Governmental entities in the Center East and Africa have been at the obtaining conclusion of sustained cyber-espionage attacks that leverage in no way-ahead of-seen and scarce credential theft and Trade email exfiltration tactics.
“The major purpose of the attacks was to get very confidential and delicate information and facts, precisely related to politicians, navy routines, and ministries of international affairs,” Lior Rochberger, senior risk researcher at Palo Alto Networks, claimed in a complex deep dive revealed previous week.
The firm’s Cortex Danger Investigation team is tracking the activity under the non permanent identify CL-STA-0043 (the place CL stands for cluster and STA stands for condition-backed commitment), describing it as a “legitimate state-of-the-art persistent menace.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The an infection chain is triggered by the exploitation of vulnerable on-premises Internet Information Providers (IIS) and Microsoft Trade serves to infiltrate focus on networks.

Palo Alto Networks said it detected failed attempts to execute the China Chopper web shell in one particular of the attacks, prompting the adversary to shift ways and leverage an in-memory Visual Fundamental Script implant from the Exchange Server.
A successful break-in is adopted by reconnaissance activity to map out the network and solitary out critical servers that keep knowledge of price, which include domain controllers, web servers, Trade servers, FTP servers, and SQL databases.
CL-STA-0043 has also been observed leveraging native Windows applications for privilege escalation, therefore enabling it to build admin accounts and operate other applications with elevated privileges.
Yet another privilege escalation technique entails the abuse of accessibility options in Windows – i.e., the “sticky keys” utility (sethc.exe) – that helps make it possible to bypass login specifications and backdoor the methods.
“In the attack, the attacker usually replaces the sethc.exe binary or tips/references to these binaries in the registry, with cmd.exe,” Rochberger described. “When executed, it delivers an elevated command prompt shell to the attacker to operate arbitrary instructions and other tools.”
A very similar solution utilizing the Utility Manager (utilman.exe) to establish persistent backdoor entry to a victim’s atmosphere was documented by CrowdStrike earlier this April.
Approaching WEBINAR🔐 Mastering API Security: Understanding Your True Attack Surface
Find the untapped vulnerabilities in your API ecosystem and just take proactive actions toward ironclad security. Be part of our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:soon aftershow:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px stable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-appropriate-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-measurement:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:right afterwidth:50pxheight:6pxcontent:”border-top rated:2px good #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-bodyweight:900text-align:leftline-top:33px.wn-descriptiontextual content-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-size:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
Besides working with Mimikatz for credential theft, the menace actor’s modus operandi stands out for using other novel strategies to steal passwords, conduct lateral movement, and exfiltrate delicate knowledge, this kind of as –
- Applying network suppliers to execute a malicious DLL to harvest and export plaintext passwords to a distant server
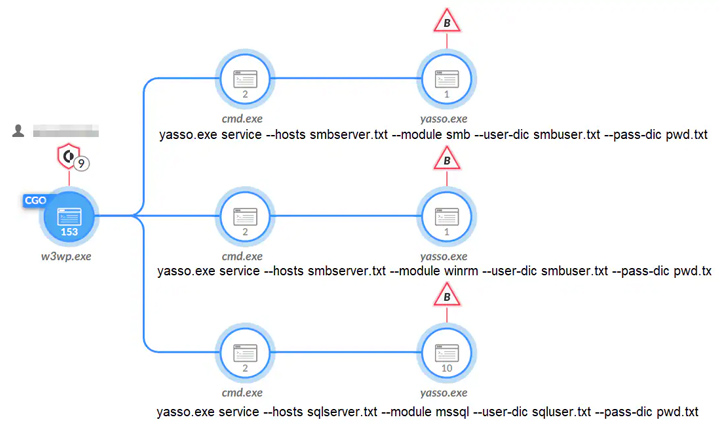
- leveraging an open-resource penetration screening toolset known as Yasso to unfold throughout the network, and
- Getting gain of the Exchange Administration Shell and PowerShell snap-ins to harvest email messages of interest
It really is really worth pointing out that the use of Trade PowerShell snap-ins to export mailbox details has been beforehand described in the circumstance of a Chinese condition-sponsored group dubbed Silk Storm (previously Hafnium), which 1st came to mild in March 2021 in relationship with the exploitation of Microsoft Exchange Server.
“This activity group’s stage of sophistication, adaptiveness, and victimology propose a really capable APT danger actor, and it is suspected to be a country-condition menace actor,” Rochberger reported.
Discovered this article interesting? Stick to us on Twitter and LinkedIn to go through far more unique content material we write-up.
Some components of this write-up are sourced from:
thehackernews.com


 Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions
Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions