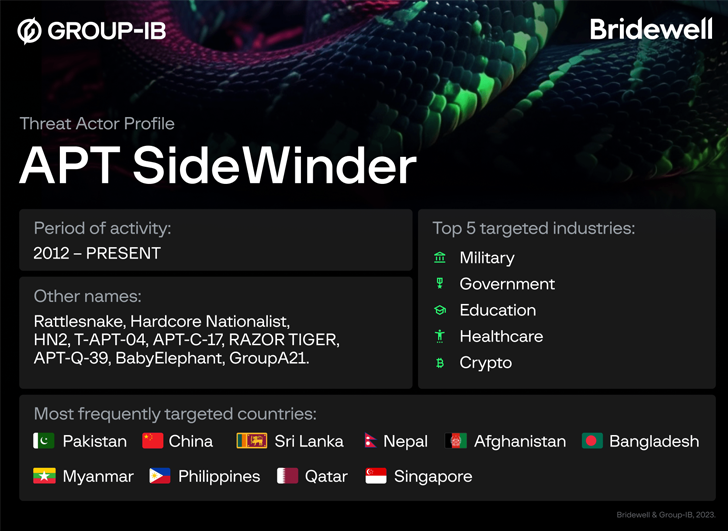
Cybersecurity researchers have unearthed earlier undocumented attack infrastructure applied by the prolific condition-sponsored team SideWinder to strike entities located in Pakistan and China.
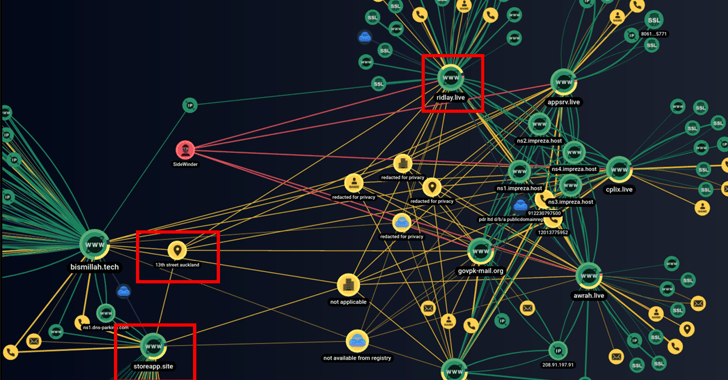
This comprises a network of 55 domains and IP addresses made use of by the threat actor, cybersecurity providers Group-IB and Bridewell said in a joint report shared with The Hacker Information.
“The determined phishing domains mimic different companies in the news, government, telecommunications, and economical sectors,” researchers Nikita Rostovtsev, Joshua Penny, and Yashraj Solanki said.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
SideWinder has been identified to be active considering that at the very least 2012, with attack chains mostly leveraging spear-phishing as an intrusion mechanism to receive a foothold into specific environments.
The goal array of the group is extensively thought to be affiliated with Indian espionage interests. The most often attacked nations involve Pakistan, China, Sri Lanka, Afghanistan, Bangladesh, Myanmar, the Philippines, Qatar, and Singapore.

Previously this February, Team-IB introduced to mild proof that SideWinder may have specific 61 govt, army, legislation enforcement, and other companies throughout Asia among June and November 2021.
Extra just lately, the nation-point out group was observed leveraging a system regarded as server-based polymorphism in evasive attacks concentrating on Pakistani government companies.
The newly found out domains mimic authorities businesses in Pakistan, China, and India and are characterised by the use of the exact values in WHOIS data and equivalent registration facts.
Hosted on some of these domains are govt-themed lure files that are designed to down load an not known future-phase payload.
A vast majority of these paperwork ended up uploaded to VirusTotal in March 2023 from Pakistan. One particular amid them is a Microsoft Word file purportedly from the Pakistan Navy War Faculty (PNWC), which was analyzed by the two QiAnXin and BlackBerry in latest months.
Also uncovered is a Windows shortcut (LNK) file that was uploaded to VirusTotal from Beijing in late November 2022. The LNK file, for its part, is engineered to run an HTML application (HTA) file retrieved from a remote server that spoofs Tsinghua University’s email method (mailtsinghua.sinacn[.]co).
A further LNK file that was uploaded to VirusTotal close to the exact time from Kathmandu employs a identical process to fetch an HTA file from a domain masquerading as a Nepalese authorities internet site (mailv.mofs-gov[.]org).
Even further investigation into SideWinder’s infrastructure has led to the discovery of a destructive Android APK file (226617) that was uploaded to VirusTotal from Sri Lanka in March 2023.
Approaching WEBINARLearn to Halt Ransomware with True-Time Safety
Join our webinar and master how to end ransomware attacks in their tracks with true-time MFA and company account protection.
Help save My Seat!
The rogue Android application passes off as a “Ludo Activity” and prompts end users to grant it access to contacts, place, phone logs, SMS messages, and calendar, successfully performing as spy ware capable of harvesting sensitive details.
Team-IB said the application also displays similarities with the pretend Secure VPN application the corporation disclosed in June 2022 as currently being dispersed to targets in Pakistan by means of a traffic way system (TDS) referred to as AntiBot.
In all, the domains stage to SideWinder setting its sights on fiscal, federal government, and regulation enforcement organizations, as nicely as organizations specializing in e-commerce and mass media in Pakistan and China.
“Like many other APT groups, SideWinder relies on specific spear-phishing as the preliminary vector,” the researchers stated. “It is therefore significant for organizations to deploy company email safety methods that detonate malicious written content.”
Observed this report appealing? Observe us on Twitter and LinkedIn to read through more exceptional content we write-up.
Some parts of this post are sourced from:
thehackernews.com

 U.S. Offers $10 Million Bounty for Capture of Notorious Russian Ransomware Operator
U.S. Offers $10 Million Bounty for Capture of Notorious Russian Ransomware Operator