A new phishing marketing campaign has established its sights on European entities to distribute Remcos RAT and Formbook through a malware loader dubbed DBatLoader.
“The malware payload is distributed via WordPress sites that have approved SSL certificates, which is a prevalent tactic made use of by threat actors to evade detection engines,” Zscaler scientists Meghraj Nandanwar and Satyam Singh claimed in a report posted Monday.
The findings establish on a earlier report from SentinelOne final month that thorough phishing email messages containing destructive attachments that masquerade as economic paperwork to activate the infection chain.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
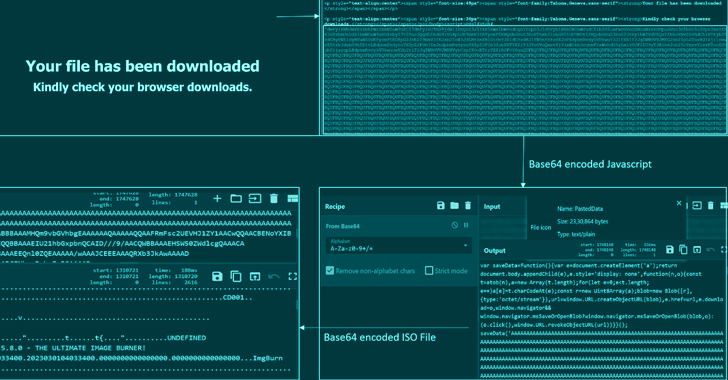
Some of the file formats made use of to distribute the DBatLoader payload issue the use of a multi-layered obfuscated HTML file and OneNote attachments.
The development adds to rising abuse of OneNote documents as an original vector for malware distribution considering the fact that late past 12 months in reaction to Microsoft’s determination to block macros by default in information downloaded from the internet.
DBatLoader, also referred to as ModiLoader and NatsoLoader, is a Delphi-based malware that’s able of delivering adhere to-on payloads from cloud products and services like Google Travel and Microsoft OneDrive, while also adopting graphic steganography strategies to evade detection engines.
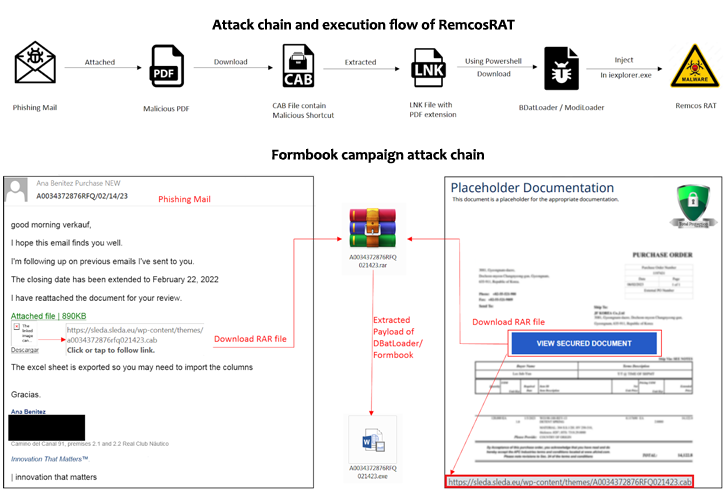
Just one noteworthy aspect of the attack is the use of mock trustworthy directories such as “C:Windows Program32” (note the trailing house just after Windows) to bypass User Account Command (UAC) and escalate privileges.
WEBINARDiscover the Concealed Risks of Third-Party SaaS Applications
Are you conscious of the hazards associated with third-party application accessibility to your company’s SaaS applications? Be a part of our webinar to learn about the styles of permissions being granted and how to reduce risk.
RESERVE YOUR SEAT
A caveat in this article is that the directories can’t be directly designed from inside of the Windows Explorer user interface, rather necessitating the attacker to depend on a script to complete the process and duplicate to the folder a rogue DLL and a reputable executable (easinvoker.exe) that’s susceptible to DLL hijacking in order to load the DLL payload.
This enables the attackers to conduct elevated things to do with no alerting buyers, which include establishing persistence and including the “C:Customers” directory to the Microsoft Defender exclusion list to stay away from getting scanned.
To mitigate pitfalls posed by DBatLoader, it truly is advised to keep track of procedure executions that require filesystem paths with trailing spaces and think about configuring Windows UAC to Constantly notify.
Uncovered this write-up intriguing? Abide by us on Twitter and LinkedIn to go through extra unique articles we publish.
Some components of this report are sourced from:
thehackernews.com

 Four Years Behind Bars for Prolific BEC Scammer
Four Years Behind Bars for Prolific BEC Scammer