A new open resource distant accessibility trojan (RAT) called DogeRAT targets Android users mainly positioned in India as element of a refined malware marketing campaign.
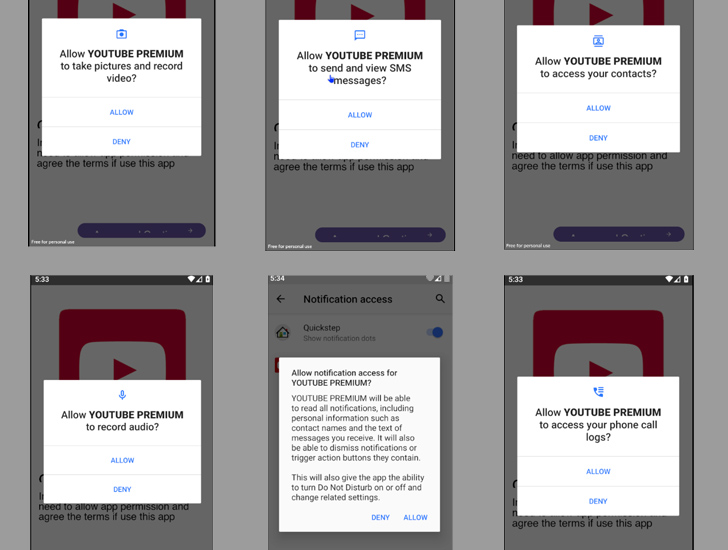
The malware is distributed by way of social media and messaging platforms beneath the guise of legitimate purposes like Opera Mini, OpenAI ChatGOT, and Top quality versions of YouTube, Netflix, and Instagram.
“After set up on a victim’s unit, the malware gains unauthorized obtain to sensitive information, such as contacts, messages, and banking qualifications,” cybersecurity organization CloudSEK claimed in a Monday report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“It can also get command of the infected product, enabling destructive steps this kind of as sending spam messages, creating unauthorized payments, modifying data files, and even remotely capturing shots by means of the device’s cameras.”
DogeRAT, like lots of other malware-as-a-provider (MaaS) choices, is promoted by its India-dependent developer as a result of a Telegram channel that has far more than 2,100 subscribers because it was made on June 9, 2022.
This also includes a high quality subscription which is offered for grime-low cost charges ($30) with additional abilities these kinds of as taking screenshots, stealing photographs, capturing clipboard content material, and logging keystrokes.
In a even further try to make it a lot more obtainable to other legal actors, the no cost edition of DogeRAT has been produced out there on GitHub, along with screenshots and movie tutorials showcasing its capabilities.
“We do not endorse any illegal or unethical use of this instrument,” the developer states in the repository’s README.md file. “The consumer assumes all accountability for the use of this software.”
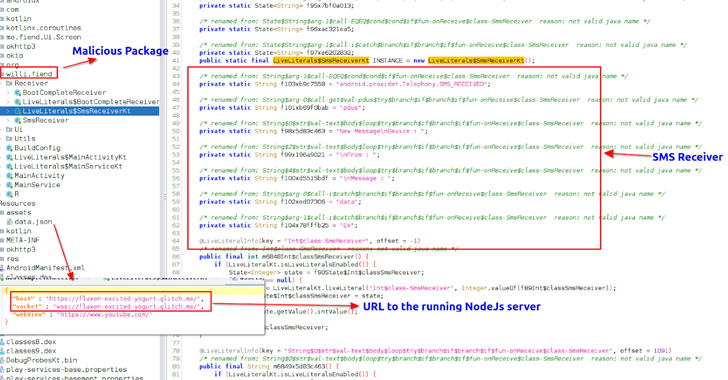
Upon set up, the Java-primarily based malware requests for intrusive permissions to complete its info-collecting aims, in advance of exfiltrating it to a Telegram bot.
Forthcoming WEBINAR Zero Trust + Deception: Master How to Outsmart Attackers!
Discover how Deception can detect state-of-the-art threats, cease lateral motion, and greatly enhance your Zero Rely on method. Join our insightful webinar!
Save My Seat!.advert-button,.ad-label,.advert-label:just aftershow:inline-block.advertisement_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px sound #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-right-radius:25px-moz-border-radius-bottomright:25px.advert-labelfont-dimensions:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.advertisement-label:followingwidth:50pxheight:6pxcontent:”border-major:2px stable #d9deffmargin: 8px.ad-titlefont-dimensions:21pxpadding:10px 0font-fat:900textual content-align:leftline-top:33px.advert-descriptiontext-align:leftfont-size:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.ad-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-pounds:500letter-spacing:.2px
“This campaign is a stark reminder of the fiscal inspiration driving scammers to frequently evolve their practices,” CloudSEK researcher Anshuman Das stated.
“They are not just constrained to making phishing web sites, but also distributing modified RATs or repurposing malicious applications to execute fraud strategies that are minimal-price and easy to established up, yet yield large returns.”
The results come as Google-owned Mandiant comprehensive a new Android backdoor referred to as LEMONJUICE which is intended to empower distant handle of and accessibility to a compromised product.
“The malware is able of monitoring system site, recording the microphone, retrieving speak to lists, accessing contact, SMS, clipboard, and notification logs, viewing mounted programs, downloading and uploading files, viewing connectivity status, and executing supplemental commands from the C2 server,” researcher Jared Wilson stated.
Discovered this post appealing? Abide by us on Twitter and LinkedIn to examine additional exclusive material we article.
Some pieces of this post are sourced from:
thehackernews.com

 New BrutePrint Attack Lets Attackers Unlock Smartphones with Fingerprint Brute-Force
New BrutePrint Attack Lets Attackers Unlock Smartphones with Fingerprint Brute-Force