Development Software package on Thursday disclosed a 3rd vulnerability impacting its MOVEit Transfer software, as the Cl0p cybercrime gang deployed extortion methods in opposition to influenced corporations.
The new flaw, which is nonetheless to be assigned a CVE identifier, also considerations an SQL injection vulnerability that “could direct to escalated privileges and probable unauthorized accessibility to the atmosphere.”
The corporation is urging all its customers to disable all HTTP and HTTPs targeted visitors to MOVEit Transfer on ports 80 and 443 to safeguard their environments while a patch is staying well prepared to address the weak spot.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The revelation arrives a week after Progress divulged a further set of SQL injection vulnerabilities (CVE-2023-35036) that it said could be weaponized to access the application’s databases content.
The vulnerabilities sign up for CVE-2023-34362, which was exploited as a zero-day by the Clop ransomware gang in knowledge theft attacks. Kroll explained it observed evidence that the group, dubbed Lace Tempest by Microsoft, had been tests the exploit as significantly back as July 2021.
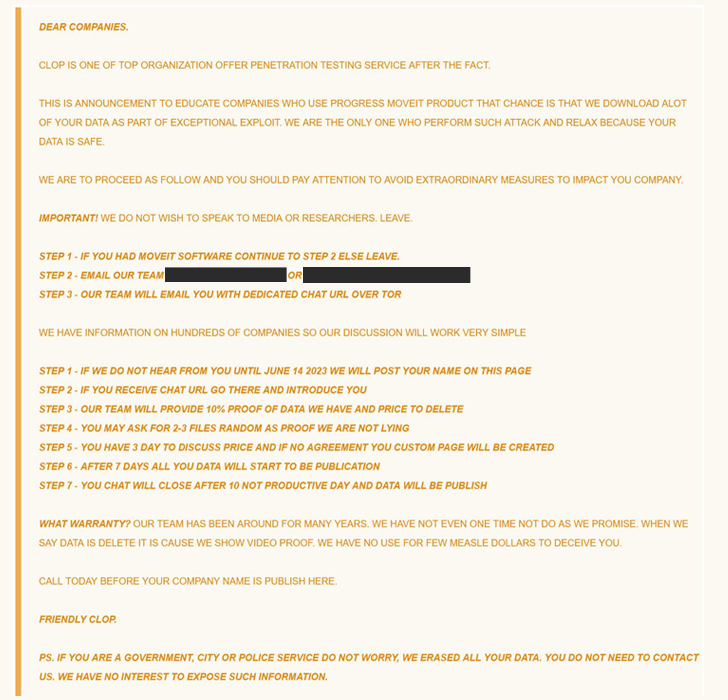
The progress also coincides with the Cl0p actors listing the names of 27 corporations that it claimed were being hacked making use of the MOVEit Transfer flaw on its darknet leak portal. According to a report from CNN, this also incorporates multiple U.S. federal organizations these as the Office of Electricity.

“The range of likely breached organizations so far is drastically greater than the first variety named as aspect of Clop’s past MFT exploitation: the Fortra GoAnywhere MFT marketing campaign,” ReliaQuest claimed.
Forthcoming WEBINAR🔐 Mastering API Security: Knowledge Your Correct Attack Surface area
Find out the untapped vulnerabilities in your API ecosystem and consider proactive measures towards ironclad security. Sign up for our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:afterscreen:inline-block.test_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-prime-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:right afterwidth:50pxheight:6pxcontent:”border-top rated:2px sound #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-body weight:900textual content-align:leftline-height:33px.wn-descriptiontext-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
Censys, a web-primarily based lookup platform for examining attack floor for internet-related gadgets, reported approximately 31% of about 1,400 exposed hosts functioning MOVEit are in the fiscal providers sector, 16% in healthcare, 9% in info technology, and 8% in govt and armed forces sectors. Practically 80% of the servers are based in the U.S.
Per Kaspersky’s evaluation of 97 families unfold via the malware-as-a-company (MaaS) enterprise model between 2015 and 2022, ransomware sales opportunities with a 58% share, followed by info stealers (24%) and botnets, loaders, and backdoors (18%).
“Revenue is the root of all evil, like cybercrime,” the Russian cybersecurity corporation said, including the MaaS schemes permit a lot less technically proficient attackers to enter the fray, therefore lowering the bar for carrying out such attacks.
Located this posting interesting? Observe us on Twitter and LinkedIn to browse more exceptional written content we publish.
Some sections of this post are sourced from:
thehackernews.com


 CISA and NSA Publish BMC Hardening Guidelines
CISA and NSA Publish BMC Hardening Guidelines