There is a seemingly hardly ever-ending quest to obtain the suitable security resources that offer the correct abilities for your business.
SOC groups have a tendency to spend about a third of their day on activities that really don’t pose any danger to their business, and this has accelerated the adoption of automatic answers to get the place of (or increase) inefficient and cumbersome SIEMs.
With an approximated 80% of these threats remaining frequent across most companies, present day SOCs are capable to confidently rely on automation to address this massive proportion of danger signals.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
But, while it is real that automation can tremendously improve the efficiency and success of security groups, it will hardly ever be able to address all detection and response use conditions infallibly.
In the just lately launched GigaOm Radar for Autonomous Security Operations Heart (SOC), they accurately state that “the SOC will not—and ought to not—be absolutely autonomous.”
As much more distributors attempt to obstacle the dominant players in the SIEM group, desire is escalating for answers that offer automation, which can protect 80%, while also presenting customization abilities to deal with bespoke use cases – the remaining 20%.
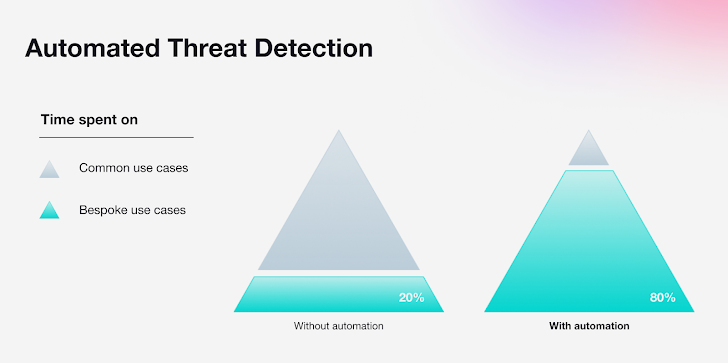 Automation can free of charge up important time for security teams, so they can expend the vast majority of their time on use cases distinctive to their organization.
Automation can free of charge up important time for security teams, so they can expend the vast majority of their time on use cases distinctive to their organization.
THE 80%: AUTOMATION
With the continuous surge in worldwide facts creation, corporations are inevitably viewing an uptick in the variety of alerts managed by security groups.
This may perhaps feel challenging for overworked security teams, but superior seller choices are implementing automation across several stages of the SOC workflow, assisting groups enhance their velocity and efficiency.
The 4 crucial phases the place we are viewing automation are:
- Details Ingestion and Normalization: Automating data ingestion and normalization enables teams to procedure large amounts of knowledge from numerous sources successfully, creating a robust basis for subsequent automatic processes.
- Detection: Transferring the accountability of producing a important part of detection rules makes it possible for security analysts to concentrate on threats distinctive to their firm or market place phase.
- Investigation: Automation can alleviate the load of manual and repetitive jobs, expediting investigation and triage processes.
- Reaction: Automatic responses to recognized and learned threats facilitate swift and correct mitigation. This can consist of connectivity to situation management, SOAR answers, ITSM, etcetera.
Present day SIEM substitution vendors, these kinds of as Hunters, leverage pre-constructed detection principles, integrate threat intelligence feeds, and immediately enrich and cross-correlate qualified prospects. These automated procedures alleviate big quantities of monotonous workloads, empowering security teams to conveniently handle the massive the vast majority of alerts.
 Computerized enrichment and cross-correlation make extensive stories, earning monitoring lateral actions much extra economical.
Computerized enrichment and cross-correlation make extensive stories, earning monitoring lateral actions much extra economical.
THE 20%: CUSTOMIZATION
Though automating the earlier mentioned phases of the workflow have been substantial in boosting efficiencies for quite a few SOCs, there will always remain the have to have for a specified degree of customization.
Every single group has bespoke needs and specifications dependent on field- or firm-certain use situations. This indicates that even if automated and designed-in abilities can handle 80% of the general use situations and tasks, supplemental abilities are wanted to cover the remaining 20%.
“Customization” can necessarily mean a ton of distinctive points, but the most important requirement for security groups is that they have the two the overall flexibility to go over distinctive use conditions and the capacity to scale their capabilities. Let’s glance at a few examples of use scenarios where this can be beneficial:
- Ingesting customized data resources: each and every organization has many data resources they ingest with unique log formats. Lots of vendors may well not have pre-built integrations to ingest from every single solitary info source, so if a vendor does offer that functionality, it can be a huge raise. This is specifically for corporations that are presently using (or will before long be going to) info lakes to sustain information for various applications.
- Detection-as-code: this has grow to be a substantial buzzword in the security marketplace, but with good cause. Detection-as-code provides a selection of rewards for detection engineers, like improved and effective advancement lifecycle, and for huge organizations to additional effectively control multi-tenancy environments. If you usually are not acquainted with the concept, detection-as-code utilizes APIs and deployment pipelines to present wished-for auditing capabilities, generating the progress lifecycle for security operations much nearer to that of regular software enhancement. This approach enhances procedures to assist teams establish bigger-top quality alerts or reuse code within your corporation so you do not have to make every single new detector from scratch. It also allows push detection engineering remaining in the advancement lifecycle, taking away the require to manually examination and deploy detectors.
- Scalable small business context: Whether or not it be entities with unique sensitivity stages (like crown jewels), data from various business enterprise units or different geographies, or siloed information from unique resources, it normally takes a ton of time and exertion to piece jointly data in a way which is easy to understand and actionable. Leveraging an SIEM substitute that gives you the ability to regulate all this by using API delivers expanded efficiencies and scalability that not each and every seller gives.
Conclusion
Building out an efficient SOC has usually been, and will proceed to be, a nuanced effort.
There is no one particular-sizing-suits-all remedy when it will come to security resources. It is essential to offer ways for businesses to not just personalize for their use scenarios, but it is essential that they are equipped to incorporate this “customization” with the now current automatic capabilities that sellers give.
It has develop into a necessity to glance for sellers that can present each a palms-on method to customizing applications, but to do so in a way to bolster the autonomous parts of their offerings.
SIEM replacement vendors like Hunters, which have been named leaders in GigaOm’s formerly mentioned report on autonomous SOC, are regarded for their effortless-to-use and pre-designed capabilities. And, to ensure that they provide the wants of security teams, are continuing to insert impressive customization attributes that permit organizations to tailor their security approach to their exclusive specifications.
Covering the 80% is essential, but addressing the remaining 20% will established your security workforce higher than the rest.
Found this post intriguing? Comply with us on Twitter and LinkedIn to read extra exceptional articles we submit.
Some components of this post are sourced from:
thehackernews.com


 Alert: ‘Effluence’ Backdoor Persists Despite Patching Atlassian Confluence Servers
Alert: ‘Effluence’ Backdoor Persists Despite Patching Atlassian Confluence Servers