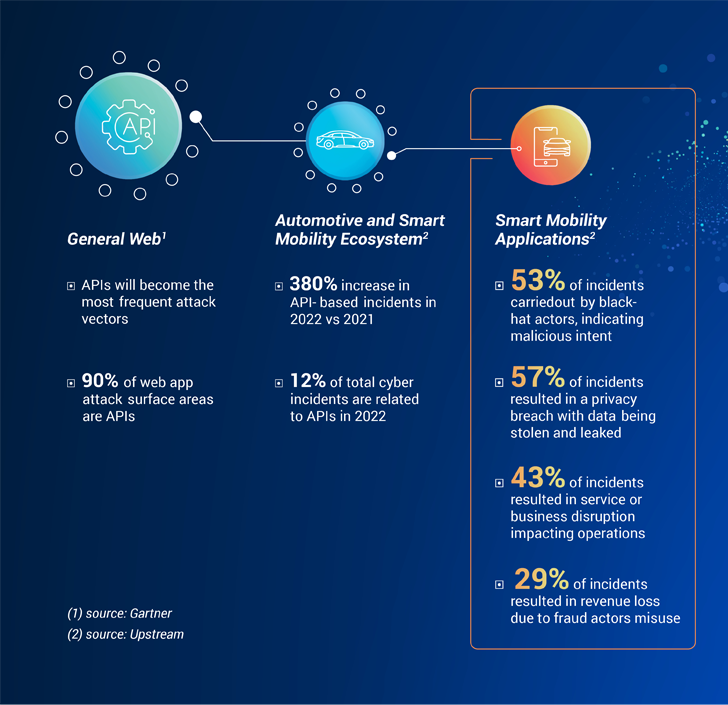
The emergence of wise mobility services and programs has led to a sharp raise in the use of APIs in the automotive marketplace. Even so, this improved reliance on APIs has also designed them one of the most frequent attack vectors. According to Gartner, APIs account for 90% of the web software attack surface parts.
With no surprise, equivalent trends are rising also in the smart mobility area. A current Automotive and Sensible Mobility Cybersecurity Report by Upstream Security indicates that the automotive and sensible mobility ecosystem has observed a 380% increase in API-centered incidents in 2022, compared to 2021. On top of that, APIs accounted for 12% of complete cyber incidents in 2022, up from only 2% in 2021.
When examining smart mobility applications and solutions, Upstream’s risk intelligence team documented that black-hat actors had been found to be behind 53% of incidents, indicating malicious intent as the driving force of the majority of API-linked attacks. The effect of these incidents goes nicely beyond facts and PII breaches, typically leading to provider disruptions, fraudulent routines, trust concerns and opportunity profits reduction.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Details-pushed mobility expert services reshape regular automotive revenue styles
In new decades, car connectivity has grown dramatically, introducing progressive details-driven income chances for classic automotive stakeholders as perfectly as new players. Mobility general has come to be more connected, with ridesharing, motor vehicle rental solutions, and even fleet management products and services all making use of cell apps to provide easy access and enhanced working experience to individuals. Fashionable facts use instances offer you ongoing checking and support stakeholders introduce new functions and alternatives. In accordance to investigation by McKinsey, 30% of automotive income will be attributed to info-pushed and smart mobility solutions by 2030. But as opposed to IT-centered purposes, these modern and data-pushed apps heavily employ APIs that have a immediate influence on vehicles on the street.
Substantial site visitors jams induced by manipulated API transactions
In 2022, we observed an significantly refined use of APIs in automotive and good mobility cyberattacks. As an attack vector, APIs attract the attention of researchers and malicious actors as they have to have a somewhat reduced threshold of know-how and automotive knowledge. Basically reducing the barrier of entry of menace actors to a bare minimum. A one vulnerability in an API can pose a immediate influence on thousands and thousands of automobiles, throughout different fleets. A powerful case in point of the relieve of attack and the considerable effects can be observed in a modern incident in Europe: again in mid-2022 central Moscow was gridlocked when a ride-hailing provider was maliciously manipulated to deliver all readily available taxis to a one site, creating hours-lengthy website traffic jams, impeding people’s freedom of motion, and placing general public infrastructure and basic safety at risk. In this scenario, attackers failed to need any understanding of how cars run or function, all they required to do was to identify API vulnerabilities and exploit them.
WAF is not (generally) sufficient: developing a contextual framework for intelligent mobility API security
Smart mobility providers have often been monitoring and securing API transactions to stay clear of income loss thanks to fraud, company downtime, and compromising organizational or end users non-public data. But, traditional API security remedies have a substantial “blindspot” when it comes to sensible mobility. They frequently fail to detect complex attacks that effects mobility programs, property, and people thanks to the lack of contextual analysis of the effect of API transactions on transferring autos.
Making sure a sturdy cybersecurity posture in the clever mobility ecosystem requires increasing the scope to include things like a contextual assessment of the actual-lifestyle affect of APIs on mobility assets, which include cars on the road. API security is slowly evolving to also integrate OT (Operational Technology) features that correlate involving API visitors, transactions, and the contextual point out of mobility assets to deliver a strong cybersecurity posture. The target is to layer API discovery, profiling and checking with deep analysis of the habits of mobility property and the affect of the specific API transaction on safety. When you get into account how OT property behave differently to IT belongings, be it their ignition standing, site, or speed, you can start to method securing them in a contextual manner.
Smart mobility players are adopting a new approach to securing good mobility API transactions, which incorporates 4 vital techniques:
- Map the potential attack surface
- Continuously watch API traffic
- Apply contextual anomaly detection
- Mitigate and answer to cyber threats
The first phase is to recognize the likely attack surface as it relates to APIs. This calls for inventorying APIs used by companies, purposes, and third get-togethers, from documentation resources like Swagger as perfectly as the examination of live, authentic-time API traffic and transactions. This assessment includes both of those documented, undocumented or even the depreciated-but-reside APIs that may be a “fantastic” entry issue for threat actors.
After the attack floor is understood, checking API targeted visitors helps enhance the cybersecurity posture by guaranteeing that any variations are documented and detected, as very well as any misuse of misconfigurations. When checking mobility API targeted visitors in true-time, it truly is significant to contemplate the skill to cope with the scale and complexity of these transactions and understand any deviations from the standard point out of the asset. When a solitary API call can start off the engine of a automobile or report back the spot of a driver – cybersecurity will become particularly important.
Because clever mobility belongings are OT in nature, the context that they are in – their condition at a presented instant in time – can be utilised in securing them. Any big deviations or anomalies in their behavior can show likely misuse or attack. By correlating the assets point out with the API visitors, cyber groups can have an understanding of the contextual implications and the effect on purposes or buyers. Seemingly legitimate requests can in some cases be an indicator of destructive intent. For instance, a solitary IP, however not suspicious originally, that sends requests to multiple motor vehicles or mobility apps must induce instant suspicion and investigation.
Upstream Security has not long ago taken a phase further in the contextual examination of API transactions. It relies on a sturdy digital twin, which is a are living electronic illustration of the asset’s point out, created on data streams from purposes, backend servers, telematics products and services, and more. As a outcome, it delivers a comprehensive see of all mobility property and buyers impacted. Once the attack or misconfiguration has been detected using the unique context supplied by understanding the condition of the asset, cyber groups can correctly and promptly react and mitigate possible threats.
This special mobility–driven method opens a new scope of API security pursuits in the sensible mobility ecosystem. As innovation in this space is shifting so rapid, introducing new transportation products, autonomous companies and experience-sharing selections, eliminating “blindspots” will go on to be a top rated precedence challenge.
Discovered this post appealing? Follow us on Twitter and LinkedIn to study additional special articles we post.
Some sections of this write-up are sourced from:
thehackernews.com


 Multi-cloud ‘over-permissioning’ causing cyber risk headaches for businesses
Multi-cloud ‘over-permissioning’ causing cyber risk headaches for businesses