Disclaimer: This article is meant to give insight into cyber threats as noticed by the group of customers of CrowdSec.
What can tens of 1000’s of machines notify us about illegal hacker routines?
Do you don’t forget that scene in Batman – The Dark Knight, the place Batman employs a technique that aggregates active seem details from countless cellular telephones to create a meta sonar feed of what is likely on at any provided area?

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It is an attention-grabbing analogy with what we do at CrowdSec. By aggregating intrusion alerts from our community, we can present a distinct picture of what is likely on in phrases of unlawful hacking in the globe.
Following 2 decades of activity and analyzing 1 million intrusion indicators each day from tens of thousands of end users in 160 nations around the world, we commence getting an exact “Batman sonar” international feed of cyber threats. And there are some fascinating takeaways to define.
A cyber risk with several faces
Initial of all, the world wide cyber risk is very functional. What do we see when searching at the types of attacks reported, their origin, and the Autonomous Methods (AS) behind the destructive IP addresses?
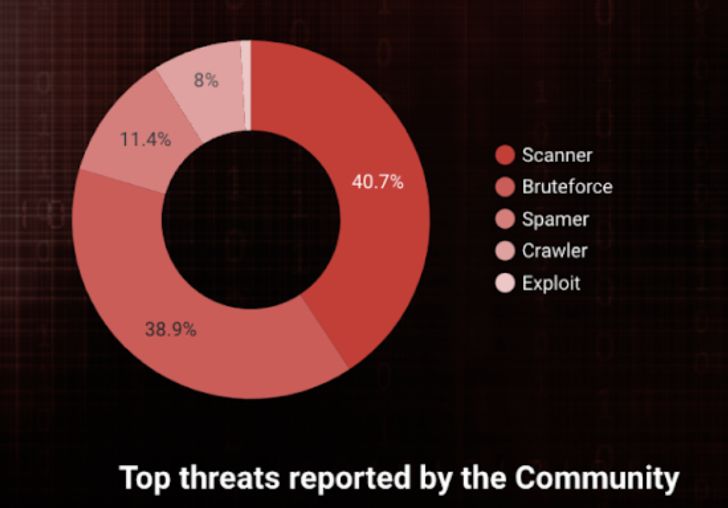
Scanners and Brute force tries are continue to the most popular intrusion vectors our neighborhood sees and rank #1. Pretty logic, as surveillance is the 1st phase to a a lot more sophisticated intrusion. The scanning actions seen by our community are largely port scans or HTTP-primarily based probings.
Amongst the diverse intrusion styles applied by hackers, brute drive makes an attempt on sensitive solutions (SSH, email, admin URLs, etcetera.) is #2. Not breakthrough facts, but when studies clearly show that brute drive attacks are accounted for 6% of cyber attacks in the globe, it is not shocking to see it as dominant, primarily considering that it is nonetheless 1 of the least complicated and most economical kinds to automate and deploy (hello script kiddies). Simply because it is quite effortless to counter, one particular would consider it hardly ever works, but hey, 6%!
Log4J is nevertheless not but a accomplished deal
Among the most preferred exploit tries our group sees, we have Log4j. You indeed appreciated last year’s storm on how a straightforward open up-supply logging utility for Apache with a vulnerability took around the cybersecurity globe and brought on endless headaches to cybersecurity specialists. And, of training course, the criminal earth was extra than happy to exploit it with automated scanning bots searching for vulnerable providers.
Well, our local community has witnessed the storm. Once the December peak adhering to the disclosure handed, items calmed down a small bit, but scanning functions for Log4j begun again, even though at a decreased but continual stage, fueled by bots.
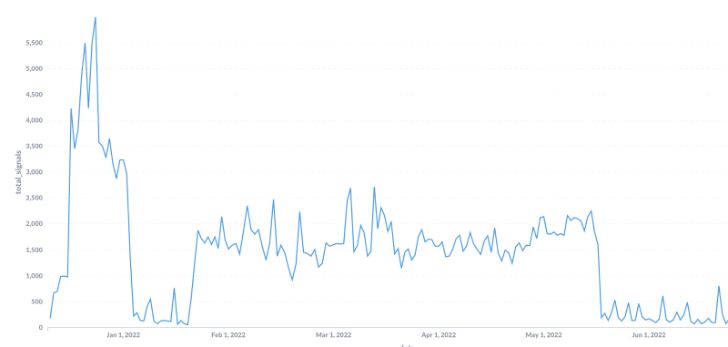
The crucial message is that if you believe you are safeguarded since the “internet marketing” storm handed, believe two times.
There is nevertheless a incredibly intense action looking to use the vulnerability.
For occasion, a pair of weeks in the past, a massive spectrum of our local community was scanned as the IP handle 13.89.48.118 was claimed by additional than 500 end users in significantly less than 12 hrs. It joined 20000+ other IP addresses on the community blocklist for remediation.
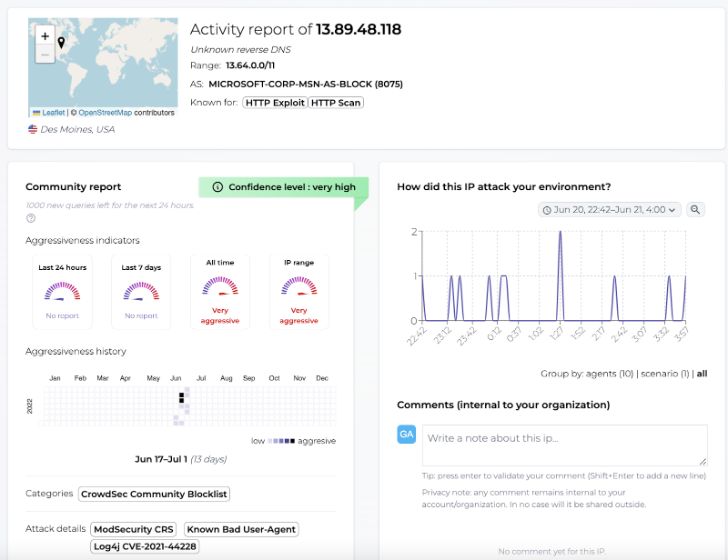
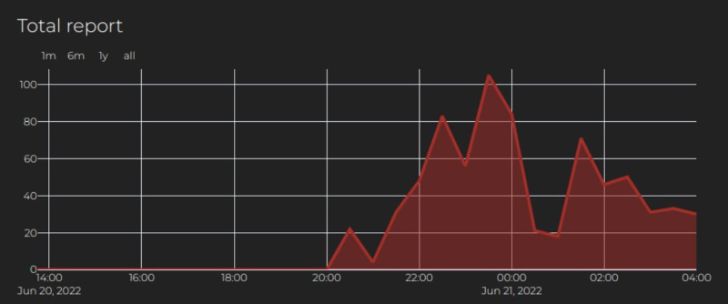
IP addresses: cyber criminals’ core source
IP addresses are almost never malevolent permanently and their status can modify from just one day to a further. With the community consistently sharing information and facts on them, any update can be instantaneously transferred to customers. In the extensive operate, it offers a must have info on the aggressiveness period of IP addresses.
This is a snapshot of the variety of IP addresses that landed in the CrowdSec knowledge lakes (flagged as malicious). What is exciting to note is that cybercriminals are without a doubt shifting the IPs they are utilizing to commit their attacks:
* only 2,79% of these are lasting customers of our databases
* 12,63% of all gathered IPs transform every single 7 days
* The day-to-day renewal fee sits at 1.8%

**Autonomous units have various ways to mitigating compromised IPs**
Each and every IP is element of a pool of addresses managed by an AS (Autonomous Technique). An AS is an comprehensive network or team of networks that have a unified routing policy. Just about every pc or unit that connects to the Internet is connected to an AS. Commonly, every AS is operated by a solitary big corporation, these types of as an Internet assistance provider (ISP), a substantial company technology company, a university, or a governing administration agency, and is, as these types of, dependable for the IP addresses.
Every single intense IP shared by the CrowdSec neighborhood is enriched by its AS. This, merged with the data on aggressiveness duration, can provide a distinct photograph of how AS deal with compromised IPs.
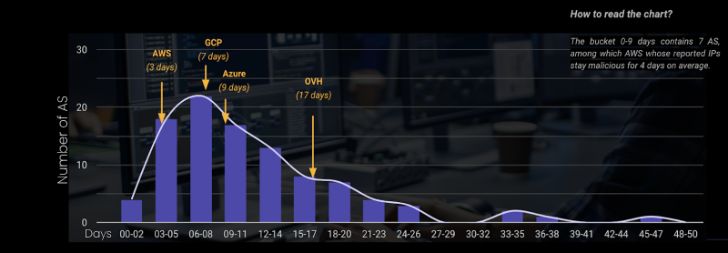
Though looking basically at the amount of compromised property could possibly be an angle, it would not be necessarily reasonable. Not all operators are equivalent in measurement, and some are hosting “riskier” services (hello there out-of-date PHP CMS) than other people.
The ordinary malevolent duration of all the IPs in the same AS implies the operator’s thanks diligence in identifying and dealing with compromised assets. The distribution of the normal duration is proven with arrows pointing to the placement of the most noted AS for the foremost cloud vendors. For instance, at AWS, compromised addresses remain compromised for an average of 3 times. Azure 9 days. At the conclusion of the chart, AS from China or Russia (surprise…) “are a lot less brief” to act on compromised IPs.
This posting is meant to give an overview of the risk action and intelligence CrowdSec people see everyday. You should seek advice from the total variation of the report right here if you want additional information.
Identified this report appealing? Comply with THN on Fb, Twitter and LinkedIn to study much more unique material we article.
Some elements of this post are sourced from:
thehackernews.com


 FBI and MI5 Bosses Warn of “Massive” China Threat
FBI and MI5 Bosses Warn of “Massive” China Threat