A persistent intrusion marketing campaign has set its eyes on telecommunications and business enterprise method outsourcing (BPO) organizations at lease because June 2022.
“The stop objective of this campaign seems to be to obtain obtain to mobile carrier networks and, as evidenced in two investigations, carry out SIM swapping activity,” CrowdStrike researcher Tim Parisi reported in an evaluation posted last 7 days.
The economically motivated attacks have been attributed by the cybersecurity company to an actor tracked as Scattered Spider.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Initial access to the goal atmosphere is mentioned to be undertaken via a range of approaches ranging from social engineering utilizing phone calls and messages despatched by way of Telegram to impersonate IT personnel.
This technique is leveraged to direct victims to a credential harvesting website or trick them into setting up business remote monitoring and administration (RMM) applications like Zoho Assist and Getscreen.me.
Ought to the focus on accounts be secured by two-factor authentication (2FA), the risk actor both confident the victim into sharing the 1-time password or employed a technique referred to as prompt bombing, which was place to use in the recent breaches of Cisco and Uber.
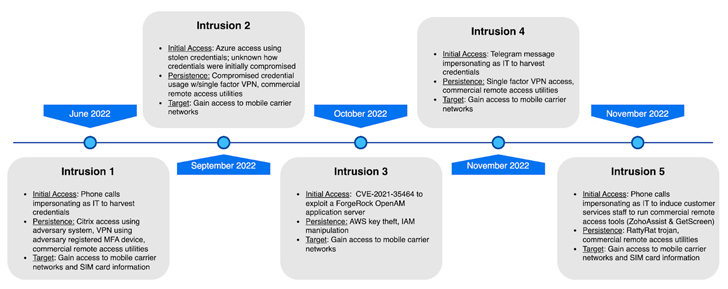
In an different an infection chain observed by CrowdStrike, a user’s stolen credentials formerly received through unknown signifies were being applied by the adversary to authenticate to the organization’s Azure tenant.
An additional occasion concerned the exploitation of a critical distant code execution bug in ForgeRock OpenAM entry administration solution (CVE-2021-35464) that came less than lively exploitation previous year.
Quite a few of the attacks also involved Scattered Spider attaining obtain to the compromised entity’s multi-factor authentication (MFA) console to enroll their have products for persistent remote access by way of respectable remote entry equipment to prevent raising red flags.
First obtain and persistence actions are followed by reconnaissance of Windows, Linux, Google Workspace, Azure Active Directory, Microsoft 365, and AWS environments as effectively as conducting lateral movement, when also downloading more applications to exfiltrate VPN and MFA enrollment facts in pick cases.
“These strategies are particularly persistent and brazen,” Parisi pointed out. “At the time the adversary is contained or operations are disrupted, they right away go to focus on other corporations in the telecom and BPO sectors.”
Discovered this article interesting? Follow us on Twitter and LinkedIn to read more exclusive written content we submit.
Some pieces of this posting are sourced from:
thehackernews.com


 Russian Hackers Use Western Networks to Attack Ukraine
Russian Hackers Use Western Networks to Attack Ukraine