An “intense” advanced persistent menace (APT) team recognised as SideWinder has been joined to about 1,000 new attacks because April 2020.
“Some of the primary traits of this threat actor that make it stand out between the many others, are the sheer variety, substantial frequency and persistence of their attacks and the massive assortment of encrypted and obfuscated malicious factors utilized in their operations,” cybersecurity company Kaspersky mentioned in a report that was presented at Black Hat Asia this month.
SideWinder, also identified as Rattlesnake or T-APT-04, is mentioned to have been active considering that at minimum 2012 with a observe report of focusing on navy, defense, aviation, IT businesses, and lawful companies in Central Asian nations around the world this sort of as Afghanistan, Bangladesh, Nepal, and Pakistan.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Kaspersky’s APT developments report for Q1 2022 published late very last month revealed that the risk actor is actively increasing the geography of its targets further than its target profile to other nations around the world and locations, which include Singapore.
SideWinder has also been observed capitalizing the ongoing Russo-Ukrainian war as a entice in its phishing campaigns to distribute malware and steal sensitive info.
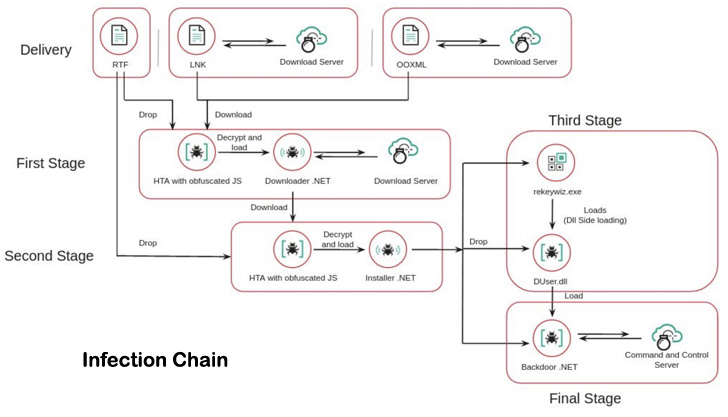
The adversarial collective’s an infection chains are notable for incorporating malware-rigged files that acquire benefit of a distant code vulnerability in the Equation Editor component of Microsoft Business (CVE-2017-11882) to deploy destructive payloads on compromised methods.
Moreover, SideWinder’s toolset employs several sophisticated obfuscation routines, encryption with exceptional keys for each destructive file, multi-layer malware, and splitting command-and-regulate (C2) infrastructure strings into unique malware parts.
The a few-stage an infection sequence commences with the rogue documents dropping a HTML Software (HTA) payload, which subsequently hundreds a .NET-based module to set up a 2nd-stage HTA component that is designed to deploy a .NET-primarily based installer.

This installer, in the up coming section, is both equally accountable for creating persistence on the host and loading the last backdoor in memory. The implant, for its portion, is capable of harvesting information of desire as properly as program information and facts, amid other individuals.
No much less than 400 domains and subdomains have been set to use by the danger actor about the past two a long time. To incorporate an supplemental layer of stealth, the URLs applied for C2 domains are sliced into two parts, the very first part of which is bundled in the .NET installer and the latter 50 % is encrypted inside the second phase HTA module.
“This danger actor has a relatively high degree of sophistication utilizing several infection vectors and advanced attack techniques,” Noushin Shabab of Kaspersky explained, urging that organizations use up-to-date variations of Microsoft Business office to mitigate these types of attacks.
Found this report exciting? Abide by THN on Fb, Twitter and LinkedIn to go through much more distinctive articles we write-up.
Some elements of this short article are sourced from:
thehackernews.com


 Learn Raspberry Pi and Arduino with 9 Online Developer Training Courses
Learn Raspberry Pi and Arduino with 9 Online Developer Training Courses