SonicWall has released an advisory warning of a trio of security flaws in its Protected Cellular Entry (SMA) 1000 appliances, which include a substantial-severity authentication bypass vulnerability.
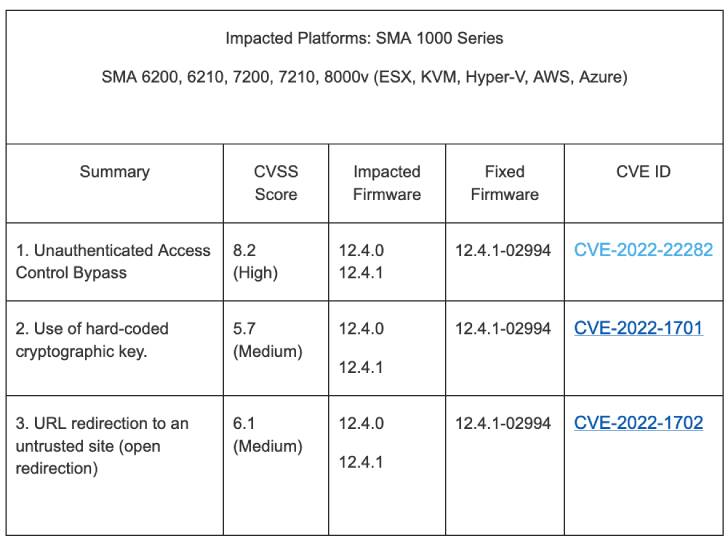
The weaknesses in question affect SMA 6200, 6210, 7200, 7210, 8000v operating firmware variations 12.4. and 12.4.1. The list of vulnerabilities is below –
- CVE-2022-22282 (CVSS score: 8.2) – Unauthenticated Obtain Manage Bypass
- CVE-2022-1702 (CVSS rating: 6.1) – URL redirection to an untrusted web site (open redirection)
- CVE-2022-1701 (CVSS score: 5.7) – Use of a shared and difficult-coded cryptographic important
Effective exploitation of the aforementioned bugs could make it possible for an attacker to unauthorized entry to interior sources and even redirect prospective victims to malicious sites.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Tom Wyatt of the Mimecast Offensive Security Staff has been credited with getting and reporting the vulnerabilities.
SonicWall pointed out that the flaws do not affect SMA 1000 sequence working variations before than 12.4., SMA 100 collection, Central Management Servers (CMS), and distant access customers.
Even though there is no proof that these vulnerabilities are being exploited in the wild, it really is proposed that end users implement the fixes in the light-weight of the simple fact that SonicWall appliances have offered an interesting bullseye in the previous for ransomware attacks.
“There are no non permanent mitigations,” the network security corporation said. “SonicWall urges impacted consumers to put into action relevant patches as quickly as probable.”
Uncovered this report attention-grabbing? Abide by THN on Fb, Twitter and LinkedIn to read through much more exclusive material we publish.
Some components of this posting are sourced from:
thehackernews.com


 IT Pro News In Review: Businesses cancel cyber policies, EE milestone, Costa Rica Conti attack
IT Pro News In Review: Businesses cancel cyber policies, EE milestone, Costa Rica Conti attack