A new custom made backdoor dubbed Stealth Soldier has been deployed as section of a set of remarkably-specific espionage attacks in North Africa.
“Stealth Soldier malware is an undocumented backdoor that mostly operates surveillance functions these as file exfiltration, display and microphone recording, keystroke logging and thieving browser facts,” cybersecurity firm Verify Point explained in a technical report.
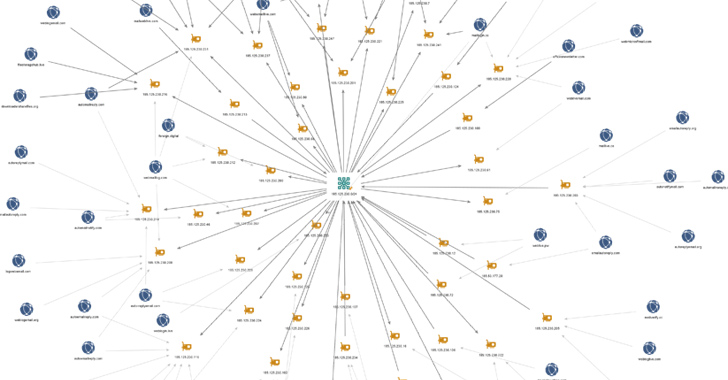
The ongoing operation is characterized by the use of command-and-management (C&C) servers that mimic internet sites belonging to the Libyan Ministry of Overseas Affairs. The earliest artifacts affiliated with the campaign day back again to Oct 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The attacks start with opportunity targets downloading bogus downloader binaries that are shipped by way of social engineering attacks and act as a conduit for retrieving Stealth Soldier, although at the same time displaying a decoy empty PDF file.
The custom made modular implant, which is considered to be utilized sparingly, permits surveillance abilities by accumulating listing listings and browser qualifications, logging keystrokes, recording microphone audio, using screenshots, uploading information, and functioning PowerShell instructions.
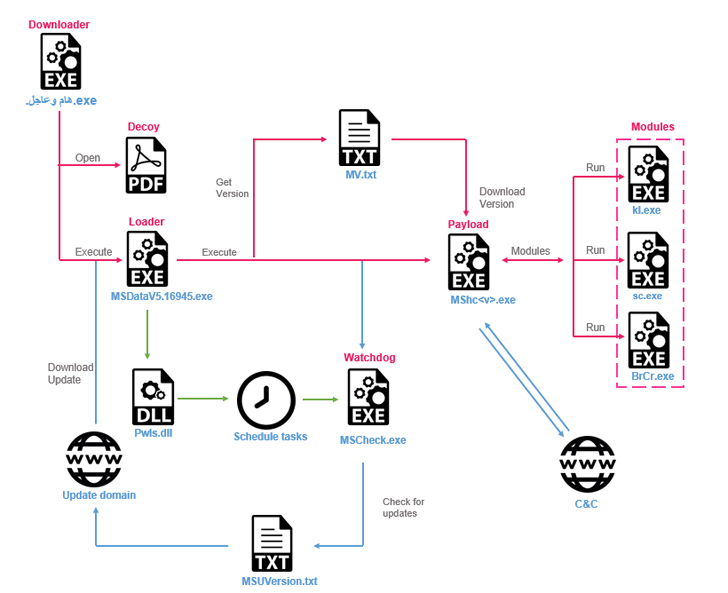
“The malware utilizes unique varieties of commands: some are plugins that are downloaded from the C&C and some are modules inside the malware,” Look at Position explained, including the discovery of three variations of Stealth Soldier implies that it truly is remaining actively preserved by its operators.
Some of the elements are no lengthier offered for retrieval, but the screen seize and browser credential stealer plugins are stated to have been inspired by open up source initiatives out there on GitHub.
Approaching WEBINAR🔐 Mastering API Security: Knowledge Your Real Attack Floor
Discover the untapped vulnerabilities in your API ecosystem and just take proactive measures towards ironclad security. Be part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:right afterdisplay screen:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-leading:2px good #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-excess weight:900text-align:leftline-height:33px.wn-descriptiontextual content-align:leftfont-dimension:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
What is far more, the Stealth Soldier infrastructure exhibits overlaps with infrastructure related with a different phishing campaign dubbed Eye on the Nile, which specific Egyptian journalists and human rights activists in 2019.
The growth alerts the “very first probable re-appearance of this threat actor” because then, suggesting the group is geared toward surveillance against Egyptian and Libyan targets.
“Specified the modularity of the malware and the use of numerous stages of an infection, it is possible that the attackers will keep on to evolve their ways and approaches and deploy new versions of this malware in the in the vicinity of long run,” Look at Place stated.
Found this posting attention-grabbing? Abide by us on Twitter and LinkedIn to read additional exceptional content we article.
Some pieces of this report are sourced from:
thehackernews.com

 Espionage Attacks in North Africa Linked to “Stealth Soldier” Backdoor
Espionage Attacks in North Africa Linked to “Stealth Soldier” Backdoor