An older model of Shein’s Android software endured from a bug that periodically captured and transmitted clipboard contents to a distant server.
The Microsoft 365 Defender Research Workforce claimed it identified the trouble in edition 7.9.2 of the app that was produced on December 16, 2021. The issue has given that been dealt with as of May possibly 2022.
Shein, at first named ZZKKO, is a Chinese on the internet fast vogue retailer primarily based in Singapore. The app, which is now at version 9.., has over 100 million downloads.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The tech huge claimed it can be not “exclusively informed of any destructive intent powering the habits,” but famous that the purpose is just not necessary to execute responsibilities on the app.
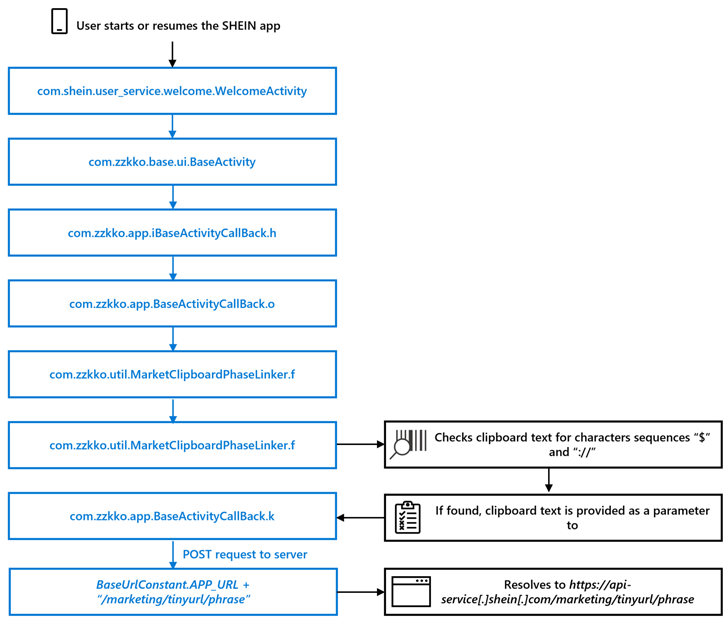
It even more pointed out that launching the application soon after copying any content to the machine clipboard automatically triggered an HTTP Put up request containing the details to the server “api-company[.]shein[.]com.”
To mitigate this sort of privacy threats, Google has further designed advancements to Android in new years, which includes exhibiting toast messages when an app accesses the clipboard and barring applications from having the knowledge except it is actively managing in the foreground.
Find out the Latest Malware Evasion Techniques and Prevention Procedures
Ready to bust the 9 most risky myths about file-dependent attacks? Be part of our approaching webinar and come to be a hero in the combat towards individual zero bacterial infections and zero-working day security functions!
RESERVE YOUR SEAT
“Thinking of cell people often use the clipboard to duplicate and paste delicate information and facts, like passwords or payment data, clipboard contents can be an desirable concentrate on for cyberattacks,” researchers Dimitrios Valsamaras and Michael Peck stated.
“Leveraging clipboards can enable attackers to acquire goal information and facts and exfiltrate handy info.”
Found this short article appealing? Adhere to us on Twitter and LinkedIn to browse a lot more special content we submit.
Some elements of this posting are sourced from:
thehackernews.com


 LastPass Hack: Engineer’s Failure to Update Plex Software Led to Massive Data Breach
LastPass Hack: Engineer’s Failure to Update Plex Software Led to Massive Data Breach