Shutterstock
Security scientists have discovered a flaw in the logic driving the BlackMatter ransomware family that makes it possible for businesses to cease the application from encrypting remote shared folders on an organisation’s network.
The results imply corporations are ready to deploy a fairly uncomplicated mitigation to guard by themselves in opposition to a critical attack vector in a person of the most successful ransomware strains of the past handful of decades.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Despite the ransomware family remaining highly sophisticated and deploying many anti-debugging methods, the mitigation can assistance prevent BlackMatter from looking for other computers in the lively listing (Ad), in accordance to researchers at Illusive.
By generating a ‘dummy’ computer account in the Ad, and setting the ‘dNSHostName’ attribute to
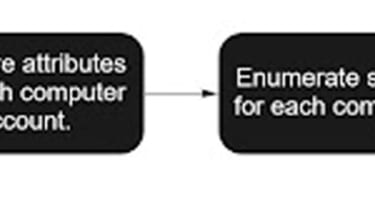
BlackMatter’s encryption and pc enumeration process
Illusive
Researchers mentioned BlackMatter first tries to enumerate all computer system accounts in the Advert, scanning all accounts alphabetically. It then retrieves the attributes for each individual computer system account before enumerating shares for every single computer system and encrypting each available share, other than for ADMIN$ and C$.
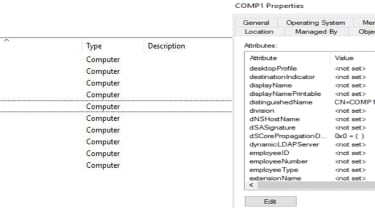
An instance of how to established up a computer account to halt the encryption of all machines in an organisation
Illusive
This implies by naming a person account ‘aaa-comp’, for example, and disabling the dNSHostName attribute, program directors can have that ‘dummy’ account look to start with in the alphabetically organised Advertisement. If BlackMatter started out scanning for personal computers, it would scan aaa-comp very first and would end searching for other personal computers to encrypt in the Ad.
The outcome would lead to the an infection of that single laptop account and the machine would develop into encrypted, but it would stop BlackMatter from encrypting remote file shares. This dummy ‘aaa-comp’ account would correctly act like a honeypot, avoiding a critical security incident.
The researchers said halting the research and encryption of distant shared folders is just one attack approach BlackMatter utilizes to inflict problems on victims, and that the mitigation isn’t really a silver bullet. Other procedures, this sort of as nearby file encryption and mapped drive encryption, are all nonetheless practical to BlackMatter, even with the mitigation in put.
It would be “strange” to configure a laptop or computer account without having a dNSHostName established, Shahar Zelig, security researcher at Illusive, told IT Pro. Personal computers usually have the dNSHostName attribute when signing up for the Advertisement.
Requested why BlackMatter stops exploring when it encounters these types of an account, Zelig claimed: “we are not able to be particular about the motive, but getting a computer system account lacking the dNSHostName attribute is not a little something that appears normally in an Energetic Listing environment, so it appears most likely that the BlackMatter team viewed as it as an edge-circumstance that they should not cope with.”
Preventing BlackMatter from encrypting remotely available folders can decreased the sum of injury the attack can reach. The mitigation could not stop encryption of the pcs on which it’s executed, but can help guard general public folders made up of small business-critical information.
“This obtaining is important considering that encrypting remote shared folders may well lead to substantial [disruption] to an organisation, irrespective of whether this is a shared folder on an employee’s laptop or a file server that serves the full organisation with significant information,” claimed Zelig. “In a situation where BlackMatter is dispersed to only a portion of the network, distant share encryption is considerable, since it can have an affect on available shares even however the ransomware by itself was not executed on the goal gadget.”
Complex overview of BlackMatter
When it gains accessibility to a device, BlackMatter attempts to retrieve all pcs from the Advert, but it only searches the designed-in ‘Computers’ container and not objects discovered in other organisational models (OUs). When it identifies all desktops in the Ad, it makes use of lightweight listing entry protocol (LDAP) requests to retrieve characteristics of people personal computers.
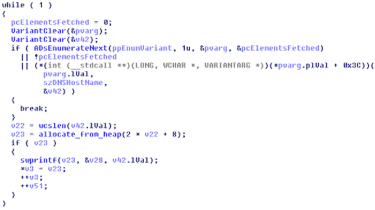
BlackMatter applying APIs to enumerate pc accounts
Illusive
BlackMatter utilizes 3 typical API capabilities to enumerate desktops in the Advert and keep them for additional use: ADsOpenObject, AdsBuildEnumerator, ADsEnumerateNext.
The latter of the 3 is named for every iteration of the loop and the loop breaks if both ADsEnumerateNext fails, no factors are returned by ADsEnumerateNext, or if it really is not able to get the dNSHostName attribute. The loop is broken if dNSHostName is not established.
After computers have been enumerated, BlackMatter then employs the NetShareEnum perform to map what shares just about every laptop has, which results in a NetShareEnumAll request more than remote treatment simply call (RPC). BlackMatter will then endeavor to access the shares by means of server information block (SMB), ignoring C$ and ADMIN$, and disregarding forms STYPE_DISKTREE and STYPE_Exclusive, before encrypting the documents.
BlackMatter background
BlackMatter is a family members of ransomware that has claimed numerous higher-profile victims in the earlier 12 months, which include the massively disruptive attack on Colonial Pipeline.
Iowa and Minnesota-primarily based farms ended up also productively specific by ransomware operators utilizing BlackMatter, which led CISA, FBI, and NSA to publish a joint advisory warning US businesses of the threat it confronted. The US govt later on offered a $10 million reward to anyone who could aid the investigation into these at the rear of the attack on Colonial Pipeline.
Inspite of the refined mother nature of BlackMatter and how devastating it has tested to be as a ransomware strain, Illusive’s findings you should not mark the initial time a cyber security outfit has identified flaws in its code.
Adhering to an investigation of BlackMatter in October 2021, scientists at Emisoft found that an encryption flaw used by the ransomware could be exploited so that victims wouldn’t have to pay out the ransom in get to restore obtain to their data files. The company claimed the getting has assisted providers help you save millions in ransom payments.
Some elements of this report are sourced from:
www.itpro.co.uk

 Log4J-Related RCE Flaw in H2 Database Earns Critical Rating
Log4J-Related RCE Flaw in H2 Database Earns Critical Rating