Cybersecurity scientists have identified a new info stealer dubbed SYS01stealer focusing on critical authorities infrastructure staff members, production companies, and other sectors.
“The threat actors driving the campaign are concentrating on Fb business enterprise accounts by making use of Google advertisements and phony Fb profiles that promote things like video games, adult content material, and cracked computer software, etcetera. to lure victims into downloading a destructive file,” Morphisec explained in a report shared with The Hacker Information.
“The attack is created to steal sensitive information and facts, such as login knowledge, cookies, and Fb ad and business account information and facts.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The Israeli cybersecurity business said the campaign was in the beginning tied to a fiscally motivated cybercriminal operation dubbed Ducktail by Zscaler.
Nonetheless, WithSecure, which first documented the Ducktail action cluster in July 2022, mentioned the two intrusion sets are different from a person one more, indicating how the threat actors managed to confuse attribution efforts and evade detection.
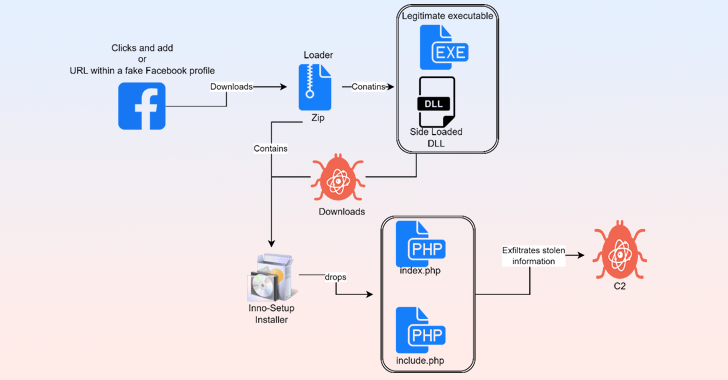
The attack chain, for each Morphisec, commences when a victim is productively lured into clicking on a URL from a pretend Facebook profile or advertisement to obtain a ZIP archive that purports to be cracked software package or grownup-themed articles.
Opening the ZIP file launches a based mostly loader – generally a reputable C# application – which is susceptible to DLL side-loading, thus earning it feasible to load a malicious dynamic backlink library (DLL) file along with the app.
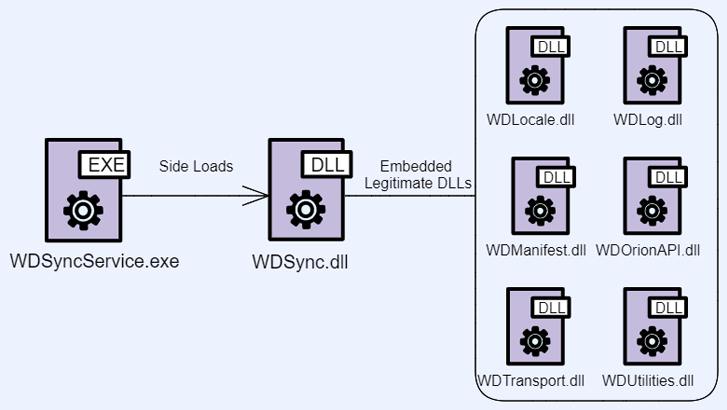
Some of the purposes abused to aspect-load the rogue DLL are Western Digital’s WDSyncService.exe and Garmin’s ElevatedInstaller.exe. In some scenarios, the aspect-loaded DLL functions as a signifies to deploy Python and Rust-primarily based intermediate executables.
Irrespective of the approach employed, all roadways lead to the shipping of an installer that drops and executes the PHP-based mostly SYS01stealer malware.
The stealer is engineered to harvest Fb cookies from Chromium-based mostly web browsers (e.g., Google Chrome, Microsoft Edge, Courageous, Opera, and Vivaldi), exfiltrate the victim’s Facebook facts to a remote server, and down load and run arbitrary information.
Find the Most current Malware Evasion Tactics and Prevention Strategies
Ready to bust the 9 most harmful myths about file-based mostly attacks? Be part of our future webinar and turn out to be a hero in the fight in opposition to affected individual zero infections and zero-day security activities!
RESERVE YOUR SEAT
It really is also outfitted to add files from the infected host to the command-and-handle (C2) server, run commands sent by the server, and update itself when a new version is offered.
The improvement comes as Bitdefender uncovered a identical stealer campaign identified as S1deload which is made to hijack users’ Facebook and YouTube accounts and leverage the compromised methods to mine cryptocurrency.
“DLL side-loading is a extremely effective procedure for tricking Windows devices into loading malicious code,” Morphisec stated.
“When an application hundreds in memory and lookup purchase is not enforced, the software masses the malicious file in its place of the legit 1, permitting danger actors to hijack respectable, trustworthy, and even signed programs to load and execute malicious payloads.”
Identified this posting intriguing? Abide by us on Twitter and LinkedIn to examine a lot more distinctive written content we publish.
Some elements of this posting are sourced from:
thehackernews.com

 Just 10% of Firms Can Resolve Cloud Threats in an Hour
Just 10% of Firms Can Resolve Cloud Threats in an Hour