A new exploitation technique termed Uncomplicated Mail Transfer Protocol (SMTP) smuggling can be weaponized by danger actors to send spoofed email messages with phony sender addresses whilst bypassing security actions.
“Danger actors could abuse vulnerable SMTP servers all over the world to deliver malicious e-mails from arbitrary email addresses, letting focused phishing attacks,” Timo Longin, a senior security marketing consultant at SEC Seek advice from, stated in an examination released very last thirty day period.
SMTP is a TCP/IP protocol utilised to send and acquire email messages above a network. To relay a concept from an email consumer (aka mail user agent), an SMTP connection is set up among the consumer and server in buy to transmit the precise information of the email.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The server then relies on what is identified as a mail transfer agent (MTA) to verify the area of the recipient’s email handle, and if it’s distinctive from that of the sender, it queries the domain title process (DNS) to seem up the MX (mail exchanger) history for the recipient’s area and total the mail exchange.
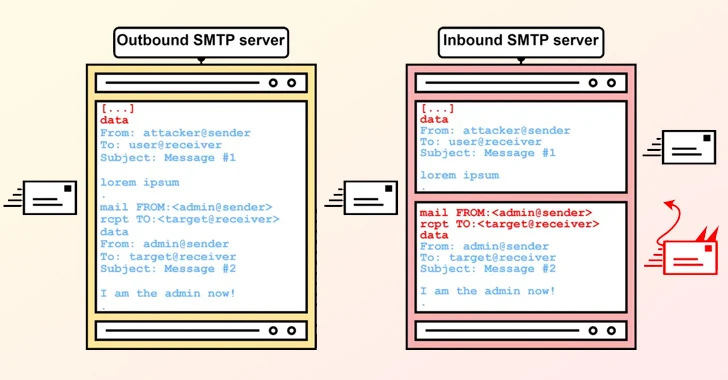
The crux of SMTP smuggling is rooted in the inconsistencies that occur when outbound and inbound SMTP servers cope with finish-of-information sequences otherwise, most likely enabling danger actors to split out of the concept details, “smuggle” arbitrary SMTP instructions, and even deliver different e-mails.

It borrows the thought from a recognised attack approach recognised as HTTP request smuggling, which will take advantage of discrepancies in the interpretation and processing of the “Content-Length” and “Transfer-Encoding” HTTP headers to prepend an ambiguous ask for to the inbound ask for chain.
Exclusively, it exploits security flaws in messaging servers from Microsoft, GMX, and Cisco to deliver e-mails spoofing thousands and thousands of domains. Also impacted are SMTP implementations from Postfix and Sendmail.

This will allow for sending cast e-mail that seemingly seem like they are originating from authentic senders and defeat checks in position erected to make sure the authenticity of incoming messages – i.e., DomainKeys Identified Mail (DKIM), Area-centered Information Authentication, Reporting and Conformance (DMARC), and Sender Policy Framework (SPF).
Even though Microsoft and GMX have rectified the issues, Cisco claimed the results do not represent a “vulnerability, but a characteristic and that they will not change the default configuration.” As a consequence, inbound SMTP smuggling to Cisco Safe Email circumstances is even now doable with default configurations.
As a fix, SEC Talk to endorses Cisco customers adjust their configurations from “Cleanse” to “Allow for” in buy to stay clear of obtaining spoofed e-mails with valid DMARC checks.
Uncovered this short article appealing? Abide by us on Twitter and LinkedIn to browse a lot more exclusive content we put up.
Some components of this posting are sourced from:
thehackernews.com

 DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation
DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation