Standard perimeter-based mostly security has turn into pricey and ineffective. As a outcome, communications security among men and women, devices, and networks is extra critical than blocking entry with firewalls. On top rated of that, most cybersecurity threats are brought about by just a couple superusers – normally 1 out of 200 users. There’s a organization aiming to deal with the hole concerning common PAM and IdM options and protected your one out of 200 end users – SSH Communications Security.
Your Privileged Obtain Management (PAM) and Id Management (IdM) should perform hand in hand to secure your users’ obtain and identities – common consumers and privileged consumers alike. But classic options struggle to accomplish that.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Let’s appear at what businesses will need to have an understanding of about PAM and IdM and how you can bridge and potential-proof your PAM and IdM.
PIM, PAM, IAM – you will need all a few of them
Privileged Identification Management (PIM), Privileged Entry Administration (PAM), and Id and Access Management (IAM) – all a few are intently related, and you require all a few of them to efficiently take care of and safe your digital identities, buyers and access.
Let us immediately evaluate what PIM, PAM, and IAM concentrate on:
- PIM – management of root user identities and authorizations
- PAM – administration of root user accessibility to critical methods and auditing
- IAM – administration of standard consumer identities, authorizations, and access to resources
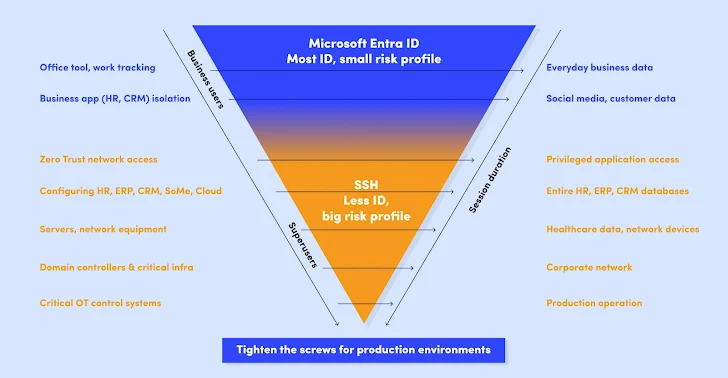
Not all electronic identities are created equal – superusers want tremendous defense
Think about this: Your standard consumer probably requirements access to regular place of work resources, like your CRM or M365. They don’t want obtain to any of your critical belongings.
The identification verification approach should really correspond to this. A common consumer requirements to be confirmed with solid authentication techniques, e.g. Microsoft Entra ID, but there is generally no want to go beyond that.
These typical people variety the bulk of your users, up to 99,5% of them.
On the other hand, you have your privileged substantial-impact buyers – there is only a compact range of them (ordinarily all over just one in 200 consumers), but the power and hazards they have are huge because they can obtain your critical info, databases, infrastructures, and networks.
Similarly, acceptable identity verification treatments should implement. In the scenario of your substantial-impression consumers, you have to have obtain controls that go further than solid id-dependent authentication.
Enter the Zero Rely on – Borderless, Passwordless, Keyless and Biometric Long run
Common answers are not enough to bridge your PAM and IdM. They just won’t be able to tackle the security that you require to shield your critical assets. Nor can they present effective and long term-proof security controls for entry and identities of your regular consumers as properly as large-impact people.
The potential of cybersecurity is borderless, passwordless, keyless, biometric, and Zero Belief.
This usually means that you will need a future-evidence cybersecurity design with no implicitly reliable users, connections, purposes, servers, or gadgets. On leading of that, you require an additional layer of security with passwordless, keyless, and biometric authentication.
Master the worth of utilizing the passwordless and keyless strategy into your cybersecurity from the whitepaper presented by SSH Communications Security.
Found this report intriguing? This post is a contributed piece from one of our valued companions. Comply with us on Twitter and LinkedIn to read extra special material we submit.
Some sections of this short article are sourced from:
thehackernews.com


 TimbreStealer Malware Spreading via Tax-themed Phishing Scam Targets IT Users
TimbreStealer Malware Spreading via Tax-themed Phishing Scam Targets IT Users