Ransomware: modern day threats, how to avert them and how the FBI can help
In April 2021, Dutch supermarkets faced a foods shortage. The result in wasn’t a drought or a unexpected surge in the demand for avocados. Instead, the purpose was a ransomware attack. In the earlier a long time, providers, universities, faculties, health care facilities and other organizations have been specific by ransomware threat actors, turning ransomware into the internet’s most severe security disaster.
The Ransomware Landscape
Ransomware has existed for far more than 30 many years, but it became a lucrative resource of income for cyber actors and gangs in the earlier ten years. Considering that 2015, ransomware gangs have been targeting companies in its place of people. As a result, ransom sums have amplified appreciably, reaching millions of pounds.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Ransomware is efficient due to the fact it pressures victims in two, complementary means. 1st, by threatening victims to ruin their data. Next, by threatening to publicize the attack. The second threat has an indirect affect, still it is just as significant (if not much more). Publication could induce regulatory and compliance issues, as nicely as detrimental prolonged-term manufacturer outcomes.
Here are some examples of genuine ransomware notes:
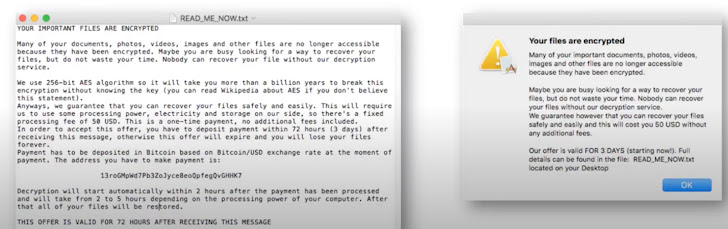
Ransomware as a Service (RaaS) has develop into the most popular type of ransomware. In RaaS attacks, the ransomware infrastructure is formulated by cyber criminals and then certified out to other attackers for their use. The buyer attackers can fork out for the use of computer software or they can break up the loot with the creators. Etay maor, Senior Director Security Approach at Cato Networks commented, “There are other types of RaaS. Immediately after obtaining the ransomware payment some Ransomware groups offer all the knowledge about the victim’s network to other gangs. This implies the next attack is significantly easier and can be fully automated as it does not need weeks of discovery and network analysis by the attackers.”
Some of the big RaaS gamers, who are infamous for turning the RaaS landscape into what it is these days, are CryptoLocker, who contaminated around a quarter million techniques in the 2000s and profited more than $3 million in much less than 4 months, CryptoWall, who produced above $18 million and prompted an FBI advisory, and ultimately Petya, NotPetya and WannaCry who utilised many kinds of exploits, ransomware included.
How the FBI Assists Combat Ransomware
An organization below attack is bound to working experience aggravation and confusion. One of the to start with recommended programs of motion is to get in touch with an Incident Reaction team. The IR staff can guide with investigation, recuperation and negotiations. Then, the FBI can also enable.
Aspect of the FBI’s mission is to elevate recognition about ransomware. Many thanks to a huge neighborhood and global network, they have entry to beneficial intelligence. This information can support victims with negotiations and with operationalization. For instance, the FBI could be in a position to give profiler information and facts about a danger actor centered on its Bitcoin wallet.
To assist ransomware victims and to avert ransomware, the FBI has established up 56 Cyber Activity Forces across its area places of work. These Task Forces get the job done carefully with the IRS, the Office of Education, the Office environment of Inspector Normal, the Federal Protecting Support and the Point out Police. They’re also in near call with the Top secret Services and have accessibility to regional forensics labs. For National Security cyber crimes, the FBI has a specified Squad.
Along with the Cyber Endeavor Pressure, the FBI operates a 24/7 CyWatch, which is a Look at Middle for coordinating the field workplaces, the non-public sector and other federal and intelligence companies. There is also an Internet Crime Grievance Heart, ic3.gov, for registering grievances and determining developments.
Protecting against Ransomware Attacks On Time
Numerous ransomware attacks do not have to attain the issue where by the FBI is desired. Rather, they can be averted beforehand. Ransomware is not a solitary-shot attack. Alternatively, a series of ways and tactics all add to its execution. By pinpointing the network and security vulnerabilities in progress that enables the attack, organizations can block or restrict menace actors’ capability to conduct ransomware. Etay Maor added “We need to rethink the concept that “the attackers want to be right just as soon as, the defenders will need to be appropriate all the time”. A cyber attack is a mixture of many methods and techniques. As these types of, it can only be countered with a holistic approach, with multiple converged security programs that all share context in true time. This is exactly what a SASE architecture, and no other, features the defenders”.
For example, here are all the measures in a REvil attack on a well-regarded company, mapped out to the MITRE ATT&CK framework. As you can see, there are quite a few phases that took place right before the real ransom and had been important to its “results”. By mitigating those threats, the attack might have been prevented.
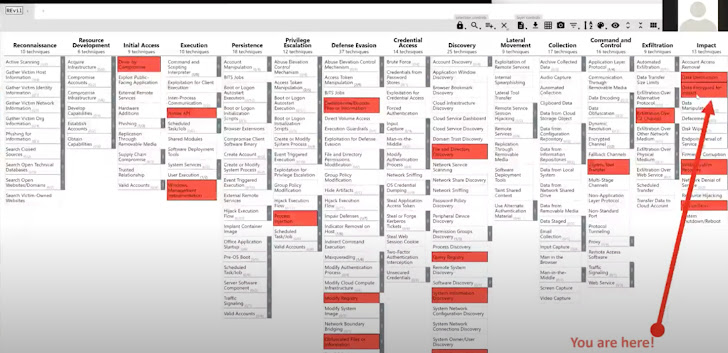
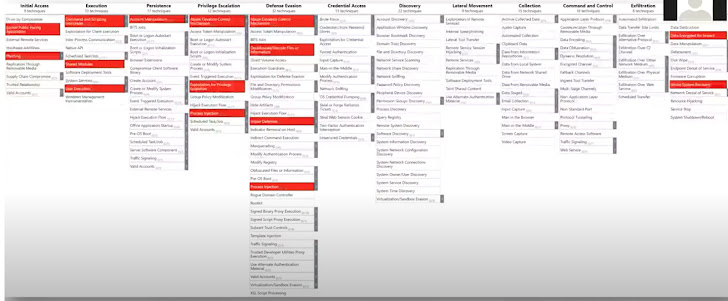
Below is a similar mapping of a Sodinokobi attack:
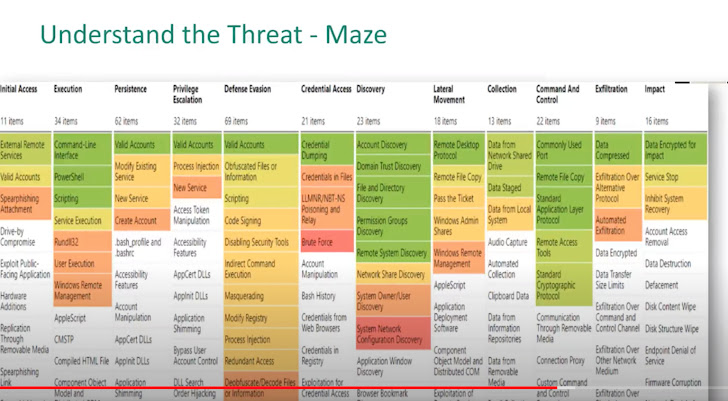
Maze attack mapping to the MITRE framework:

Yet another way to map ransomware attacks is by means of heat maps, which show how often different ways and techniques are made use of. Listed here is a warmth map of Maze attacks:
A single way to use these mappings is for network evaluation and systems testing. By tests a system’s resilience to these tactics and techniques and utilizing controls that can mitigate any pitfalls, businesses minimize the risk of a ransomware attack by a particular actor on their critical methods.
How to Avoid Attacks – From the Horse’s Mouth
But you should not get our phrase for it. Some ransomware attackers are “variety” enough to give businesses with most effective tactics for securing by themselves from foreseeable future ransomware attacks. Tips involve:
- Turning off neighborhood passwords
- Utilizing safe passwords
- Forcing the end of admin periods
- Configuring group guidelines
- Examining privileged users’ access
- Making certain only necessary programs are functioning
- Limiting the reliance of Anti-Virus
- Putting in EDRs
- 24 hour procedure admins
- Securing vulnerable ports
- Observing for misconfigured firewalls
- And much more
Etay Maor of Cato Networks highlights “Almost nothing in what quite a few Ransomware teams say corporations need to do is new. These greatest procedures have been talked about for decades. The rationale they still perform is that we check out to utilize them using disjoint, stage answers. That didn’t operate and will not function. A SASE, cloud native, architecture, where all security alternatives share context and have the functionality to see each networks movement and get a holistic look at of the attack lifecycle can degree the playing subject towards cyber attacks”.

Ransomware Avoidance: An Ongoing Action
Just like brushing your tooth or working out, security hygiene is an ongoing, methodical follow. Ransomware attackers have been acknowledged to revisit the criminal offense scene and demand from customers a next ransom, if issues haven’t been resolved. By using security controls that can proficiently mitigate security threats and obtaining a proper incident response plan in place, the hazards can be minimized, as properly as the attackers’ pay out day. The FBI is below to help and give facts that can support, let’s hope that help won’t be desired.
To master extra about ransomware attacks and how to protect against them, Cato Networks’ Cyber Security Masterclass sequence is offered for your viewing.
Observed this report appealing? Stick to us on Twitter and LinkedIn to read through a lot more exceptional information we put up.
Some sections of this post are sourced from:
thehackernews.com

 Malicious PyTorch Package Downloaded Thousands of Times
Malicious PyTorch Package Downloaded Thousands of Times