Google has removed two new malicious dropper apps that have been detected on the Play Retail outlet for Android, 1 of which posed as a way of life application and was caught distributing the Xenomorph banking malware.
“Xenomorph is a trojan that steals qualifications from banking apps on users’ units,” Zscaler ThreatLabz researchers Himanshu Sharma and Viral Gandhi explained in an assessment revealed Thursday.
“It is also able of intercepting users’ SMS messages and notifications, enabling it to steal just one-time passwords and multi-factor authentication requests.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The cybersecurity firm stated it also observed an expenditure tracker application that exhibited similar conduct, but observed that it could not extract the URL employed to fetch the malware artifact.
The two malicious applications are as follows –
- Todo: Working day manager (com.todo.daymanager)
- 経費キーパー (com.setprice.costs)
The two the applications operate as a dropper, that means the apps them selves are harmless and are a conduit to retrieve the true payload, which, in the situation of Todo, is hosted on GitHub.

Xenomorph, initially documented by ThreatFabric previously this February, is acknowledged to abuse Android’s accessibility permissions to perform overlay attacks, whereby bogus login screens are offered atop legit financial institution applications to steal victim’s credentials.
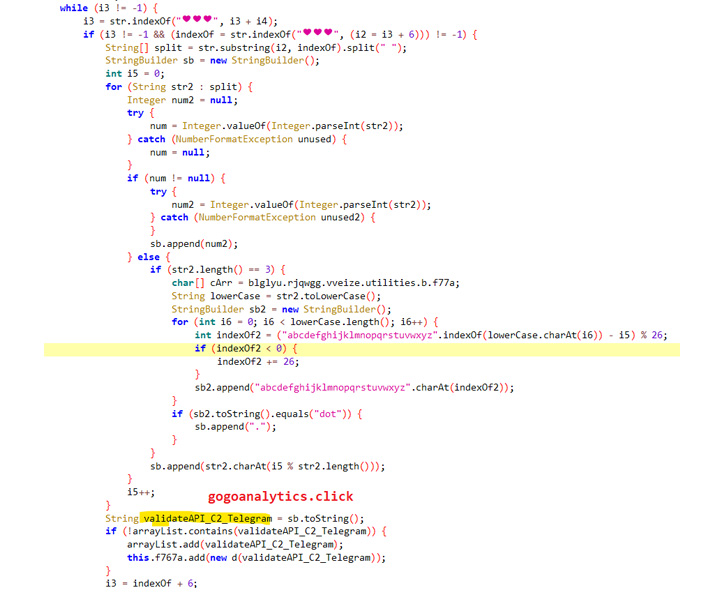
What is extra, the malware leverages a Telegram channel’s description to decode and construct the command-and-control (C2) domain made use of to get extra instructions.
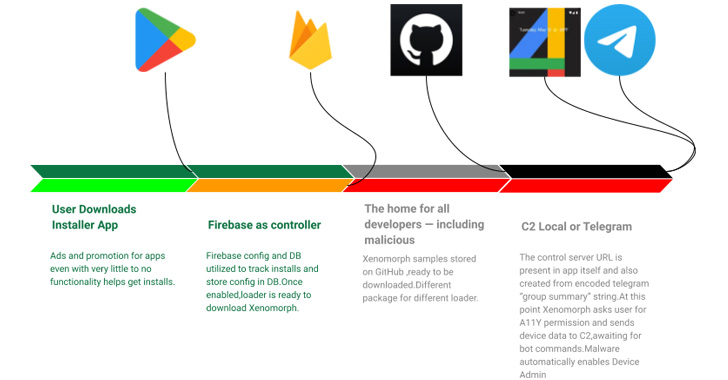
The development follows the discovery of 4 rogue applications on Google Participate in that have been uncovered directing victims to destructive websites as element of an adware and information and facts-thieving campaign. Google informed The Hacker Information that it has due to the fact banned the developer.
Uncovered this post interesting? Adhere to THN on Fb, Twitter and LinkedIn to read through a lot more special content we article.
Some pieces of this write-up are sourced from:
thehackernews.com

 VPN vs. DNS Security
VPN vs. DNS Security