Repairing indirect vulnerabilities is just one of individuals advanced, monotonous and, very frankly, tedious jobs that no a person genuinely would like to touch. No one except for Debricked, it seems. Certain, there are a lot of ways to do it manually, but can it be carried out quickly with nominal risk of breaking adjustments? The Debricked workforce decided to find out.
A forest total of fragile trees
So, exactly where do you even start?
Firstly, there wants to be a way to repair the vulnerability, which, for indirect dependencies, is no stroll in the park. Secondly, it requirements to be completed in a secure way, or, with out something breaking.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
You see, oblique dependencies are released deep down the dependency tree and it’s extremely challenging to get to the exact variation you want. As Debricked’s Head of R&D the moment put it, “You are turning the knobs by actively playing all around with your immediate dependencies and praying to Torvalds that the accurate indirect deals are fixed. When Torvalds is in your favour, you have to sacrifice some cloud storage to uncle Bob to make positive the updates you should not break your software.”
In other words, there really ought to be an simpler, less stressful, way to do it.
In this short article, we will wander you by way of how solving transitive vulnerabilities can be completed manually and, in direction of the end, exhibit you the Debricked answer, which enables you to do it routinely. If you happen to be really just interested in the solution, I recommend you commence scrolling.
Precision medical procedures on your dependency tree
All through the exploration phase of the graph-database venture, or, how Debricked nowadays fixes your open resource vulnerabilities at the pace of light, the workforce stumbled upon some articles describing how to take care of oblique vulnerabilities in NPM.
As mentioned in the article, the `minimist` bundle is affected by vulnerabilities, namely CVE-2021-44906 and CVE-2020-7598.
These are both “Prototype Pollution” vulnerabilities, which means that arguments are not correctly sanitized. Luckily for us, the maintainers of `minimist` set these vulnerabilities in variation 1.2.6.
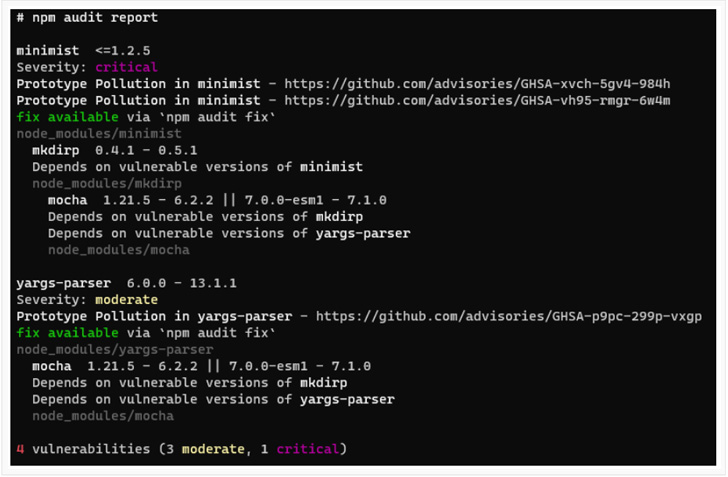
Regrettably, `mocha` version 7.1. resolves `minimist` ..8, which is inside of the susceptible selection of these vulnerabilities. As suggested by the creator of this post, these vulnerabilities can be fixed in a couple distinctive methods.
But! What about breaking improvements?
The very first recommendation is to basically cause an update of all “indirect dependencies”, meaning that we is not going to basically transform the version of `mocha`. To complete this update, merely run `npm update`, delete your `npm.lock` file, and operate `npm install`. This regenerates the dependency tree with the newest attainable edition (according to constraints) of your oblique dependencies. With this method, the risk of breaking changes is quite minimal as you essentially really don’t update any of your root dependencies, just your indirect types.
Breaking improvements arise when the offer operation or interface is not forward appropriate, indicating that an update to the offer could lead to your application to split. Popular breaking variations are class/purpose-removal, transform of arguments to a operate, or licence-modify (observe out for that a single!).
But everyday living is not usually this uncomplicated, and this simple update of the tree will not fix the vulnerability. The trouble is that `mkdirp` has truly locked their edition of `minimist` to ..8. This indicates that the contributors of `mkdirp` have arrive to the summary that they are not compatible with more recent versions of `minimist`, and forcing the update of `minimist` could introduce breaking adjustments in between `mkdirp` and `minimist`.
Think… graphs!
So, the million-dollar concern is: what variation of `mocha` should really be utilised, that in convert trickles down to a safe variation of `minimist` with no breaking the dependency tree? This is actually a graph challenge, which has been described in this short article.
What graph algorithm would solve this difficulty? How NPM resolves dependencies can be a bit challenging, as they are allowed to “break up” the dependency tree. This usually means that they can have various variations of a person dependency to make sure that we always have a tree that is appropriate. To solve the vulnerability, we need to have to make confident that all situations of `minimist` are harmless by updating all roots that can trickle down to `minimist`.
The algorithm utilised to remedy this trouble is known as “All Max Paths Harmless”. By walking down the dependency graph and retaining the max versions, all whilst pruning all other versions of that package in every intersection, we can make an approximate illustration of our dependency tree. If the approximation is safe and sound, that indicates that our authentic tree will be harmless as well!
By doing this algorithm for all potential variations of `mocha`, we locate the smallest update to resolve this vulnerability. To get the pace we required for this algorithm, the staff had to make a custom made Neo4j procedure, which can handle browsing over 100 root versions with a lookup depth of 30+ in ~150 milliseconds. Fast, huh?
In this scenario, we never have to lookup really far… as 7.1.1 of `mocha` is secure! This is only a patch update, which suggests that the risk of breaking changes is incredibly reduced. For a lot less complex instances (like this instance), ‘npm audit’ can aid you with their excellent ‘npm audit fix’ command.
Never be advertisement-hoc, enter the pub-sub-human way of functioning!
Now, if you acquired this far (congratulations, quite outstanding) and believed, “this appears truly elaborate and like an awful ton of do the job,” you should not fear – you’re not the only just one. The good thing is, all this comes about absolutely mechanically in the Debricked software when clicking this little button:
As of ideal now, this is out there for Javascript. Shortly, the assist will be prolonged to Java, Golang, C#, Python and PHP.
If you are not nevertheless a Debricked user, what are you waiting for? It is totally free for solitary devs, scaled-down groups and open source tasks (and if you happen to be a larger sized corporation, worry not. There is certainly a generous cost-free trial). Signal up for totally free in this article.
Observed this posting intriguing? Abide by THN on Facebook, Twitter and LinkedIn to study more exclusive articles we put up.
Some elements of this posting are sourced from:
thehackernews.com


 Santander Warns of 87% Surge in Celeb Crypto Scams
Santander Warns of 87% Surge in Celeb Crypto Scams