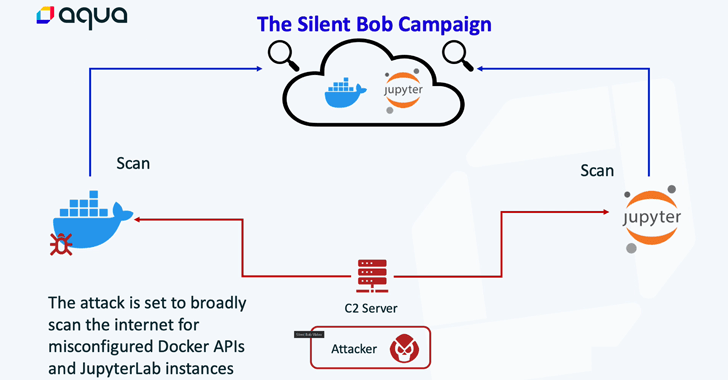
Cybersecurity scientists have unearthed an attack infrastructure which is remaining used as part of a “probably massive marketing campaign” in opposition to cloud-native environments.
“This infrastructure is in early stages of tests and deployment, and is mostly regular of an aggressive cloud worm, developed to deploy on exposed JupyterLab and Docker APIs in order to deploy Tsunami malware, cloud qualifications hijack, useful resource hijack, and even further infestation of the worm,” cloud security business Aqua claimed.
The exercise, dubbed Silentbob in reference to an AnonDNS domain set up by the attacker, is said to be joined to the notorious cryptojacking team tracked as TeamTNT, citing overlaps in strategies, approaches, and strategies (TTPs). Alternatively, it could be the get the job done of an “state-of-the-art copycat.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Aqua’s investigation was prompted in the aftermath of an attack focusing on its honeypot in early June 2023, foremost to the discovery of 4 malicious container images that are created to detect exposed Docker and Jupyter Lab circumstances and deploy a cryptocurrency miner as effectively as the Tsunami backdoor.
This feat is achieved by indicates of a shell script which is programmed to launch when the container starts and is utilised to deploy the Go-based ZGrab scanner to find misconfigured servers. Docker has since taken down the images from the general public registry. The listing of illustrations or photos are down below –
- shanidmk/jltest2 (44 pulls)
- shanidmk/jltest (8 pulls)
- shanidmk/sysapp (11 pulls)
- shanidmk/blob (29 pulls)
shanidmk/sysapp, apart from executing a cryptocurrency miner on the contaminated host, is configured to download and run further binaries, which Aqua explained could either be backup cryptominers or the Tsunami malware.
Future WEBINAR🔐 Privileged Obtain Management: Discover How to Conquer Key Troubles
Explore various techniques to conquer Privileged Account Administration (PAM) issues and amount up your privileged accessibility security system.
Reserve Your Spot
Also downloaded by the container is a file named “aws.sh.txt,” a script that is most likely developed to systematically scan the surroundings for AWS keys for subsequent exfiltration.
Aqua stated it located 51 servers with uncovered JupyterLab circumstances in the wild, all of which have been actively exploited or exhibited symptoms of exploitation by risk actors. This incorporates a “stay manual attack on one of the servers that employed masscan to scan for exposed Docker APIs.”
“In the beginning, the attacker identifies a misconfigured server (possibly Docker API or JupyterLab) and deploys a container or engages with the Command Line Interface (CLI) to scan for and establish further victims,” security researchers Ofek Itach and Assaf Morag explained.
“This process is developed to unfold the malware to an growing selection of servers. The secondary payload of this attack incorporates a crypto miner and a backdoor, the latter utilizing the Tsunami malware as its weapon of alternative.”
Located this short article interesting? Follow us on Twitter and LinkedIn to go through extra distinctive articles we post.
Some areas of this post are sourced from:
thehackernews.com

 INTERPOL Nabs Hacking Crew OPERA1ER’s Leader Behind $11 Million Cybercrime
INTERPOL Nabs Hacking Crew OPERA1ER’s Leader Behind $11 Million Cybercrime