A new malware pressure known as BundleBot has been stealthily running under the radar by having advantage of .NET solitary-file deployment approaches, enabling threat actors to seize delicate data from compromised hosts.
“BundleBot is abusing the dotnet bundle (solitary-file), self-contained structure that success in pretty reduced or no static detection at all,” Verify Stage stated in a report revealed this 7 days, introducing it is “usually dispersed via Facebook Advertisements and compromised accounts foremost to web sites masquerading as frequent system utilities, AI applications, and games.”
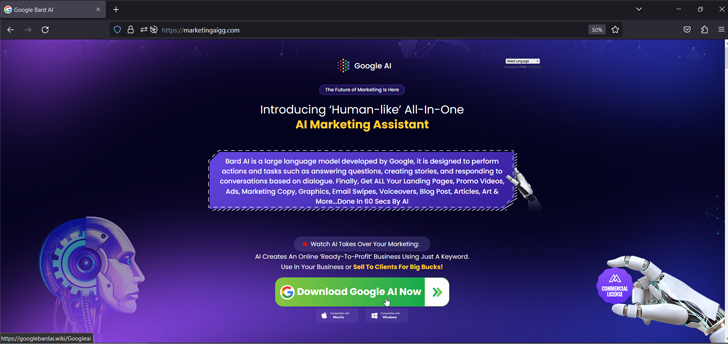
Some of these internet sites intention to mimic Google Bard, the company’s conversational generative artificial intelligence chatbot, engaging victims into downloading a bogus RAR archive (“Google_AI.rar”) hosted on legitimate cloud storage services this kind of as Dropbox.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The archive file, when unpacked, includes an executable file (“GoogleAI.exe”), which is the .NET single-file, self-contained application (“GoogleAI.exe”) that, in convert, incorporates a DLL file (“GoogleAI.dll”), whose obligation is to fetch a password-secured ZIP archive from Google Push.
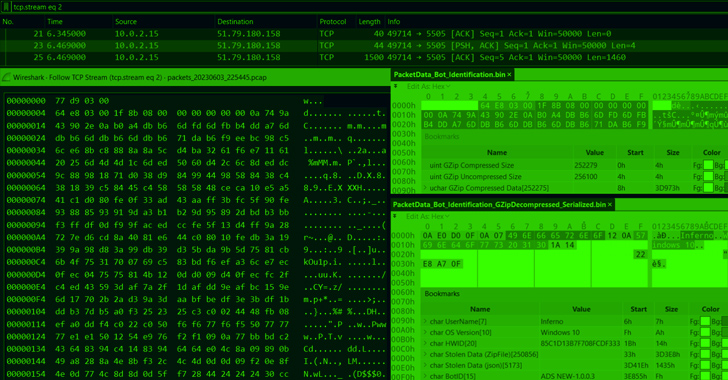
The extracted information of the ZIP file (“ADSNEW-1…3.zip”) is a further .NET one-file, self-contained application (“RiotClientServices.exe”) that incorporates the BundleBot payload (“RiotClientServices.dll”) and a command-and-regulate (C2) packet details serializer (“LirarySharing.dll”).
“The assembly RiotClientServices.dll is a customized, new stealer/bot that takes advantage of the library LirarySharing.dll to process and serialize the packet facts that are staying despatched to C2 as a component of the bot conversation,” the Israeli cybersecurity organization reported.
The binary artifacts hire customized-manufactured obfuscation and junk code in a bid to resist investigation, and come with capabilities to siphon facts from web browsers, seize screenshots, seize Discord tokens, data from Telegram, and Fb account information.
Verify Issue explained it also detected a next BundleBot sample that is pretty much identical in all features barring the use of HTTPS to exfiltrate the information and facts to a remote server in the type of a ZIP archive.
“The delivering method by way of Facebook Advertisements and compromised accounts is anything that has been abused by menace actors for a when, continue to combining it with one of the capabilities of the unveiled malware (to steal a victim’s Fb account info) could serve as a tricky self-feeding regime,” the business pointed out.
The enhancement will come as Malwarebytes uncovered a new campaign that employs sponsored posts and compromised confirmed accounts that impersonate Facebook Advertisements Supervisor to entice users into downloading rogue Google Chrome extensions that are made to steal Fb login information and facts.
Customers who click on the embedded hyperlink are prompted to obtain a RAR archive file made up of an MSI installer file that, for its aspect, launches a batch script to spawn a new Google Chrome window with the malicious extension loaded utilizing the “–load-extension” flag –
begin chrome.exe –load-extension=”%~dp0/nmmhkkegccagdldgiimedpiccmgmiedagg4″ “https://www.facebook.com/organization/equipment/advertisements-supervisor”
Upcoming WEBINARShield Against Insider Threats: Master SaaS Security Posture Management
Fearful about insider threats? We’ve obtained you coated! Be part of this webinar to check out functional techniques and the secrets of proactive security with SaaS Security Posture Management.
Be a part of Right now
“That custom extension is cleverly disguised as Google Translate and is viewed as ‘Unpacked’ for the reason that it was loaded from the community laptop or computer, relatively than the Chrome Web Retailer,” Jérôme Segura, director of risk intelligence at Malwarebytes, explained, noting it is “fully concentrated on Facebook and grabbing vital items of facts that could allow for an attacker to log into accounts.”
The captured information is subsequently sent utilizing the Google Analytics API to get all around content material security insurance policies (CSPs) to mitigate cross-internet site scripting (XSS) and info injection attacks.
The menace actors guiding the action are suspected to be of Vietnamese origin, who have, in modern months, exhibited acute curiosity in concentrating on Facebook company and marketing accounts. More than 800 victims around the world have been impacted, with 310 of individuals situated in the U.S.
“Fraudsters have a great deal of time on their fingers and commit years learning and knowledge how to abuse social media and cloud platforms, wherever it is a continual arm’s race to continue to keep poor actors out,” Segura explained. “Bear in mind that there is no silver bullet and anything at all that seems too very good to be genuine may pretty properly be a rip-off in disguise.”
Found this posting exciting? Adhere to us on Twitter and LinkedIn to browse more exclusive articles we post.
Some areas of this posting are sourced from:
thehackernews.com

 Local Governments Targeted for Ransomware – How to Prevent Falling Victim
Local Governments Targeted for Ransomware – How to Prevent Falling Victim