Substantial-profile government entities in Southeast Asia are the target of a cyber espionage marketing campaign carried out by a Chinese risk actor regarded as Sharp Panda given that late final calendar year.
The intrusions are characterized by the use of a new variation of the Soul modular framework, marking a departure from the group’s attack chains observed in 2021.
Israeli cybersecurity enterprise Test Stage said the “very long-operating” activities have historically singled out countries these types of as Vietnam, Thailand, and Indonesia. Sharp Panda was 1st documented by the company in June 2021, describing it as a “really-arranged operation that positioned considerable exertion into remaining under the radar.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Apparently, the use of the Soul backdoor was thorough by Broadcom’s Symantec in Oct 2021 in connection to an unattributed espionage procedure concentrating on defense, healthcare, and ICT sectors in Southeast Asia.
The implant’s origins, in accordance to investigate released by Fortinet FortiGuard Labs in February 2022, day as much back as October 2017, with the malware repurposing code from Gh0st RAT and other publicly out there tools.
The attack chain detailed by Check Point begins with a spear-phishing email made up of a lure document that leverages the Royal Highway Wealthy Textual content Format (RTF) weaponizer to drop a downloader by exploiting a person of various vulnerabilities in the Microsoft Equation Editor.
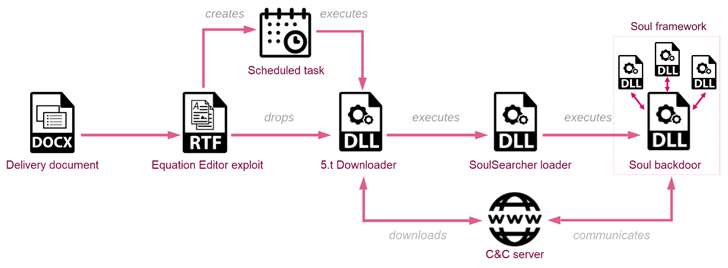
The downloader, in switch, is built to retrieve a loader recognized as SoulSearcher from a geofenced command-and-manage (C&C) server that only responds to requests originating from IP addresses corresponding to the specific countries.
The loader is then accountable for downloading, decrypting, and executing the Soul backdoor and its other parts, therefore enabling the adversary to harvest a huge assortment of information and facts.
“The Soul main module is responsible for speaking with the C&C server and its key purpose is to get and load in memory added modules,” Examine Point said.
Uncover the Most recent Malware Evasion Techniques and Avoidance Tactics
All set to bust the 9 most perilous myths about file-centered attacks? Be a part of our forthcoming webinar and become a hero in the combat versus affected person zero bacterial infections and zero-day security situations!
RESERVE YOUR SEAT
“Interestingly, the backdoor configuration is made up of a ‘radio silence’-like feature, the place the actors can specify particular hrs in a week when the backdoor is not allowed to talk with the C&C server.”
The findings are however an additional sign of the resource sharing which is prevalent amid Chinese superior persistent risk (APT) groups to aid intelligence accumulating.
“Though the Soul framework has been in use given that at the very least 2017, the menace actors at the rear of it have been regularly updating and refining its architecture and capabilities,” the corporation claimed.
It more famous that the campaign is probably “staged by innovative Chinese-backed risk actors, whose other tools, capabilities and placement in the broader network of espionage actions are nevertheless to be explored.”
Identified this article attention-grabbing? Observe us on Twitter and LinkedIn to examine more exclusive written content we post.
Some components of this posting are sourced from:
thehackernews.com


 CISA’s KEV Catalog Updated with 3 New Flaws Threatening IT Management Systems
CISA’s KEV Catalog Updated with 3 New Flaws Threatening IT Management Systems