Talk to any security expert and they’ll convey to you that remediating pitfalls from a variety of siloed security scanning resources demands a laborous and labor-intensive collection of techniques targeted on deduplication, prioritization, and routing of issues to an acceptable “fixer” someplace in the business. This burden on already source-strapped security teams is an performance killer.
A new study, commissioned by Seemplicity and done by Dark Reading, delivers clean insight into how security execs tackle the demanding remediation lifetime cycle from discovery to resolution. The exploration reveals the obstacles security industry experts encounter when coordinating remediation activities. The details exposes the outcomes — in increased workload and diminished risk posture — that occur from lengthy remediation situations, inefficient and uncontrolled guide processes, the lack of managerial visibility and oversight throughout the risk lifestyle cycle.
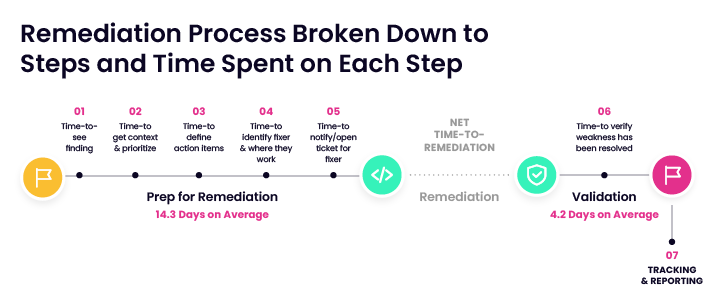 Remediation Method Broken Down to Methods and Time Used on Each Move
Remediation Method Broken Down to Methods and Time Used on Each Move

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The survey, which encompassed 108 cybersecurity pros, at firms with 100 or a lot more staff members, uncovered that:
- It takes nearly 4 months to remediate critical security threats from start out to end. A granular look at the conclusion-to-close risk- reduction method exhibits remediation life cycles continuously calculated in months, not times.
- The ordinary corporation manages 3 to 5 security tools, including complexity and slowing down remediation. The knowledge clarifies that manual jobs and many feeds from disparate scanning instruments conspire to drag down velocity-to-remediation.
- 49% of security industry experts do not know who to get hold of to deal with threats or verify fixes. Finding the right fixer, acquiring a reaction to a remediation request, and verifying productive fixes are best-time customers for most companies.
- 97% would focus on proactive security duties if remediation was economical. Had been there superior and quicker strategies to remediate risks, respondents reported they would expend the time received on forward-seeking pursuits, this sort of as additional architecture critique, threat modeling, and security recognition instruction.

If you can find a single recurring theme in the investigation, it is that the mixture of far too lots of security tools and too a great deal handbook perform staying conducted throughout distinctive teams blocks endeavours to preserve speed with modern risk reduction and remediation workloads for the the vast majority of companies.
The “Point out of Risk Remediation” investigation supplies a roadmap for bettering effectiveness and efficiency, bolstering organizational protection, and minimizing risk — and security team’s sanity.
The report also highlights 3 important actions to strengthening risk reduction:
Down load the complete study report “The Point out of Risk Reduction: A Require for Velocity” below.
Uncovered this posting interesting? Observe us on Twitter and LinkedIn to read through a lot more exclusive material we put up.
Some pieces of this posting are sourced from:
thehackernews.com


 Citrix NetScaler Alert: Ransomware Hackers Exploiting Critical Vulnerability
Citrix NetScaler Alert: Ransomware Hackers Exploiting Critical Vulnerability