A danger actor tracked as TA547 has specific dozens of German companies with an details stealer termed Rhadamanthys as portion of an bill-themed phishing marketing campaign.
“This is the 1st time scientists observed TA547 use Rhadamanthys, an information and facts stealer that is used by many cybercriminal risk actors,” Proofpoint mentioned. “Furthermore, the actor appeared to use a PowerShell script that researchers suspect was produced by a big language design (LLM).”
TA547 is a prolific, monetarily inspired threat actor that is recognized to be lively because at least November 2017, applying email phishing lures to produce a range of Android and Windows malware these types of as ZLoader, Gootkit, DanaBot, Ursnif, and even Adhubllka ransomware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In modern decades, the group has progressed into an first accessibility broker (IAB) for ransomware attacks. It has also been noticed utilizing geofencing tricks to prohibit payloads to unique locations.

The email messages observed as component of the most recent marketing campaign impersonate the German organization Metro AG and include a password-safeguarded ZIP file that contains a ZIP archive that, when opened, initiates the execution of a remote PowerShell script to launch the Rhadamanthys stealer directly in memory.
Interestingly, the PowerShell script employed to load Rhadamanthys includes “grammatically suitable and hyper unique feedback” for every instruction in the program, increasing the likelihood that it may possibly have been produced (or rewritten) making use of an LLM.
The alternate speculation is that TA547 copied the script from another supply that had made use of generative AI technology to build it.
“This marketing campaign represents an case in point of some approach shifts from TA547 including the use of compressed LNKs and previously unobserved Rhadamanthys stealer,” Proofpoint reported. “It also gives insight into how risk actors are leveraging probable LLM-generated written content in malware campaigns.”
The growth comes as phishing campaigns have also been banking on unheard of strategies to facilitate credential-harvesting attacks. In these email messages, recipients are notified of a voice message and are directed to click on on a hyperlink to entry it.
The payload retrieved from the URL is seriously obfuscated HTML content that runs JavaScript code embedded in an SVG image when the web site is rendered on the focus on procedure.
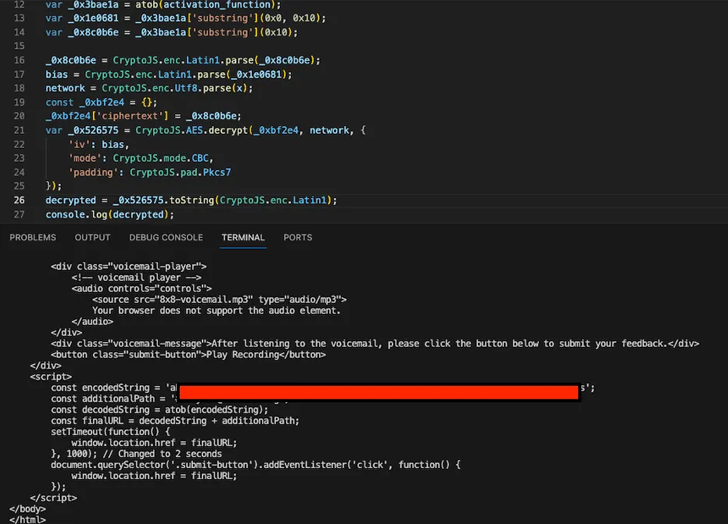
Current in the SVG information is “encrypted information containing a next stage web page prompting the focus on to enter their credentials to accessibility the voice message,” Binary Protection explained, introducing the site is encrypted utilizing CryptoJS.
Other email-based attacks have paved the way for Agent Tesla, which has emerged as an desirable possibility for risk actors due to it “staying an very affordable malware support with numerous abilities to exfiltrate and steal users’ data,” according to Cofense.
Social engineering campaigns have also taken the variety of malicious advertisements served on research engines like Google that entice unsuspecting users into downloading bogus installers for popular computer software like PuTTY, FileZilla, and Room Planner to eventually deploy Nitrogen and IDAT Loader.

The infection chain associated with IDAT Loader is noteworthy for the point that the MSIX installer is made use of to launch a PowerShell script that, in flip, contacts a Telegram bot to fetch a second PowerShell script hosted on the bot.
This PowerShell script then functions as a conduit to provide an additional PowerShell script which is employed to bypass Windows Antimalware Scan Interface (AMSI) protections as properly as bring about the execution of the loader, which subsequently proceeds to load the SectopRAT trojan.
“Endpoints can be safeguarded from destructive ads by using team policies that prohibit traffic coming from the key and lesser recognized advertisement networks,” Jérôme Segura, principal threat researcher at Malwarebytes, explained.
Identified this write-up interesting? Comply with us on Twitter and LinkedIn to study more special information we write-up.
Some pieces of this post are sourced from:
thehackernews.com


 Apple Updates Spyware Alert System to Warn Victims of Mercenary Attacks
Apple Updates Spyware Alert System to Warn Victims of Mercenary Attacks