’s graphic card to identify if it truly is working on a virtual equipment or in a sandbox ecosystem, and finally start the Aurora data stealer malware.
The campaign, per Malwarebytes, has claimed 585 victims over the earlier two months, with the menace actor also connected to other tech assist scams and an Amadey bot command-and-handle panel.
Found this article exciting? Abide by us on Twitter and LinkedIn to study extra exclusive information we submit.
Some parts of this posting are sourced from:
thehackernews.com


 Threat Actors Use Babuk Code to Build Hypervisor Ransomware
Threat Actors Use Babuk Code to Build Hypervisor Ransomware