The sophisticated persistent menace (APT) team recognized as StrongPity has qualified Android consumers with a trojanized variation of the Telegram app through a phony website that impersonates a video clip chat provider termed Shagle.
“A copycat site, mimicking the Shagle company, is used to distribute StrongPity’s cell backdoor app,” ESET malware researcher Lukáš Štefanko stated in a technological report. “The application is a modified edition of the open up supply Telegram application, repackaged with StrongPity backdoor code.”
StrongPity, also recognized by the names APT-C-41 and Promethium, is a cyberespionage team active because at the very least 2012, with a greater part of its operations concentrated on Syria and Turkey. The existence of the team was initial publicly reported by Kaspersky in Oct 2016.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The menace actor’s strategies have since expanded to encompass a lot more targets across Africa, Asia, Europe, and North The us, with the intrusions leveraging watering hole attacks and phishing messages to activate the killchain.
1 of the principal hallmarks of StrongPity is its use of counterfeit websites that purport to supply a extensive wide variety of program applications, only to trick victims into downloading tainted versions of genuine apps.
In December 2021, Minerva Labs disclosed a 3-phase attack sequence stemming from the execution of a seemingly benign Notepad++ set up file to eventually provide a backdoor on to contaminated hosts.
That very same 12 months, StrongPity was noticed deploying a piece of Android malware for the 1st time by potentially breaking into the Syrian e-government portal and changing the formal Android APK file with a rogue counterpart.
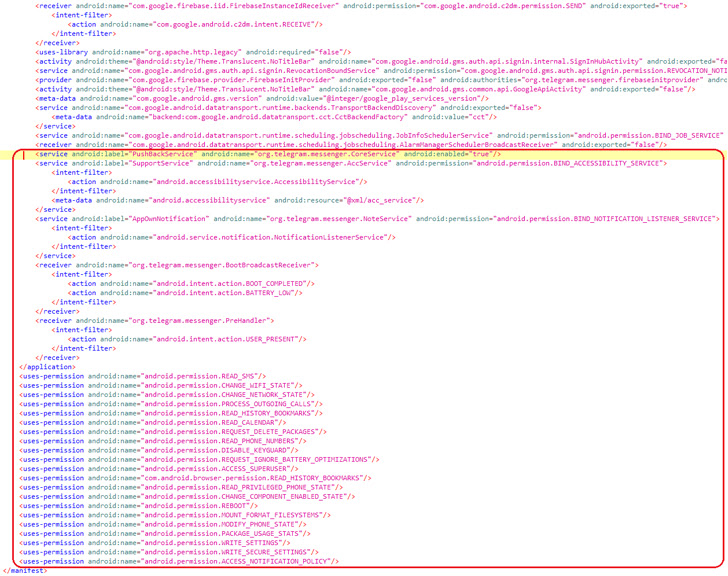
The most current results from ESET highlight a related modus operandi that is engineered to distribute an up-to-date version of the Android backdoor payload, which is geared up to history phone calls, track product destinations, and collect SMS messages, get in touch with logs, contacts lists, and files.
In addition, granting the malware accessibility products and services permissions permits it to siphon incoming notifications and messages from numerous apps like Gmail, Instagram, Kik, LINE, Messenger, Skype, Snapchat, Telegram, Tinder, Twitter, Viber, and WeChat.
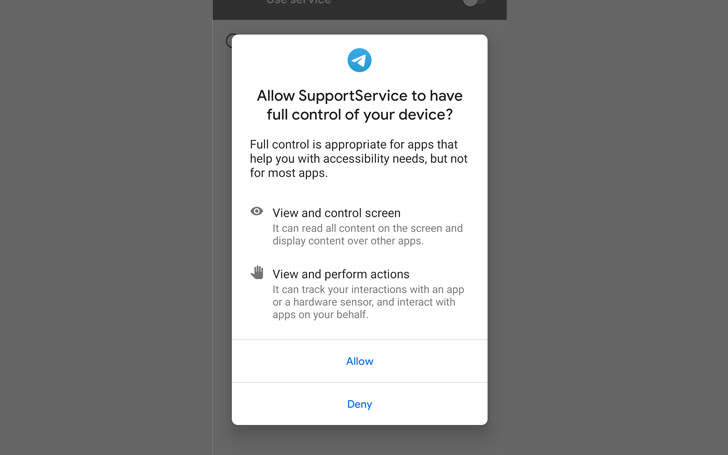
The Slovak cybersecurity organization described the implant as modular and capable of downloading supplemental parts from a remote command-and-handle (C2) server so as to accommodate the evolving aims of StrongPity’s strategies.
The backdoor performance is concealed within just a legitimate model of Telegram’s Android application that was offered for down load all over February 25, 2022. That reported, the bogus Shagle site is no longer active, even though indications are that the exercise is “quite narrowly focused” owing to the lack of telemetry details.
There is also no evidence the application was posted on the formal Google Enjoy Keep. It truly is currently not recognized how the opportunity victims are lured to the phony internet site, and if it involves techniques like social engineering, research motor poisoning, or fraudulent advertisements.
There is also no proof the application (“video clip.apk”) was printed on the formal Google Play Keep. It’s presently not known how the likely victims are lured to the phony internet site, and if it involves strategies like social engineering, look for motor poisoning, or fraudulent adverts.
“The malicious domain was registered on the exact same working day, so the copycat web page and the pretend Shagle app may perhaps have been readily available for down load since that day,” Štefanko pointed out.
One more noteworthy aspect of the attack is that the tampered version of Telegram employs the same package deal identify as the genuine Telegram application, this means the backdoored variant cannot be mounted on a product that currently has Telegram installed.
“This might necessarily mean 1 of two issues – either the danger actor to start with communicates with probable victims and pushes them to uninstall Telegram from their gadgets if it is put in, or the campaign focuses on international locations where Telegram use is exceptional for conversation,” Štefanko explained.
Uncovered this report intriguing? Adhere to us on Twitter and LinkedIn to read through far more unique written content we article.
Some areas of this posting are sourced from:
thehackernews.com


 GitHub Adds Features to Automate Vulnerability Code Scanning
GitHub Adds Features to Automate Vulnerability Code Scanning